C
HAPTER
13
| Security Measures
IPv6 Source Guard
– 404 –
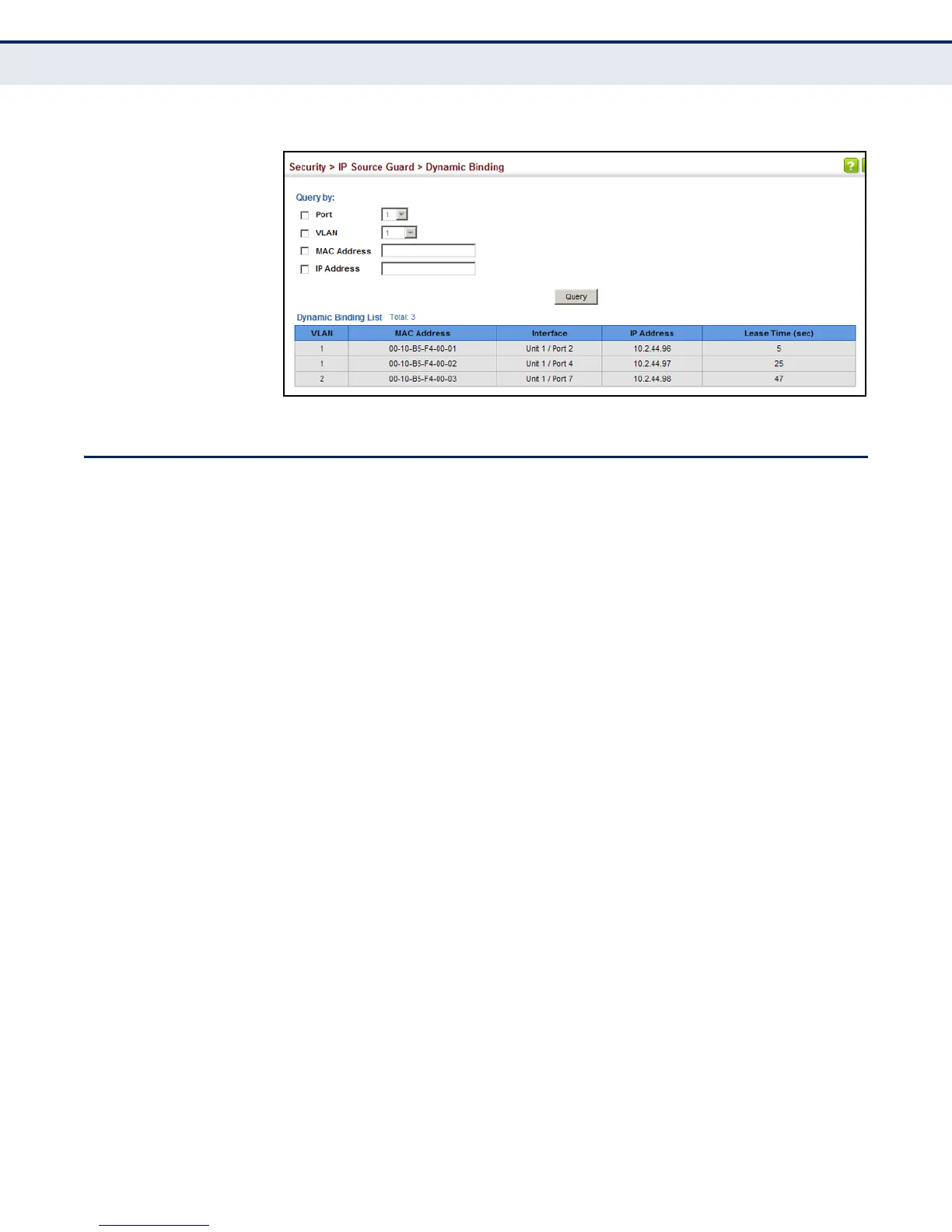
Figure 223: Showing the IP Source Guard Binding Table
IPV6 SOURCE GUARD
IPv6 Source Guard is a security feature that filters IPv6 traffic on non-
routed, Layer 2 network interfaces based on manually configured entries in
the IPv6 Source Guard table, or dynamic entries in the Neighbor Discovery
Snooping table or DHCPv6 Snooping table when either snooping protocol is
enabled (see the DHCPv6 Snooping commands on page 910). IPv6 source
guard can be used to prevent traffic attacks caused when a host tries to
use the IPv6 address of a neighbor to access the network. This section
describes how to configure IPv6 Source Guard.
CONFIGURING
PORTS FOR IPV6
SOURCE GUARD
Use the Security > IPv6 Source Guard > Port Configuration page to filter
inbound traffic based on the source IPv6 address stored in the binding
table.
IPv6 Source Guard is used to filter traffic on an insecure port which
receives messages from outside the network or fire wall, and therefore
may be subject to traffic attacks caused by a host trying to use the IPv6
address of a neighbor.
CLI REFERENCES
◆ "ipv6 source-guard" on page 928
COMMAND USAGE
◆ Setting source guard mode to SIP (Source IP) enables this function on
the selected port. Use the SIP option to check the VLAN ID, IPv6 global
unicast source IP address, and port number against all entries in the
binding table.
◆ After IPv6 source guard is enabled on an interface, the switch initially
blocks all IPv6 traffic received on that interface, except for ND packets
allowed by ND snooping and DHCPv6 packets allowed by DHCPv6
snooping. A port access control list (ACL) is applied to the interface.
Traffic is then filtered based upon dynamic entries learned via ND

 Loading...
Loading...











