User authentication User authentication methods
IX20 User Guide
865
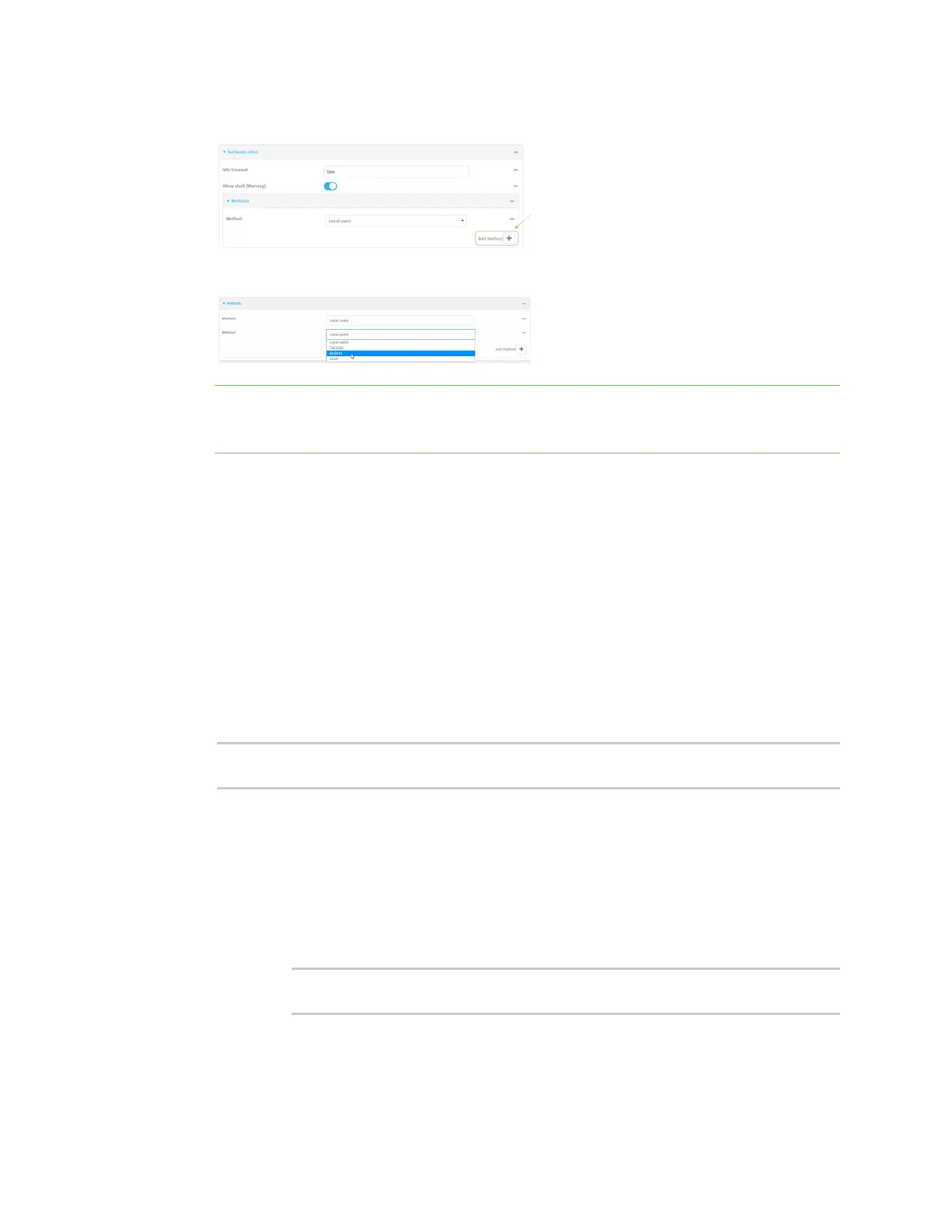
4. For Add Method, click .
5. Select the appropriate authentication type for the new method from the Method drop-down.
Note Authentication methodsare attempted in the order they are listed until the first
successful authentication result isreturned. See Rearrange the position of authentication
methodsfor information about how to reorder the authentication methods.
6. Repeat these steps to add additional methods.
7. Click Apply to savethe configuration and apply the change.
Command line
Authentication methodsare attempted in the order they are listed until the first successful
authentication result is returned. This procedure describes how to add methodsto variousplacesin
the list.
1. Select the device in Remote Manager and click Actions> Open Console, or log into the IX20
local command line as a user with full Admin access rights.
Depending on your device configuration, you may be presented with an Access selection
menu. Type admin to accessthe Admin CLI.
2. At the command line, type config to enter configuration mode:
> config
(config)>
3. Add the new authentication method to the appropriate location in the list:
n
To determine the current list of authentication methods:
a. Select the device in Remote Manager and click Actions>Open Console, or log into
the IX20 local command line as a user with full Admin accessrights.
Depending on your device configuration, you may be presented with an Access
selection menu. Type admin to access the Admin CLI.
b. At the command line, type config to enter configuration mode:
> config
(config)>
c. Use the show auth method command to display the current authentication
methodsconfiguration:
 Loading...
Loading...