497
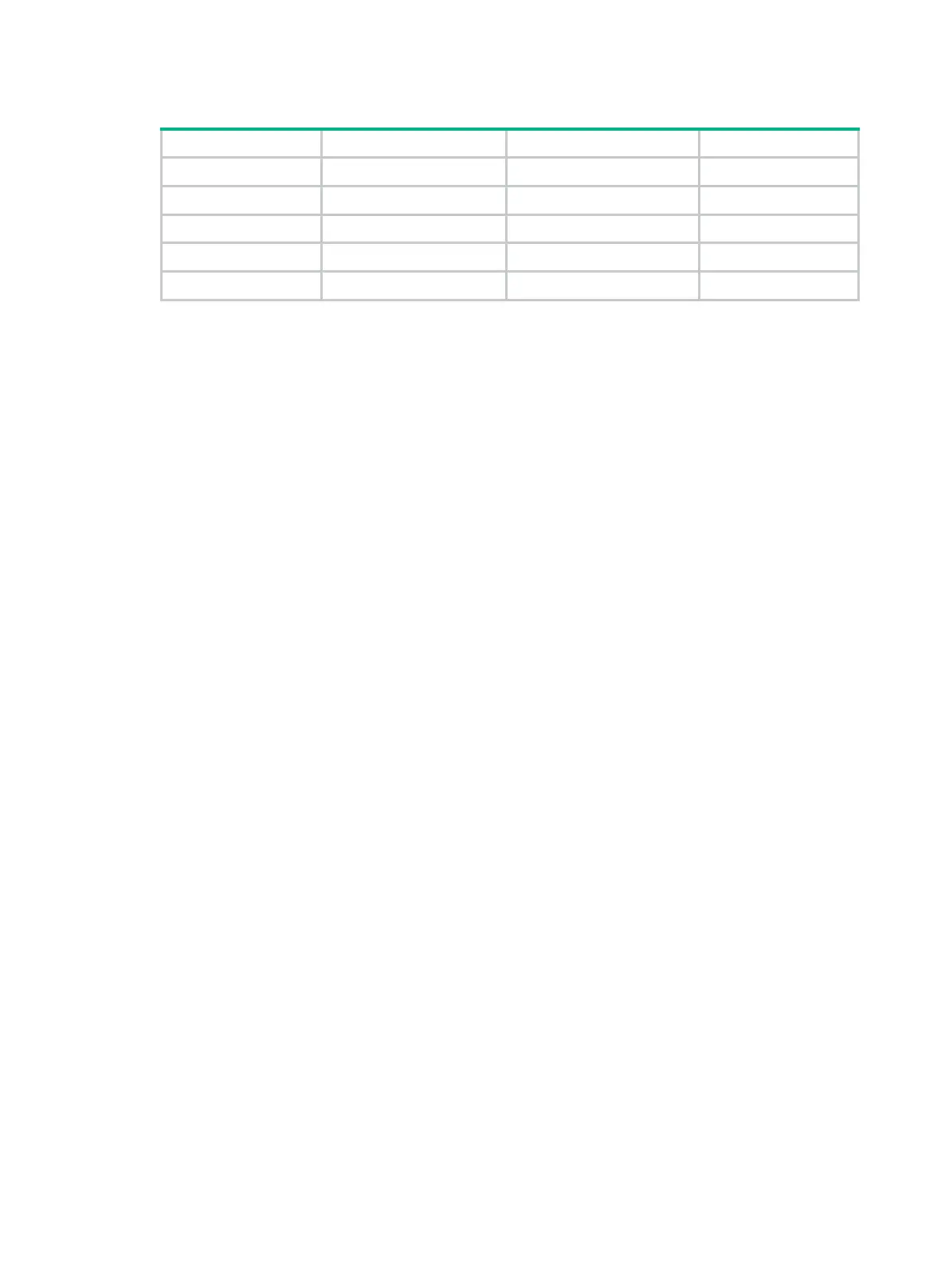
Table 75 Special characters
Tilde ~ Dot .
Asterisk * Left angle bracket <
Backslash \ Right angle bracket >
Vertical bar | Quotation marks "
Colon : Apostrophe '
ca: Specifies the CA certificate.
local: Specifies the local certificates.
Usage guidelines
Generally, certificates are automatically verified when you request, obtain, or import them, or when
an application uses PKI.
You can also use this command to manually verify a certificate in the following aspects:
• Whether the certificate is issued by a trusted CA.
• Whether the certificate has expired.
• Whether the certificate is revoked. This check is performed only if CRL checking is enabled.
When CRL checking is enabled:
• To verify the local certificates, if the PKI domain has no CRLs, the device looks up the locally
saved CRLs. If a correct CRL is found, the device loads the CRL to the PKI domain. If no correct
CRL is found locally, the device obtains a correct CRL from the CA server and saves it locally.
• To verify the CA certificate, CRL checking is performed for the CA certificate chain from the
current CA to the root CA.
Examples
# Verify the validity of the CA certificate in PKI domain aaa.
<Sysname> system-view
[Sysname] pki validate-certificate domain aaa ca
Verifying certificates......
Serial Number:
f6:3c:15:31:fe:bb:ec:94:dc:3d:b9:3a:d9:07:70:e5
Issuer:
C=cn
O=ccc
OU=ppp
CN=rootca
Subject:
C=cn
O=abc
OU=test
CN=aca
Verify result: OK
Verifying certificates......
Serial Number:
5c:72:dc:c4:a5:43:cd:f9:32:b9:c1:90:8f:dd:50:f6

 Loading...
Loading...




