User authentication, accounts, and addressing
802.1X authentication
10-9
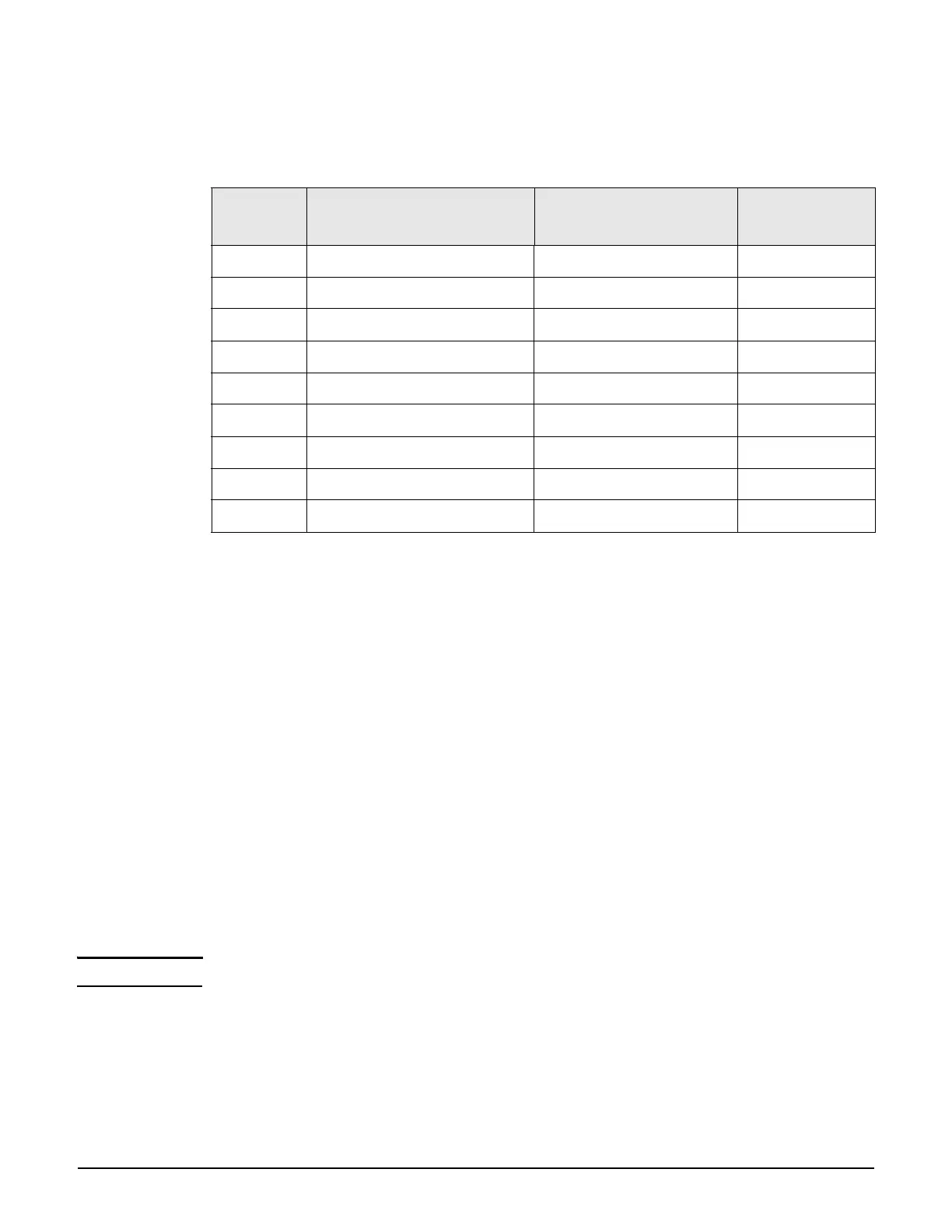
Supported 802.1X protocols
The following table lists the 802.1X protocols supported by the internal RADIUS server on the
controller, and when using a third-party RADIUS server.
The EAP protocols in this table are known to work with the controller. Other EAP protocols
may also work but have not been tested.
Protocol definitions
The following are brief definitions for the supported protocols. For more detailed
information, see the appropriate RFC for each protocol.
EAP-MD5: Extensible Authentication Protocol Message Digest 5. Offers minimum
security. Not recommended.
EAP-TLS: Extensible Authentication Protocol Transport Layer Security. Provides strong
security based on mutual authentication. Requires both client and server-side
certificates.
EAP-TTLS: Extensible Authentication Protocol Tunnelled Transport Layer Security.
Provides excellent security with less overhead than TLS as client-side certificates can be
used, but are not required.
LEAP: Lightweight Extensible Authentication Protocol. Provides mutual authentication
between a wireless client and the RADIUS server. Supports WEP, TKIP, and WPA2 keys.
Note LEAP is not supported on access-controlled VSCs.
PEAPv0: Protected Extensible Authentication Protocol. One of the most supported
implementations across all client platforms. Uses MSCHAPv2 as the inner protocol.
PEAPv1: Protected Extensible Authentication Protocol. Alternative to PEAPv0 that
permits other inner protocols to be used.
Protocol
Local user accounts (via
Internal RADIUS server)
Third-party
RADIUS server
Certificates
required
EAP-MD5 ✕✔No
EAP-TLS ✔✔Client and Server
EAP-TTLS ✔✔Server
LEAP ✕✔No
PEAPv0 ✔✔Server
PEAPv1 ✕✔Server
EAP-FAST ✕✔Optional
EAP-SIM ✕✔Server
EAP-AKA ✕✔Server
 Loading...
Loading...