Operation Manual – Port Security-Port Binding
H3C S3100 Series Ethernet Switches Chapter 1 Port Security Configuration
1-3
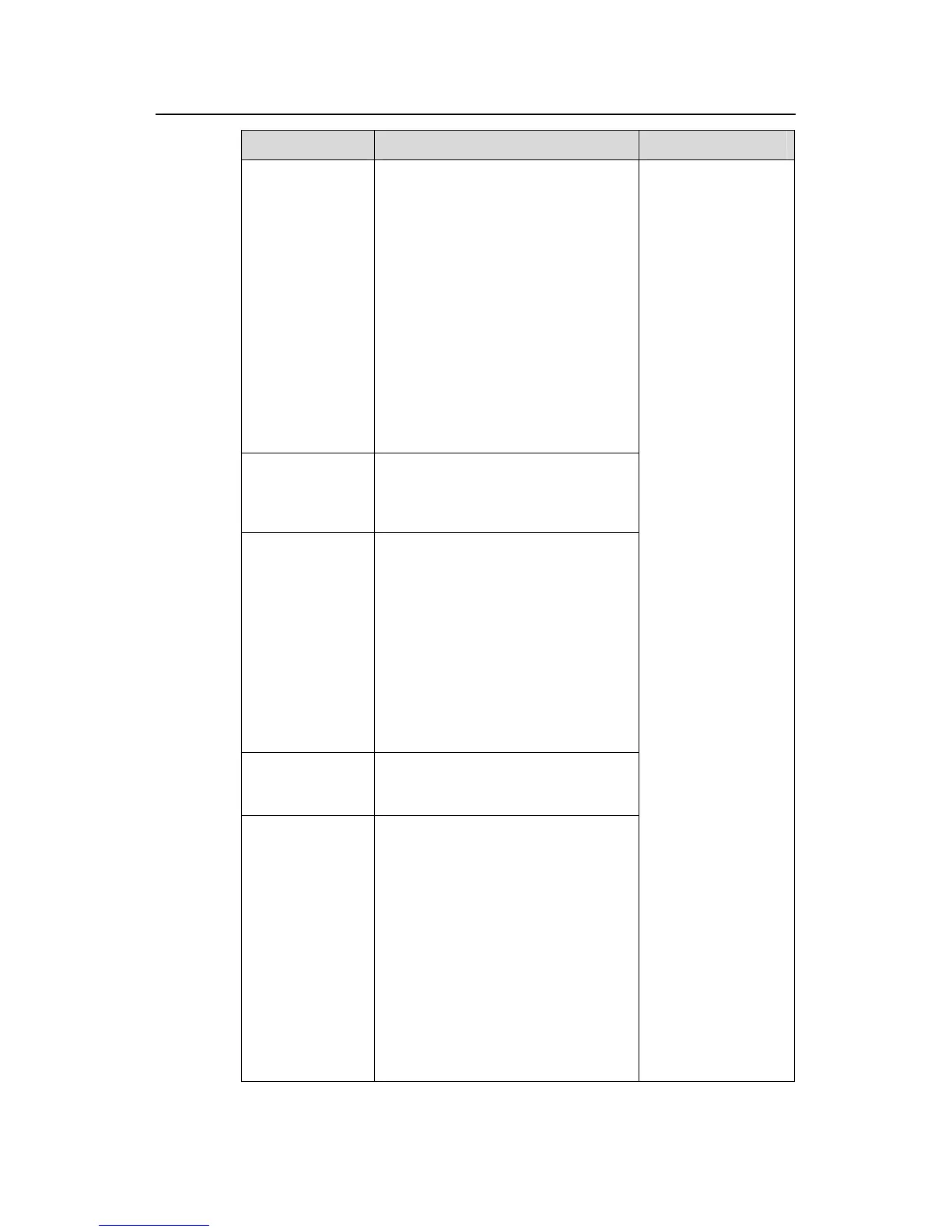
Security mode Description Feature
userLoginSecur
e
MAC-based 802.1x authentication is
performed on the access user. The
port is enabled only after the
authentication succeeds. When the
port is enabled, only the packets of the
successfully authenticated user can
pass through the port.
In this mode, only one
802.1x-authenticated user is allowed
to access the port.
When the port changes from the
noRestriction mode to this security
mode, the system automatically
removes the existing dynamic MAC
address entries and authenticated
MAC address entries on the port.
userLoginSecur
eExt
This mode is similar to the
userLoginSecure mode, except that
there can be more than one
802.1x-authenticated user on the port.
userLoginWithO
UI
This mode is similar to the
userLoginSecure mode, except that,
besides the packets of the single
802.1x-authenticated user, the
packets whose source MAC
addresses have a particular OUI are
also allowed to pass through the port.
When the port changes from the
normal mode to this security mode, the
system automatically removes the
existing dynamic/authenticated MAC
address entries on the port.
macAddressWit
hRadius
In this mode, MAC address–based
authentication is performed for access
users.
macAddressOrU
serLoginSecure
In this mode, both MAC authentication
and 802.1x authentication can be
performed, but 802.1x authentication
has a higher priority.
802.1x authentication can still be
performed on an access user who has
passed MAC authentication.
No MAC authentication is performed
on an access user who has passed
802.1x authentication.
In this mode, there can be only one
802.1x-authenticated user on the port,
but there can be several
MAC-authenticated users.
In any of these
modes, the device
triggers the NTK and
Intrusion Protection
features upon
detecting an illegal
packet or illegal
event.

 Loading...
Loading...