Control Register 4 (CR4) Extensions 3-23
18524C/0—Nov1996 AMD-K5 Processor Technical Reference Manual
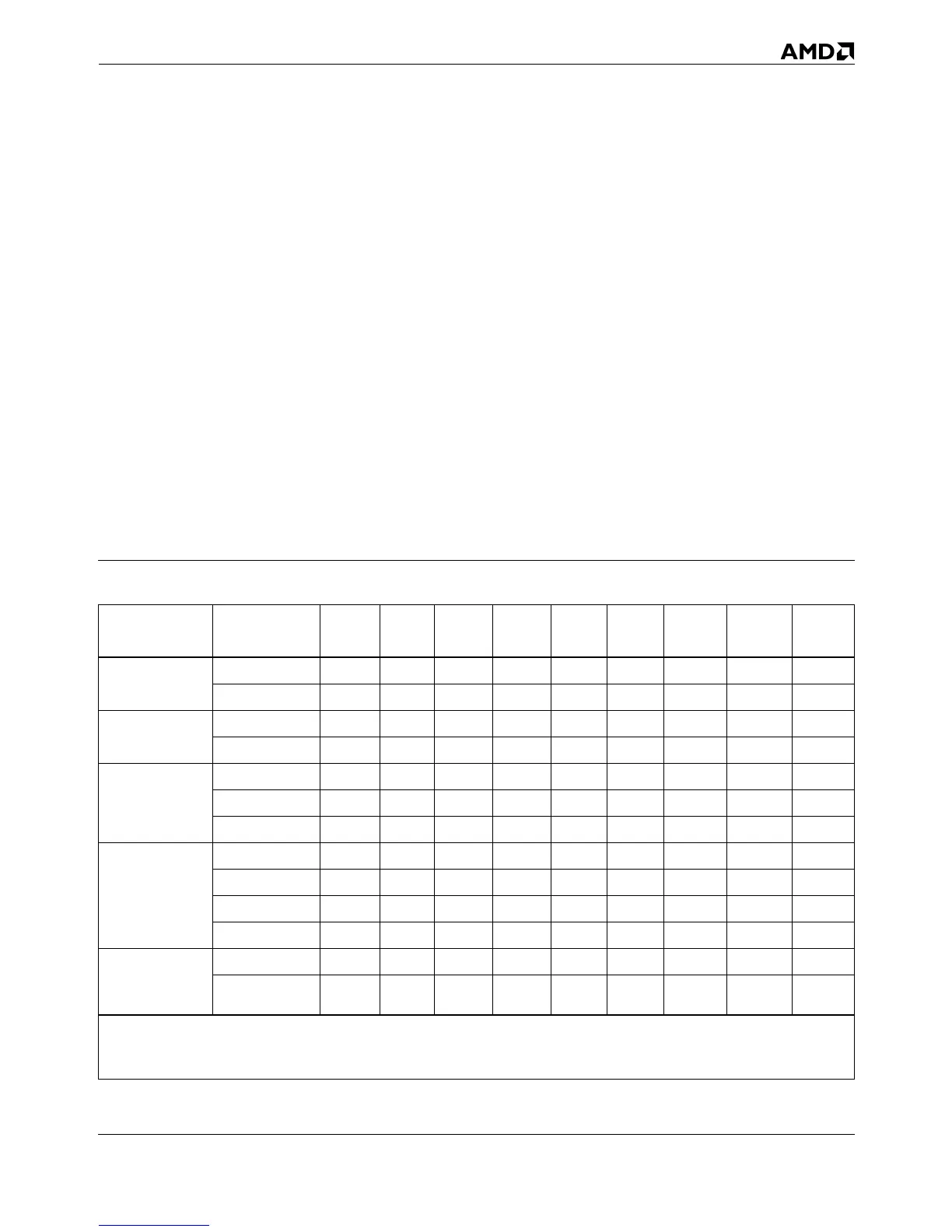
Table 3-6 compares the behavior of hardware and software
interrupts in various x86-processor operating modes. It also
shows which interrupt table is accessed: the Protected-mode
IDT or the Real- and Virtual-8086-mode IVT. The column head-
ings in this table include:
■ PE—Protection Enable bit in CR0 (bit 0)
■ VM—Virtual-8086 Mode bit in EFLAGS (bit 17)
■ VME—Virtual Mode Extensions bit in CR4 (bit 0)
■ PVI—Protected-Mode Virtual Interrupts bit in CR4 (bit 1)
■ IOPL—I/O Privilege Level bits in EFLAGS (bits 13–12)
■ IRB—Interrupt Redirection Bit for a task, from the Inter-
rupt Redirection Bitmap (IRB) in the tasks TSS
■ GP(0)—General-protection exception, with error code = 0
■ IDT—Protected-Mode Interrupt Descriptor Table
■ IVT—Real- and Virtual-8086 Mode Interrupt Vector Table
Table 3-6. Interrupt Behavior and Interrupt-Table Access
Mode
Interrupt
Type
PE VM VME PVI IOPL IRB GP(0) IDT IVT
Real mode
Software 0 0 0 —0—— —✓
Hardware 0 0 0 — 0 — — — ✓
Protected mode
Software 1 0 0 — — — — ✓ —
Hardware 1 0 0 — — — — ✓ —
Virtual-8086
mode
1
Software 1 1 0 — = 3— No ✓ —
Software 1 1 0 — < 3— Yes ✓ —
Hardware 1 1 0 — — — No ✓ —
Virtual-8086
Mode Exten-
sions (VME)
1
Software 1 1 1 0 — 0 No — ✓
Software 1 1 1 0 = 31 No ✓ —
Software 1 1 1 0 < 31 Yes ✓ —
Hardware 1 1 1 0 — — No ✓ —
Protected Vir-
tual Extensions
(PVI)
Software 1 0 1 1 — — No ✓ —
Hardware 1 0 1 1 — — No ✓ —
Notes:
1. All Virtual-8086 tasks run at CPL = 3.
— Not applicable.
 Loading...
Loading...