User authentication Terminal AccessController Access-Control System Plus(TACACS+)
IX20 User Guide
898
c. (Optional) Change the default Port setting to the appropriate port. Normally this should be
left at the default setting of port 49.
d. For Secret, type the TACACS+server's shared secret. Thisis configured in the key
parameter of the TACACS+server'stac_plus.conf file, for example:
key = testing123
Note DAL authentication doesnot support the use of the # character in the key (e.g.,
DAL#123;&). If included, the server will be unable to decipher the request.
e. (Optional) Click again to add additional TACACS+servers.
5. (Optional) Enable Authoritative to prevent other authentication methodsfrom being
attempted if TACACS+login fails.
6. (Optional) For Group attribute, typethe name of the attribute used in the TACACS+ server's
configuration to identify the IX20 authentication group or groupsthat the user is a member of.
For example, in TACACS+ user configuration, the group attribute in the sample tac_plus.conf
file is groupname, which is also the default setting in the IX20 configuration.
7. (Optional) For Service, type the value of the service attribute in the the TACACS+server's
configuration. For example, in TACACS+ user configuration, the value of the service attribute in
the sample tac_plus.conf file is system, which is also the default setting in the IX20
configuration.
8. (Optional) Enable Command authorization, which instructs the device to communicate with
the TACACS+server to determine if the user is authorized to execute a specific command. Only
the first configured TACACS+ server will be used for command authorization.
9. (Optional) Enable Command accounting, which instructs the device to communicate with the
TACACS+server to log commandsthat the user executes. Only the first configured TACACS+
server will be used for command accounting.
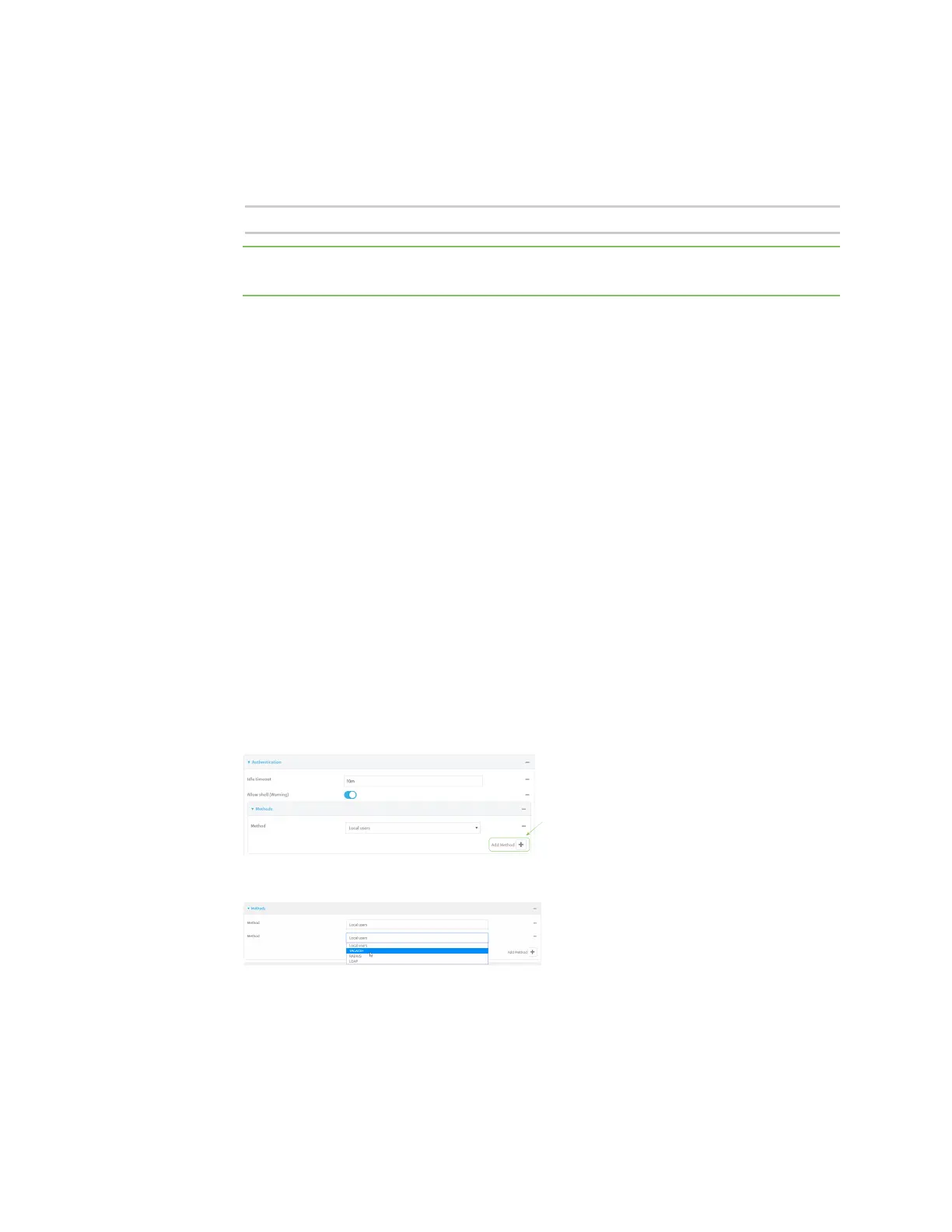
10. Add TACACS+to the authentication methods:
a. Click Authentication > Methods.
b. For Add method, click .
c. Select TACACS+ for the new method from the Method drop-down.
Authentication methodsare attempted in the order they are listed until an authentication
response, either passor fail, isreceived. If Authoritative is enabled (see above), non-
authoritative methodsare not attempted. See Rearrange the position of authentication
methodsfor information about rearranging the position of the methodsin the list.

 Loading...
Loading...