SmartAXIS Touch User’s Manual 21-1
21
User Accounts and the Security Function
This chapter describes user accounts and the Security function, how to configure them, and their operation on the
Touch and in WindO/I-NV3.
1.1 User Accounts
The Security function protects access to data and Touch displays and operations using accounts. Accounts are the
privileges to use the Touch and data. By assigning accounts to users, you can protect the Touch from being
inappropriately operated and protect project data from alterations and misuse.
Accounts assigned to users are called user accounts.
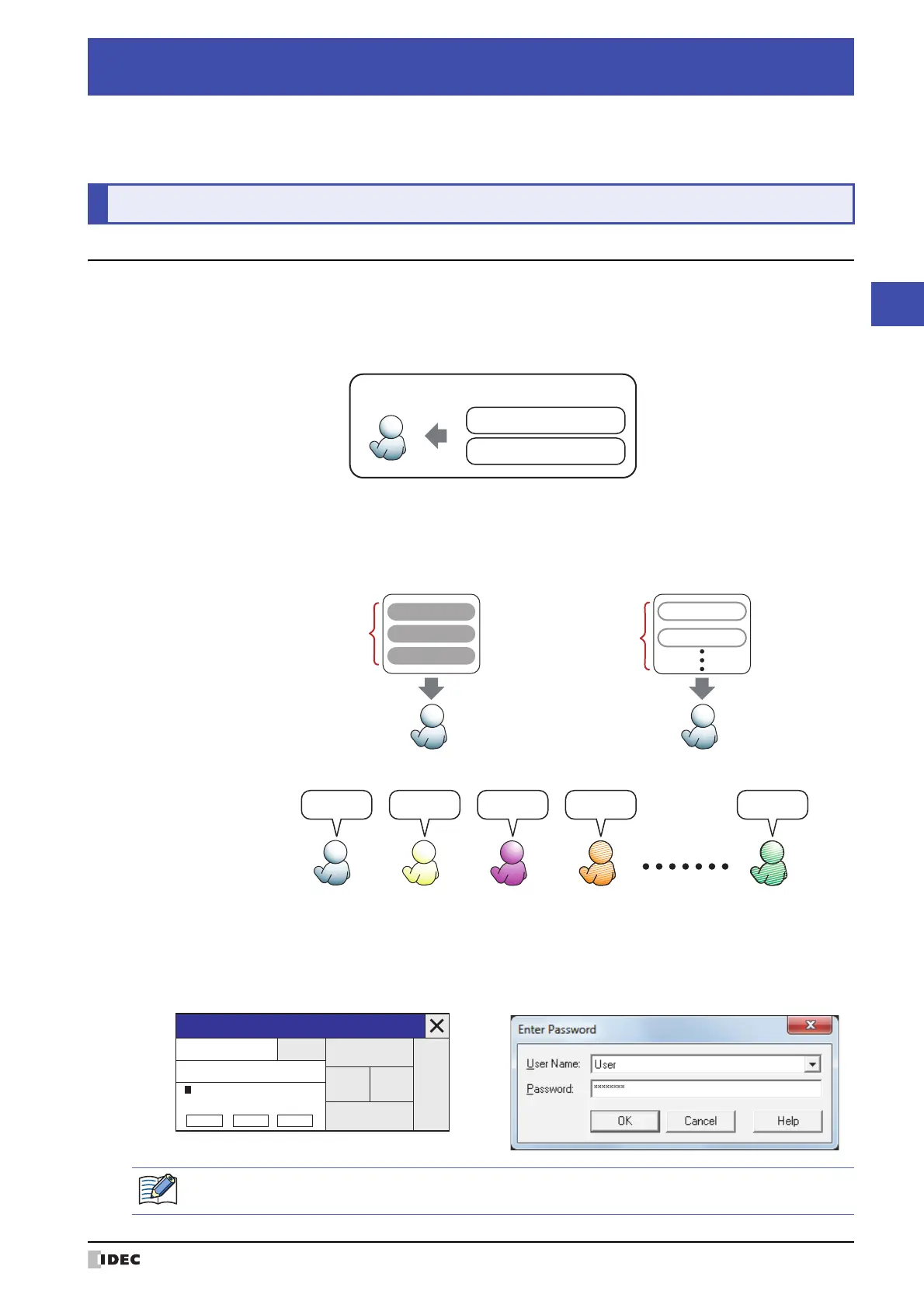
In WindO/I-NV3, security groups are used as accounts.
There are two types of security groups. One type protects access to data. The other type protects Touch displays and
operations. To protect access to data, assign one of the provided security groups to a user. To protect Touch
displays and operations, assign a user-created security group to a user.
A user name and password are associated with a user account and up to 15 user accounts can be created.
If you configure a password for a user account assigned to a security group, access to data and Touch displays and
operations are password protected.
For password protected operations, users are prompted to enter their user name and password as necessary on the
Touch Password screen or the WindO/I-NV3 Enter Password dialog box.
Chapter 21
User Accounts and the Security Function
1Overview
Password screen Enter Password dialog box
User
Assign
Account
User account
Privileges to operate the Touch
Privileges to access data
Assign
Assign
Provided security groups
User-created security
groups (12 max)
Protect displays and operationsProtect data
Administrator
Operator
Reader
GroupA
GroupB
User account: User account:
User4User3 User15User2User1
11111111 22222222 33333333 44444444 EEEEEEEEPassword:
User name:
User account:
Password
ENT
↑
↓
→
←
▼User
********
BS CLR OK
A BCDEFGHI J KLM
NOPQ RS T UVWX Y Z
0123456789
If a password is not configured for a user account, access to data and Touch displays and operations cannot
be protected.

 Loading...
Loading...