Working with VSCs
VSC data flow
5-34
Features
Authentication: The controller supports 802.1X, MAC, or HTML authentication. To
validate user login credentials the controller can use the local user accounts or make use
of third-party authentication servers (Active Directory and/or RADIUS). See Chapter 10:
User authentication, accounts, and addressing.
Access control features: The controller provides a number of features that can be
applied to user sessions. Features can be enabled globally or on a per-account basis. See
Account profiles on page 10-27.
Egress
The controller enables user traffic to be forwarded to different output interfaces, which
include the routing table, VLAN ID, or GRE tunnel. See VSC egress mapping on page 5-17.
Access control disabled
This diagram shows traffic flow when a non-access-controlled VSC is bound to an AP.
VSC on controlled AP
Ingress
The AP only handles traffic from wireless users, except for the MSM317 which can handle
traffic from both wireless and wired users. The SSID is the name of the wireless network with
which the user associates
Features
Authentication: The AP supports 802.1X or MAC authentication. To validate user login
credentials the AP makes use of a third-party authentication server (controller or third-
party RADIUS server). See Chapter 10: User authentication, accounts, and addressing.
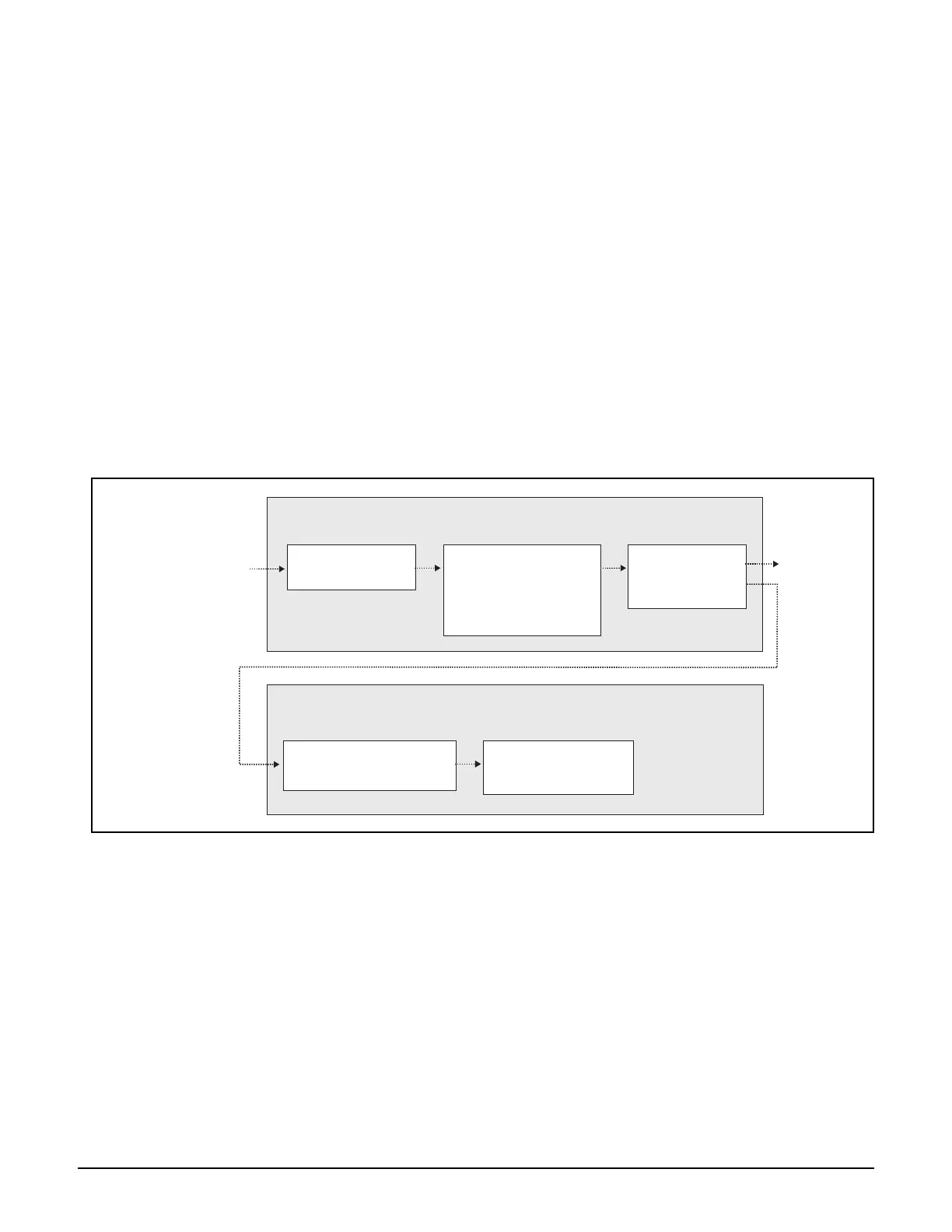
VSC on controlled AP
Ingress
- SSID (from association)
Features
-
- Authentication (MAC, 802.1X)
- Wireless security filters
- Wireless MAC filter
Wireless IP filter
Wireless traffic
VSC on controller
Ingress
- SSID (from RADIUS auth request)
Features
- Authentication (MAC, 802.1X)
Authentication
traffic
Egress
- Bridged onto port 1+2
- VLAN
User traffic

 Loading...
Loading...