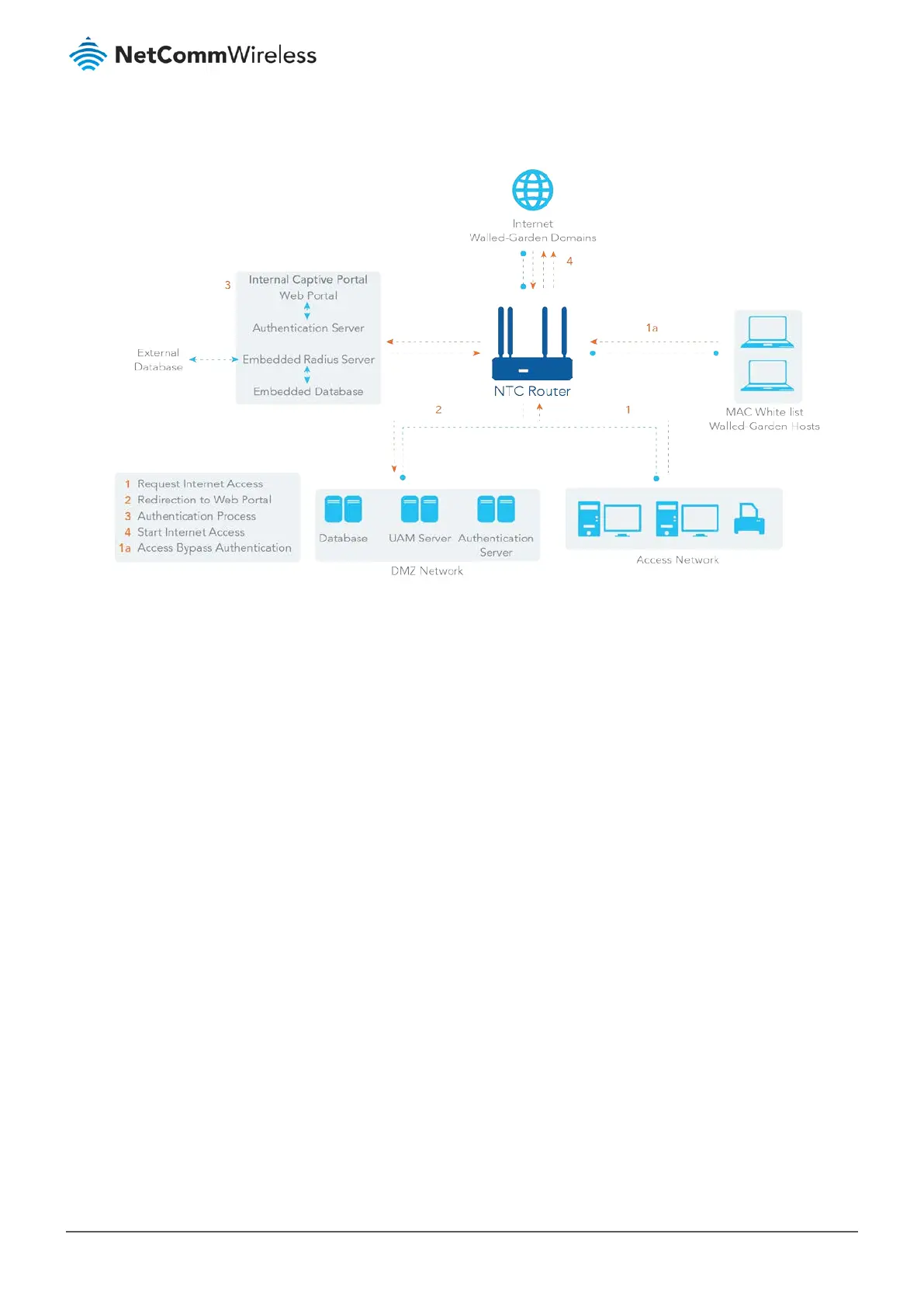
Internal Captive Portal
Figure 305 – Internal Captive Portal
In contrast, for an internal captive portal, you will only select “Internal RADIUS Server” option for user authentication. The
user account database can be an embedded database, an external AD database or an external LDAP database. However, the
UAM server is not necessary for this case and that the captive portal Web site is embedded in the device.
Before enabling the internal Captive Portal function, Go to [Object Definition]-[External Server] to define external server
objects, like LDAP server or AD server if necessary. Return to this page to configure the Captive Portal function for a specific
WAN Interface. Select the “Internal RADIUS Server” option for user authentication and specify its user database to be the
embedded one, an external LDAP server or an external AD server from the pre-defined external server object list.
Note – All Internet Packets will be forwarded to the Captive Portal page of the router when the Captive portal feature is enabled.
Please make sure that at least one user account is created.
When the user authentication process completes successfully, the router redirects the web page to the requested one. The
router also records the MAC address of the guest client host and allows its incoming Internet access requests.
Each account has its own lease time and it will not be reused for authentication once the lease time has run out. The client
host with that account will be rejected to access the Internet. However, there is a timeout setting for each account. When
the client host with that account has been idle the timeout setting, the router will re-authenticate the client host for further
Internet connections.
 Loading...
Loading...