Detecting and Preventing Wireless Intrusion
D-Link Unified Wired and Wireless Access System
Oct. 2015 Page 730
D-Link UWS User Manual
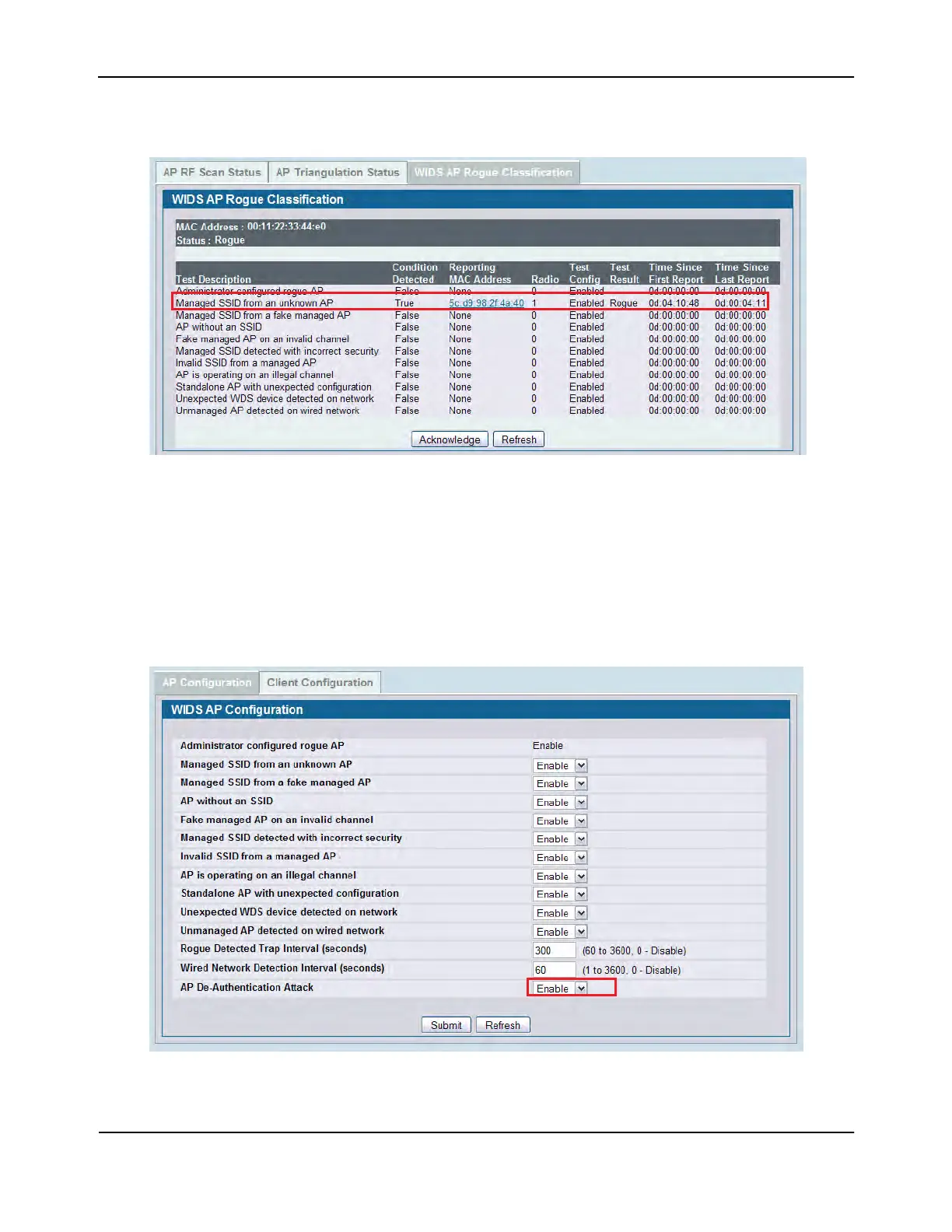
Click the WIDS AP Rogue Classification tab to learn which WIDS test triggered the rogue status.
Figure 446: WIDS Test Discovers Rogue
As Figure 446 shows, the honeypot AP is identified as a rogue because it triggered the Managed SSID from an
unknown AP test. In other words, the honeypot AP, which is an unknown AP to the company, is using the same
SSID as the legitimate AP inside the building.
At this point, no further action is taken by the DWS-4000 Series switch because the AP deauthentication attack
feature is disabled. To enable the AP to take further action, enable the AP De-Authentication Attack option on
the WLAN > Administration > Advanced Configuration > WIDS Security tab.
Figure 447: De-Authentication Attack Enabled

 Loading...
Loading...











