Wireless Access Point
Configuring the Wireless AP 229
Using the AP’s Default Certificate
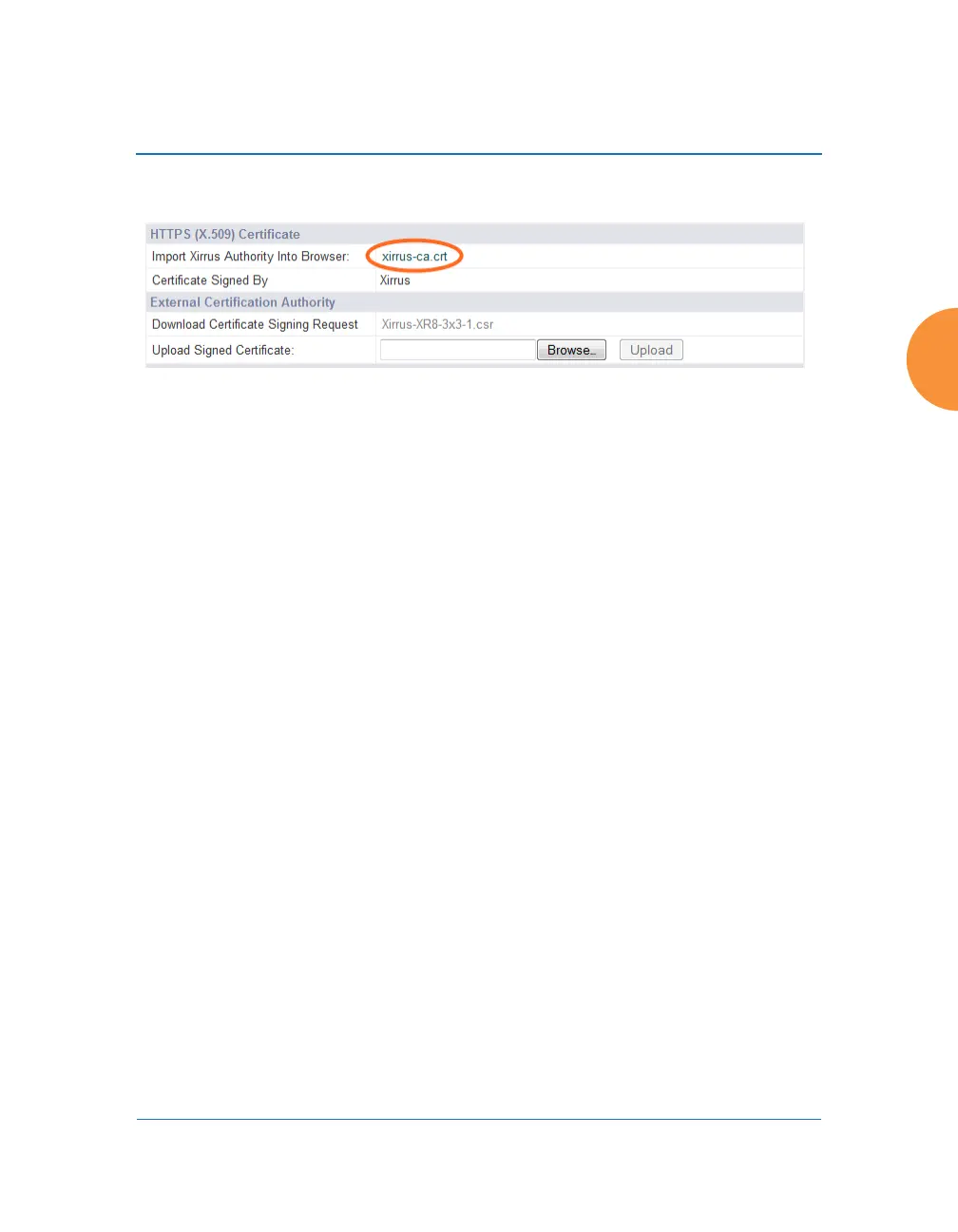
Figure 131. Import Xirrus Certificate Authority
The AP’s certificate is signed by a Xirrus CA that is customized for your AP and
its current host name. By default, browsers will not trust the AP’s certificate. You
may import the Xirrus certificate to instruct the browser to trust the Xirrus CA on
all future connections to APs. The certificate for the Xirrus CA is available on the
AP, so that you can import it into your browser’s cache of trusted CAs (right
alongside VeriSign, for example). On the Management Control window of the
WMI you will see the xirrus-ca.crt file. (Figure 131)
By clicking and opening this file, you can follow your browser’s instructions and
import the Xirrus CA into your CA cache (see “HTTPS (X.509) Certificate” on
page 244 for more information). This instructs your browser to trust any of the
certificates signed by the Xirrus CA, so that when you connect to any of our APs
you should no longer see the warning about an untrusted site. Note however, that
this only works if you use the host name when connecting to the AP. If you use
the IP address to connect, you get a lesser warning saying that the certificate was
only meant for ‘hostname’.
Since an AP’s certificate is based on the AP’s host name, any time you change the
host name the AP’s CA will regenerate and sign a new certificate. This happens
automatically the next time you reboot after changing the host name. If you have
already installed the Xirrus CA on a browser, this new AP certificate should
automatically be trusted.
When you install the Xirrus CA in your browser, it will trust a certificate signed
by any Xirrus AP, as long as you connect using the AP’s host name.

 Loading...
Loading...