Security
Working with certificates
12-5
Rules operate on IP datagrams (sometimes called packets). Datagrams are the individual
packages of data that travel on an IP network. Each datagram contains addressing and
control information along with the data it is transporting. The firewall analyses the
addressing and control information to apply the rules you define.
The controller applies the firewall rules in the order that they appear in the list. An intelligent
mechanism automatically adds the new rules to the list based on their scope. Rules that
target a large amount of data are added at the bottom. Rules that target specific datagram
attributes are added at the top.
Working with certificates
The certificate stores provide a repository for managing all certificates (except for those used
by IPSec and NOC authentication). To view the certificate stores, select Controller >>
Security > Certificate stores.
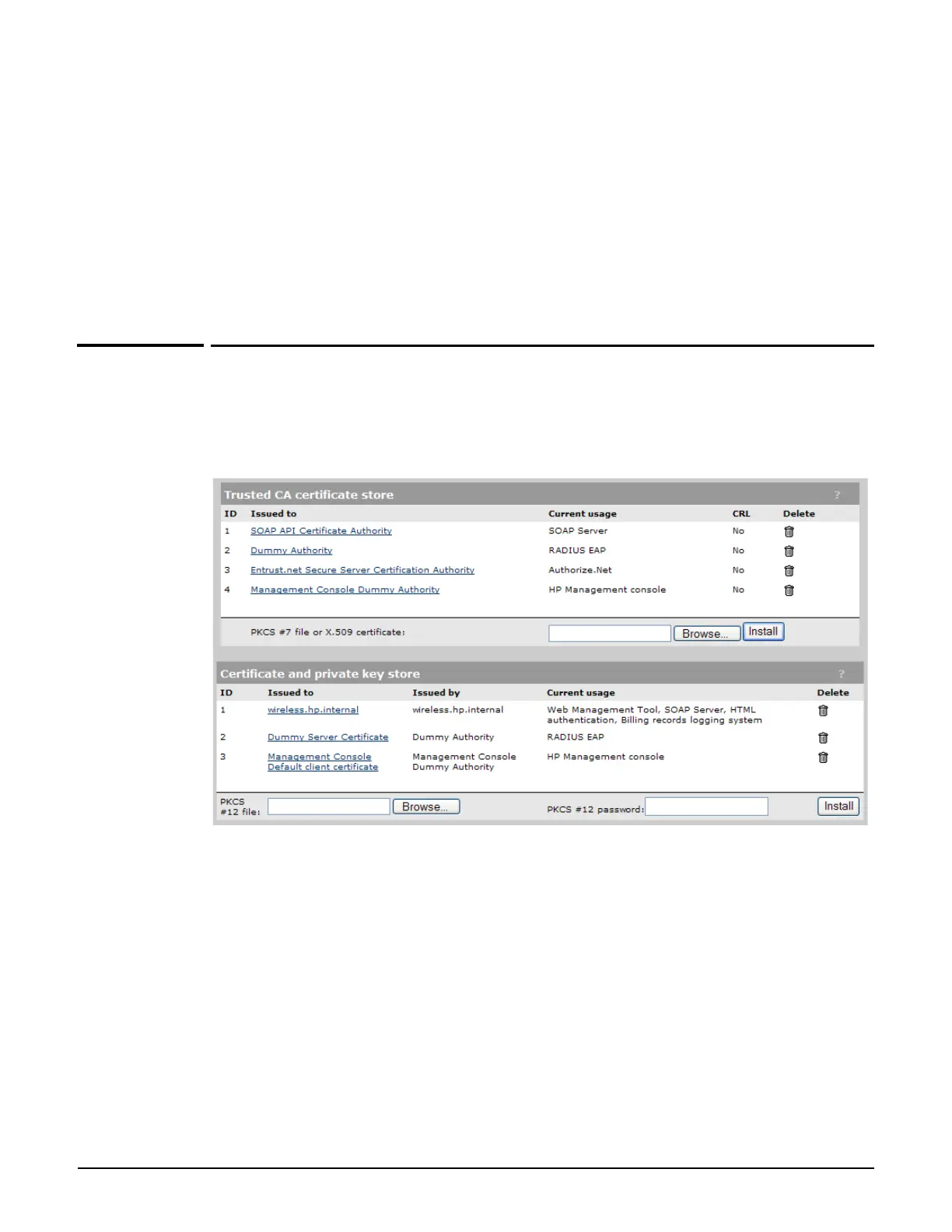
Trusted CA certificate store
This list displays all root CA (certificate authority) certificates installed on the controller. The
controller uses these CA certificates to validate the certificates supplied by client stations
during authentication. Multiple CA certificates can be installed to support validation of
clients with certificates issued by different CAs.

 Loading...
Loading...