Configuration Guide 60
Managing System Access Security Configurations
Key File Select the desired Key to download to the switch. The key must be BASE64
encoded. The SSL certificate and key downloaded must match each other,
otherwise the HTTPS connection will not work.
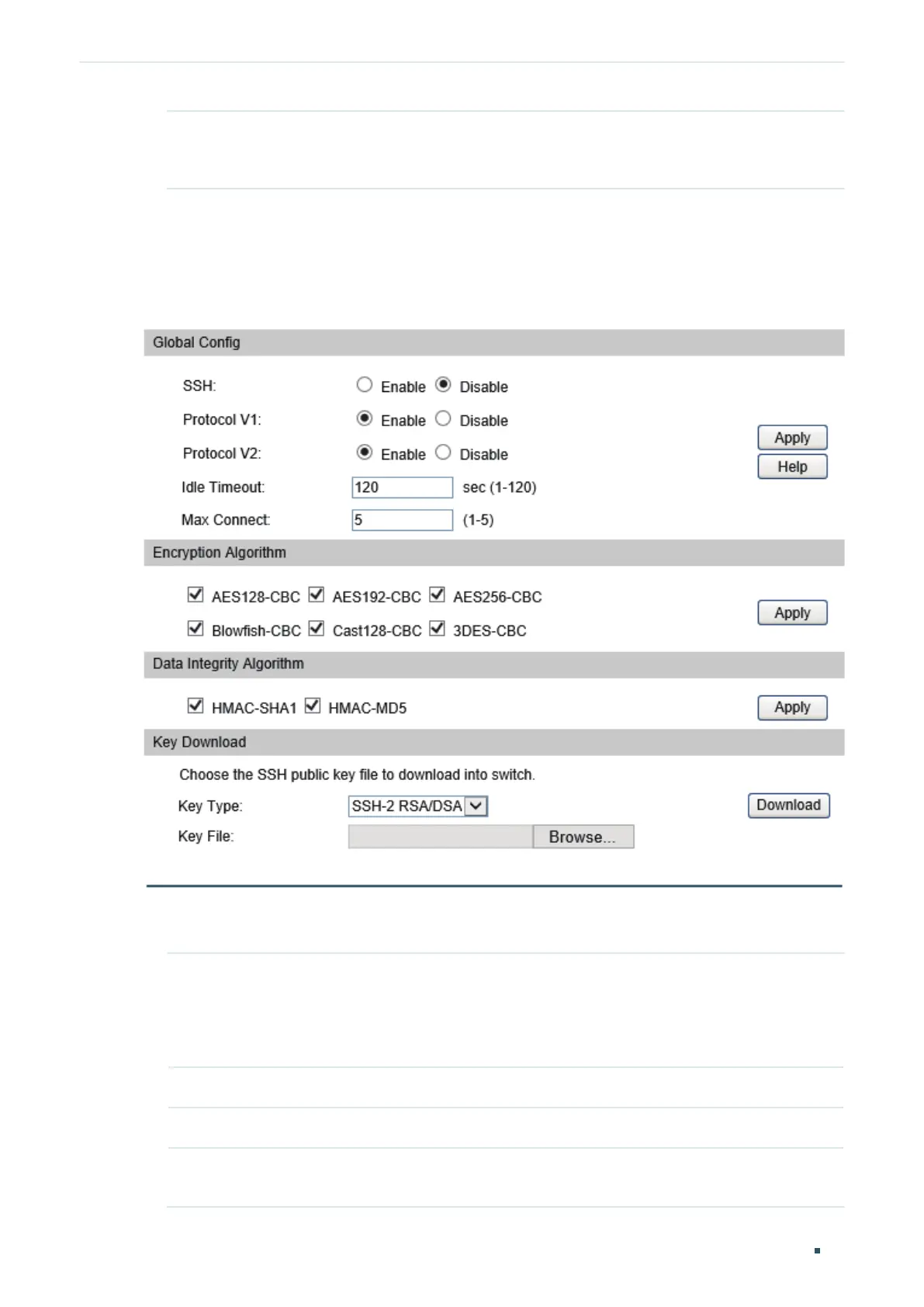
5.1.4 Configuring the SSH Feature
Choose the menu System > Access Security > SSH Config to load the following page.
Figure 5-3 Configuring the SSH Feature
1) In the Global Config section, select Enable to enable SSH function and specify other
parameters.
SSH Select Enable to enable the SSH function.
SSH is a protocol working in application layer and transport layer. It can provide a
secure, remote connection to a device. It is more secure than Telnet protocol as it
provides strong encryption.
Protocol V1 Select Enable to enable SSH version 1.
Protocol V2 Select Enable to enable SSH version 2.
Idle Timeout Specify the idle timeout time. The system will automatically release the
connection when the time is up.
 Loading...
Loading...











