Virtual PrivateNetworks(VPN) IPsec
IX20 User Guide
486
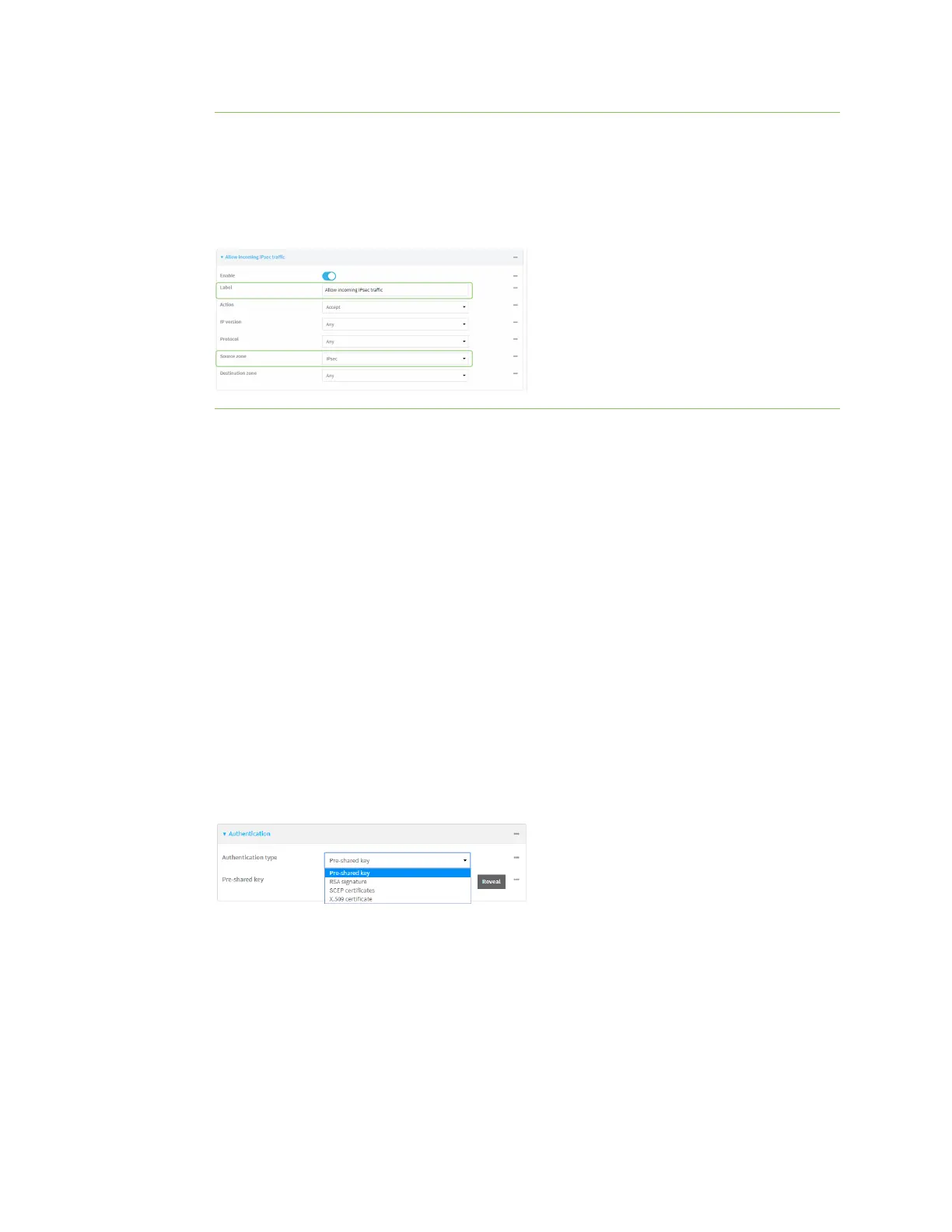
a. Click to expand Firewall >Packet filtering.
b. For Add packet filter, click .
c. For Label, type Allow incoming IPsec traffic.
d. For Source zone, select IPsec.
Leaveall other fieldsat their default settings.
10. For Metric, enter or select the priority of routes associated with this IPsec tunnel. When more
than one active route matches a destination, the route with the lowest metric is used.
The metric can also be used in tandem with SureLink to configure IPsec failover behavior. See
Configure IPsec failover for more information.
11. For Mode, select Tunnel mode. Transport mode is not currently supported.
12. Select the Mode, either:
n
Tunnel mode: Theentire IPpacket is encrypted and/or authenticated and then
encapsulated as the payload in a new IPpacket.
n
Transport mode: Only the payload of the IPpacket is encrypted and/or authenticated.
The IPheader is unencrypted.
13. Select the Protocol, either:
n
ESP (Encapsulating Security Payload): Providesencryption as well as authentication
and integrity.
n
AH (Authentication Header): Providesauthentication and integrity only.
14. Strict routingis disabled by default. Toggle on to enable.
Strict routing makes IPsec behave like a policy-based VPN, rather than aroute-based VPN.
15. Click to expand Authentication.
a. For Authentication type, select one of the following:
n
Pre-shared key: Uses a pre-shared key (PSK) to authenticate with the remote peer.
i. Typethe Pre-shared key.
n
Asymmetric pre-shared keys: Usesasymmetric pre-shared keys to authenticate
with the remote peer.
i. For Local key, type the local pre-shared key. This must be the same as the
remote key on the remote host.

 Loading...
Loading...