Cryptographic processor (CRYP) RM0090
728/1749 RM0090 Rev 18
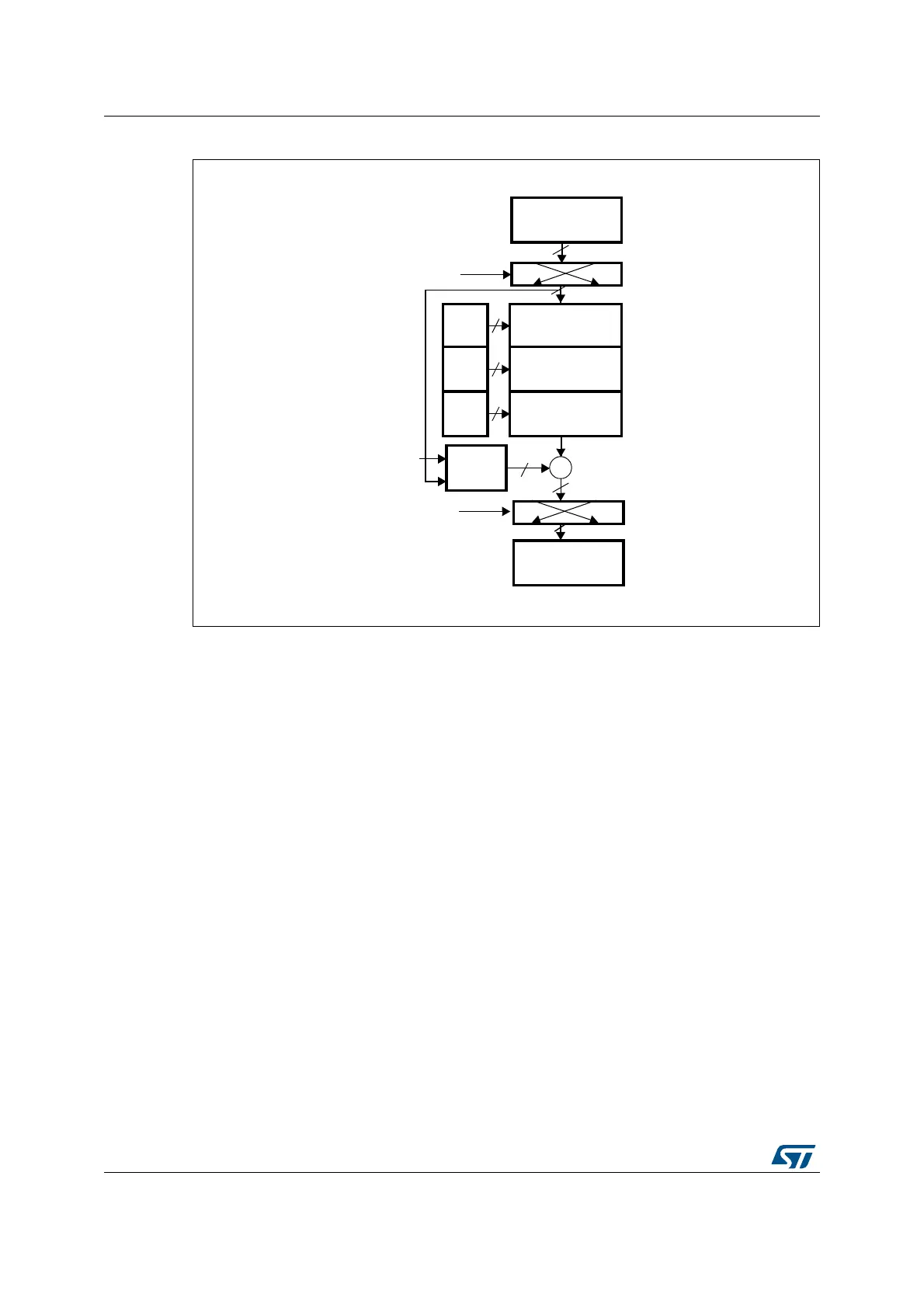
Figure 221. DES/TDES-CBC mode decryption
1. K: key; C: cipher text; I: input block; O: output block; Ps: plain text before swapping (when decoding) or
after swapping (when encoding); P: plain text; IV: initialization vectors.
23.3.2 AES cryptographic core
The AES cryptographic core consists of three components:
• The AES algorithm (AEA: advanced encryption algorithm)
• Multiple keys
• Initialization vector(s) or Nonce
The AES utilizes keys of 3 possible lengths: 128, 192 or 256 bits and, depending on the
operation mode used, zero or one 128-bit initialization vector (IV).
The basic processing involved in the AES is as follows: an input block of 128 bits is read
from the input FIFO and sent to the AEA to be encrypted using the key (K0...3). The key
format depends on the key size:
• If Key size = 128: Key = [K3 K2]
• If Key size = 192: Key = [K3 K2 K1]
• If Key size = 256: Key = [K3 K2 K1 K0]
where Kx=[KxR KxL],R=right, L=left
According to the mode implemented, the resultant output block is used to calculate the
ciphertext.
FIPS PUB 197 (November 26, 2001) provides a thorough explanation of the processing
involved in the four operation modes supplied by the AES core: AES-ECB encryption, AES-
IN FIFO
I, 64 bits
OUT FIFO
Ps, 64 bits
ciphertext C
plaintext P
P, 64 bits
swapping
DEA, decrypt
K3
DEA, encrypt
K2
DEA, decrypt
K1
64
64
64
+
IV0(L/R)
64
AHB2 data write
(before CRYP
is enabled)
O, 64 bits
I is written back
into IV at the
same time as P
is pushed into
the OUT FIFO
C, 64 bits
swapping
DATATYPE
DATATYPE
MS19022V1
 Loading...
Loading...