UCM6200 Series User Manual
Version 1.0.20.38
Security Settings
The UCM offers several methods of protection against malicious attacks and unauthorized access such as
firewall rules, connection thresholds, and Fail2ban.
To get started on configuring security settings, navigate to the System Settings->Security Settings page.
Static Defense
On the Static Defense page, users can configure firewall rules and view the ports used by various UCM
services and processes.
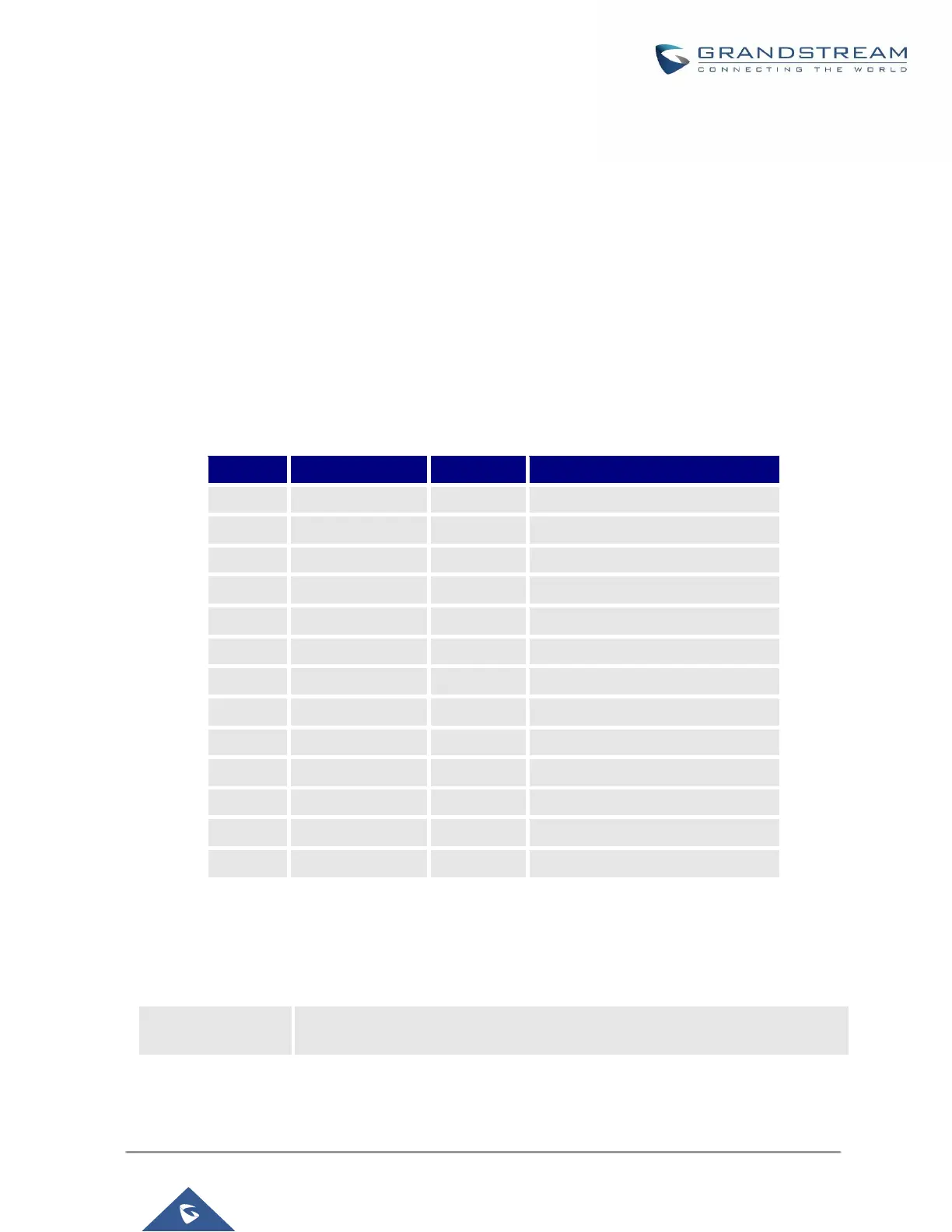
The following table shows a few examples of the information available on the Static Defense page.
Table 12: UCM6200 Firewall→Static Defense→Current Service
UCM6200 zero_config service
UCM6200 zero_config service
For general firewall defense mechanisms, UCM supports Ping Defense, SYN-Flood Defense, and Ping-of-
Death Defense. These can be configured separately for the WAN interface and LAN interface.
Table 13: Typical Firewall Settings
If enabled, the UCM will not send ICMP messages in response to ping requests.

 Loading...
Loading...











