Working with RADIUS attributes
Colubris AV-Pair - Site attribute values
15-35
Default setting
By default no access lists are defined. This means that:
If authentication (802.1X, WPA, HTML, MAC) is not enabled on a VSC, all users that
connect to the VSC have access to the protected network.
If authentication (802.1X, WPA, HTML, MAC) is enabled on a VSC, then:
Unauthenticated users only reach the public access login page. Access to the
protected network is blocked, except for register.procurve.com which enables
product registration.
Authenticated users have access to the protected network.
How the access lists work
Access lists can be applied on the controller (site access lists), in which case they affect all
user traffic, or individually for each user account (user access lists).
Incoming traffic cascades through the currently active lists. Traffic that is accepted or denied
by a list is not available to the list that follows it. Traffic that passes through all lists without
being accepted or denied is dropped.
Access list rules that accept traffic are: ACCEPT, ACCEPT-MORE, DNAT-SERVER, and
REDIRECT.
Access list rules that deny traffic are: DENY and WARN.
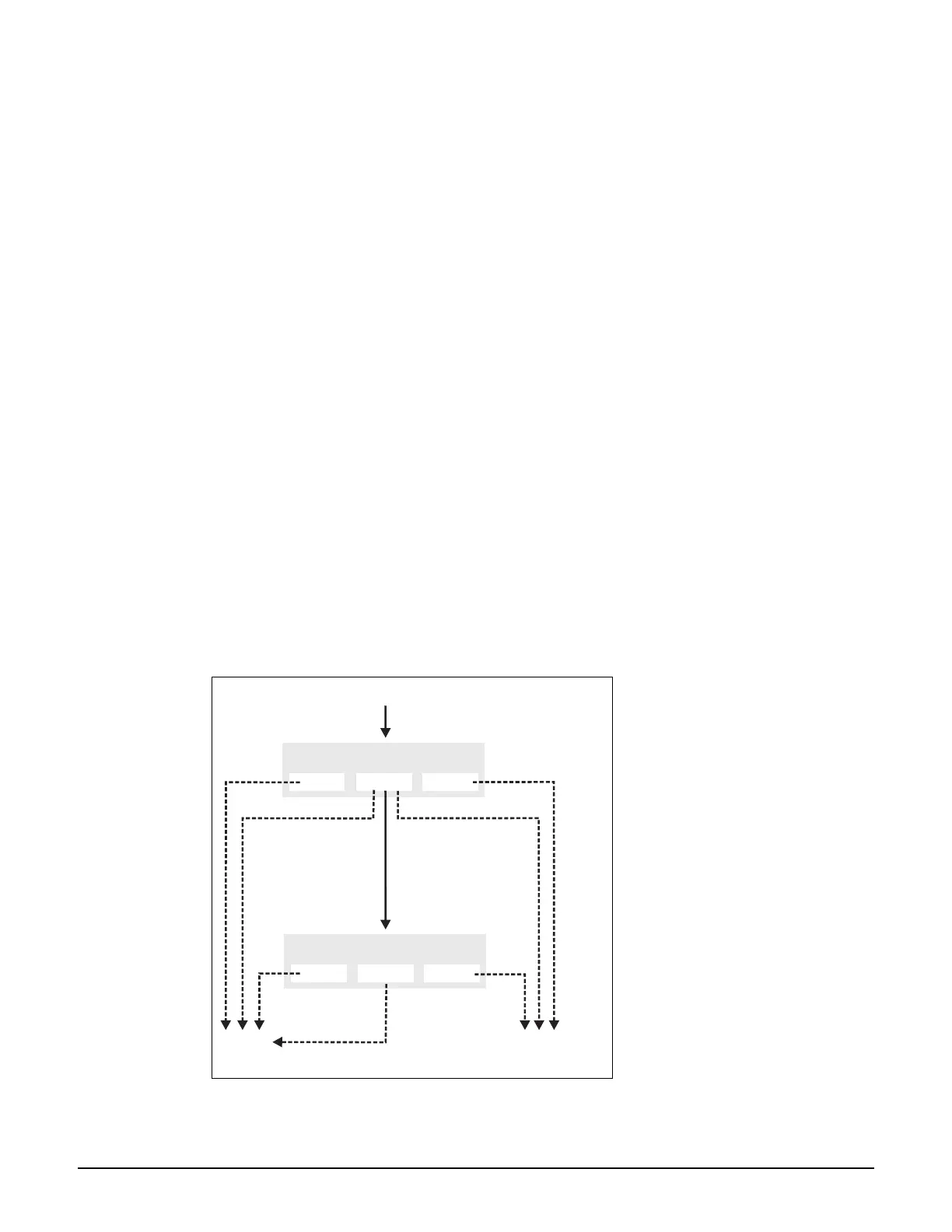
The following diagram illustrates how incoming traffic from a user session is processed by
the access list mechanism.
Incoming user traffic
Service Controller Access List
DENY
NO MATCH ACCEPT
User Access List
DENY
NO MATCH ACCEPT
Authenticated and
a user access
list exists
Authenticated and
no user access list
exists
Unauthenticated
To protected network
via the Internet port
Dropped
 Loading...
Loading...