DGS-3630 Series Layer 3 Stackable Managed Switch Web UI Reference Guide
510
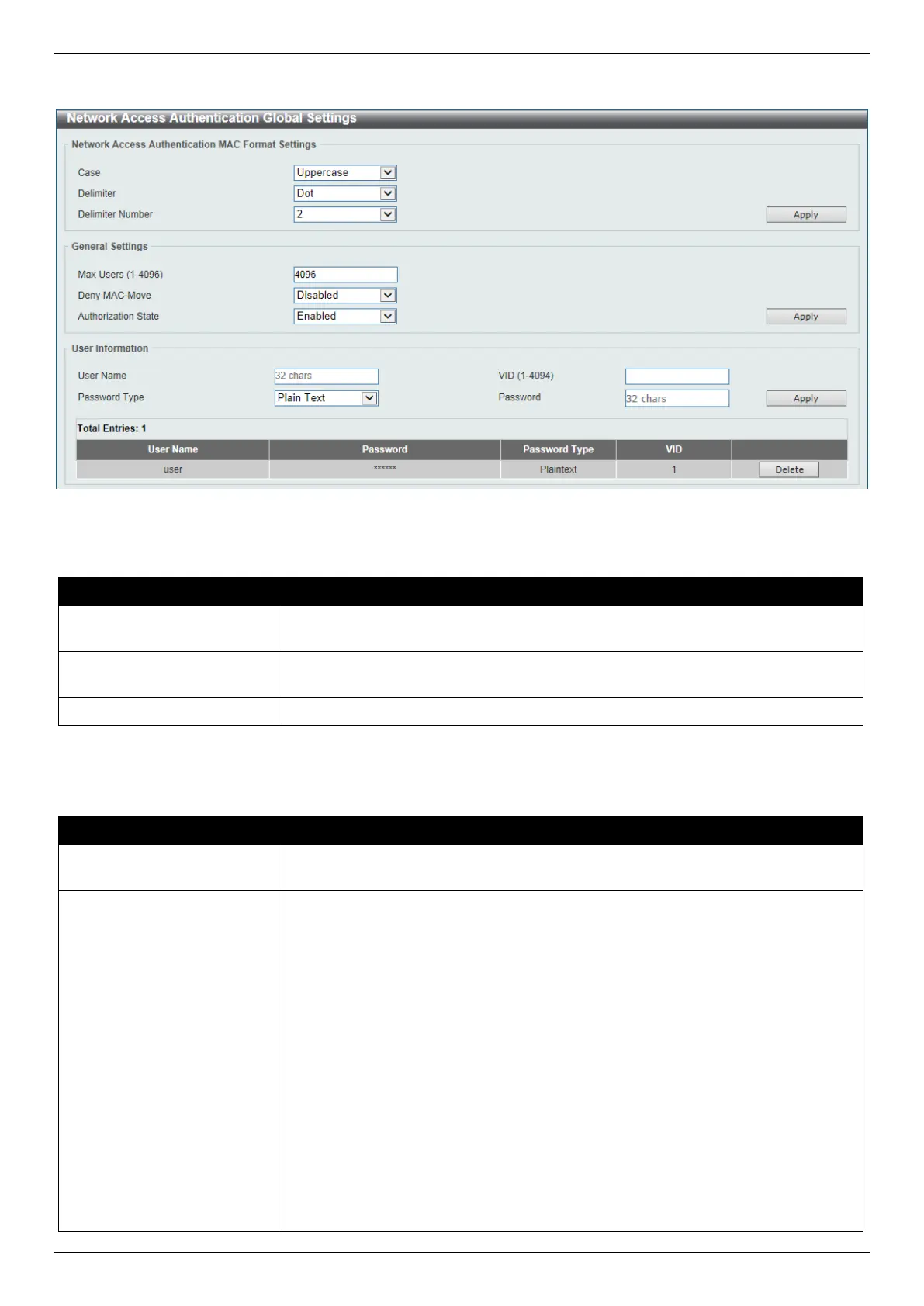
To view the following window, click Security > Network Access Authentication > Network Access Authentication
Global Settings, as shown below:
Figure 9-75 Network Access Authentication Global Settings Window
The fields that can be configured in Network Access Authentication MAC Format Settings are described below:
Parameter Description
Case
Select the case format that will be used for the network access authentication
MAC address here. Options to choose from are Lowercase and Uppercase.
Delimiter
Select the delimiter that will be used for the network access authentication MAC
address here. Options to choose from are Hyphen, Colon, Dot, and None.
Delimiter Number
Select the delimiter number option here. Options to choose from are 1, 2, and 5.
Click the Apply button to accept the changes made.
The fields that can be configured in General Settings are described below:
Parameter Description
Max Users
Enter the maximum amount of users allowed here. This value must be between 1
and 1000. By default, this option is 1000.
Deny MAC-Move
Select to enable or disable the deny MAC-move feature here. This option controls
whether to allow authenticated hosts to do roaming across different Switch ports
and only controls whether a host, which is authenticated at a port set to the multi-
authenticate mode, is allowed to move to another port.
If a station is allowed to move, there are two situations. It may either need to be
re-authenticated or directly moved to the new port without re-authentication based
on the following rule. If the new port has the same authentication configuration as
the original port, then re-authentication is not needed. The host will inherit the
same authorization attributes with new port. The authenticated host can do
roaming from port 1 to port 2, and inherit the authorization attributes without re-
authentication. If the new port has the different authentication configuration as the
original port, then re-authentication is needed. The authenticated host on port 1
can move and re-authenticated by port 2. If the new port has no authentication
method enabled, then the station is directly moved to the new port. The session
with the original port is removed. The authenticated host on port 1 can be moved
to port 2.
If this feature is disabled and an authenticated host moves to another port, then
this is treated as a violation error.

 Loading...
Loading...










