Wireless Access Point
597
The pci-audit command checks items such as:
Telnet is disabled.
Admin RADIUS is enabled (admin login authentication is via RADIUS
server).
An external Syslog server is in use.
All SSIDs must set encryption to WPA or better (which also enforces
802.1x authentication)
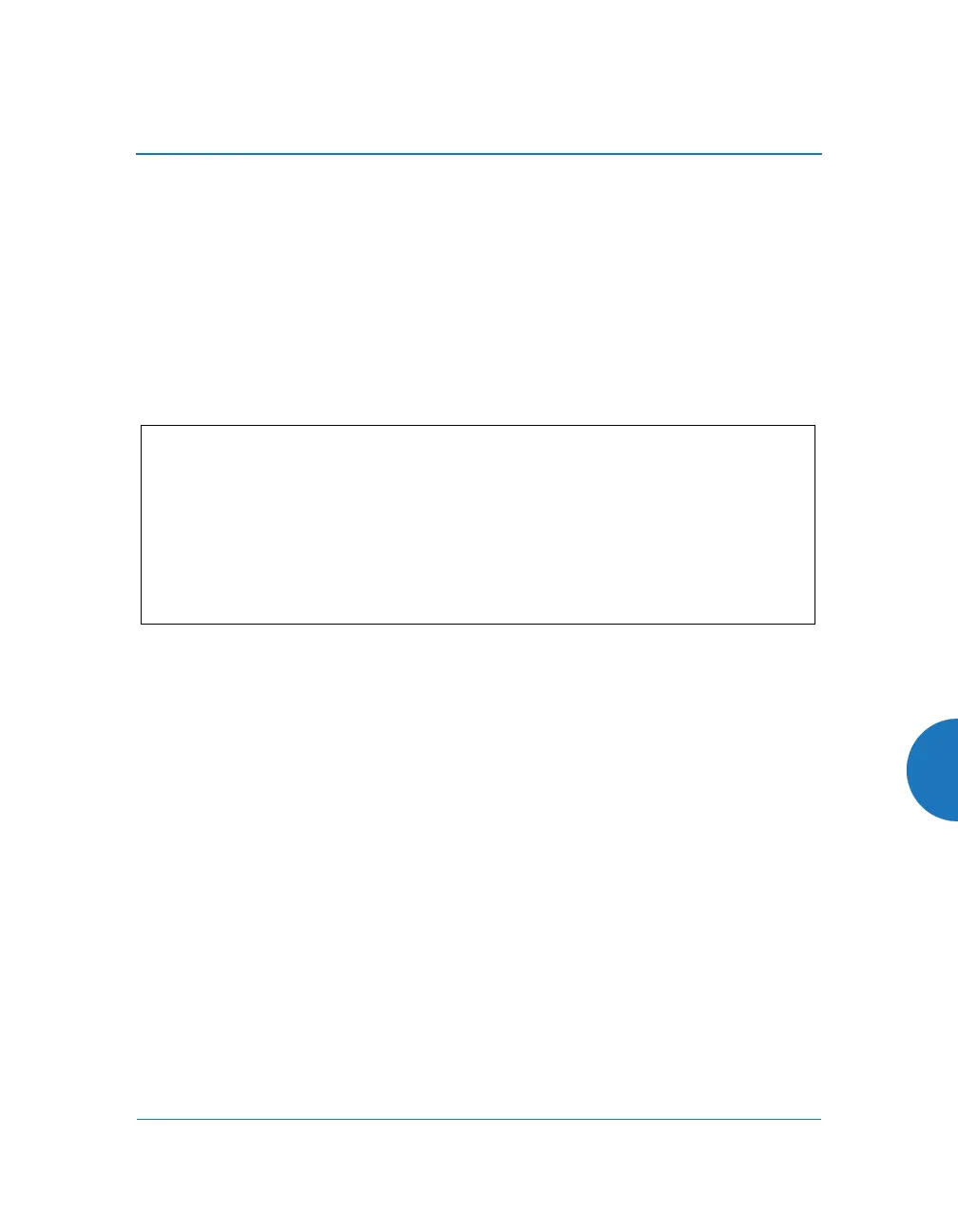
Sample output from this command is shown below.
Figure 228. Sample output of pci-audit command
Additional Resources
PCI Security Standards Web site: www.pcisecuritystandards.org
List of Qualified PCI Security Assessors: www.pcisecuritystandards.org/
pdfs/pci_qsa_list.pdf
SS-AP(config)# pci-audit
PCI audit failure: telnet enabled.
PCI audit failure: admin RADIUS authentication disabled.
PCI audit failure: SSID ssid2 encryption too weak.
PCI audit failure: SSID ssid3 encryption too weak.
PCI audit failure: SSID ssid4 encryption too weak.
PCI audit failure: SSID ssid5 encryption too weak.
PCI audit failure: SSID ssid6 encryption too weak.

 Loading...
Loading...