iPECS UCP
Feature Description and Operation Manual Issue 1.3
89
COCOS Dialing Restriction
5 No dialing restrictions applied, overrides Station COS 2 through 6.
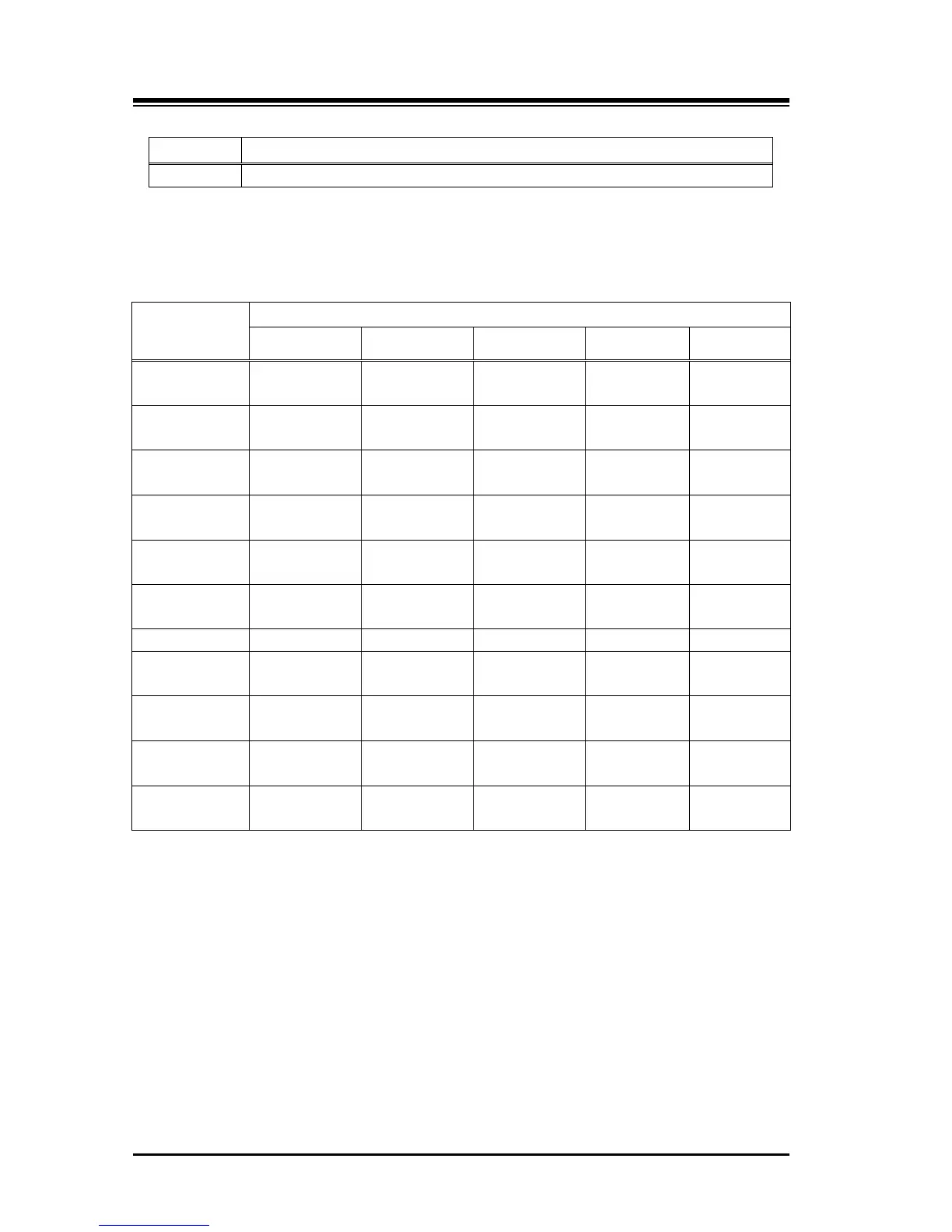
Station and CO COS Interaction – The following chart displays the dialing capabilities based
on the interaction between the Station COS and CO line COS assignments.
Station COS
(Class of
Service)
Restriction
CO COS 1 CO COS 2 CO COS 3 CO COS 4 CO COS 5
1 No restriction No restriction No restriction
No LD calls &
Table C
No restriction
2
Exception Table
A
Exception Table
A
No restriction
No LD calls &
Table C
No restriction
3
Exception Table
B
No restriction
Exception Table
B
No LD calls &
Table C
No restriction
4
Exception Table
A & B
Exception Table
A
Exception Table
B
No LD calls &
Table C
No restriction
5
Local call & Table
C
Local call & Table
C
Local call & Table
C
No LD calls &
Table C
No restriction
6
Local call & Table
C
C
Local call & Table
C
No LD calls &
Table C
No restriction
7 Intercom only Intercom only Intercom only Intercom only Intercom only
8
Exception Table
D
Exception Table
D
No restriction
No LD calls &
Table C
No restriction
9
Exception Table
E
Exception Table
E
No restriction
No LD calls &
Table C
No restriction
10
Exception Table
D & E
Exception Table
D & E
No restriction
No LD calls &
Table C
No restriction
11
Exception Table
A, B, D & E
Exception Table
A, B, D & E
No restriction
No LD calls &
Table C
No restriction
PBX Dialing Codes – Four (4) one or two-digit PBX Trunk Access Codes can be defined in
the system database. When dialed as the first digit(s), these codes signal the system to apply
the appropriate COS. If not dialed, the call is treated as an internal PBX call and dialing is not
restricted.
Exception Tables – Each Exception Table permits entry of 50 Allow codes and 50 Deny
codes. Each code can contain up to 20 digits including digits 0-9, “#” as a wild card (any digit)
and “*”as the end of entry mark. Reference the previous charts for application of the
Exception Tables.
Exception Table process – As digits are dialed, they are compared to entries in the
appropriate Exception Table. Based on the Allow and Deny entries, the system applies the
following rules to allow or deny the call.
 Loading...
Loading...