CHAPTER14 Security
Mediant 1000 Gateway & E-SBC | User's Manual
When a user connects to the secured Web interface of the device:
■ If the user has a client certificate from a CA that is listed in the Trusted Root Certificate file, the
connection is accepted and the user is prompted for the system password.
■ If both the CA certificate and the client certificate appear in the Trusted Root Certificate file,
the user is not prompted for a password (thus, providing a single-sign-on experience - the
authentication is performed using the X.509 digital signature).
■ If the user does not have a client certificate from a listed CA or does not have a client
certificate, the connection is rejected.
● The process of installing a client certificate on your PC is beyond the scope of this
document. For more information, refer to your operating system documentation
and/or consult with your security administrator.
● The root certificate can also be loaded through the device's Automatic Provisioning
mechanism, using the HTTPSRootFileName ini file parameter.
● You can enable the device to check whether a peer's certificate has been revoked
by an OCSP server per TLS Context (see Configuring TLS Certificate Contexts).
Configuring TLS Server Certificate Expiry Check
You can configure the TLS Server Certificate Expiry Check feature per TLS Context, whereby the
device periodically checks the validation date of installed TLS server certificates. You can also
configure the device to send an SNMP alarm (acCertificateExpiryAlarm) at a user-defined number
of days before the installed TLS server certificate is to expire. The alarm indicates the TLS Context
to which the certificate belongs.
➢ To configure TLS certificate expiry checks and notification:
1. Open the TLS Contexts table (see Configuring TLS Certificate Contexts).
2. Select the required TLS Context index row, and then click the Change Certificate link located
below the table; the Change Certificates page appears.
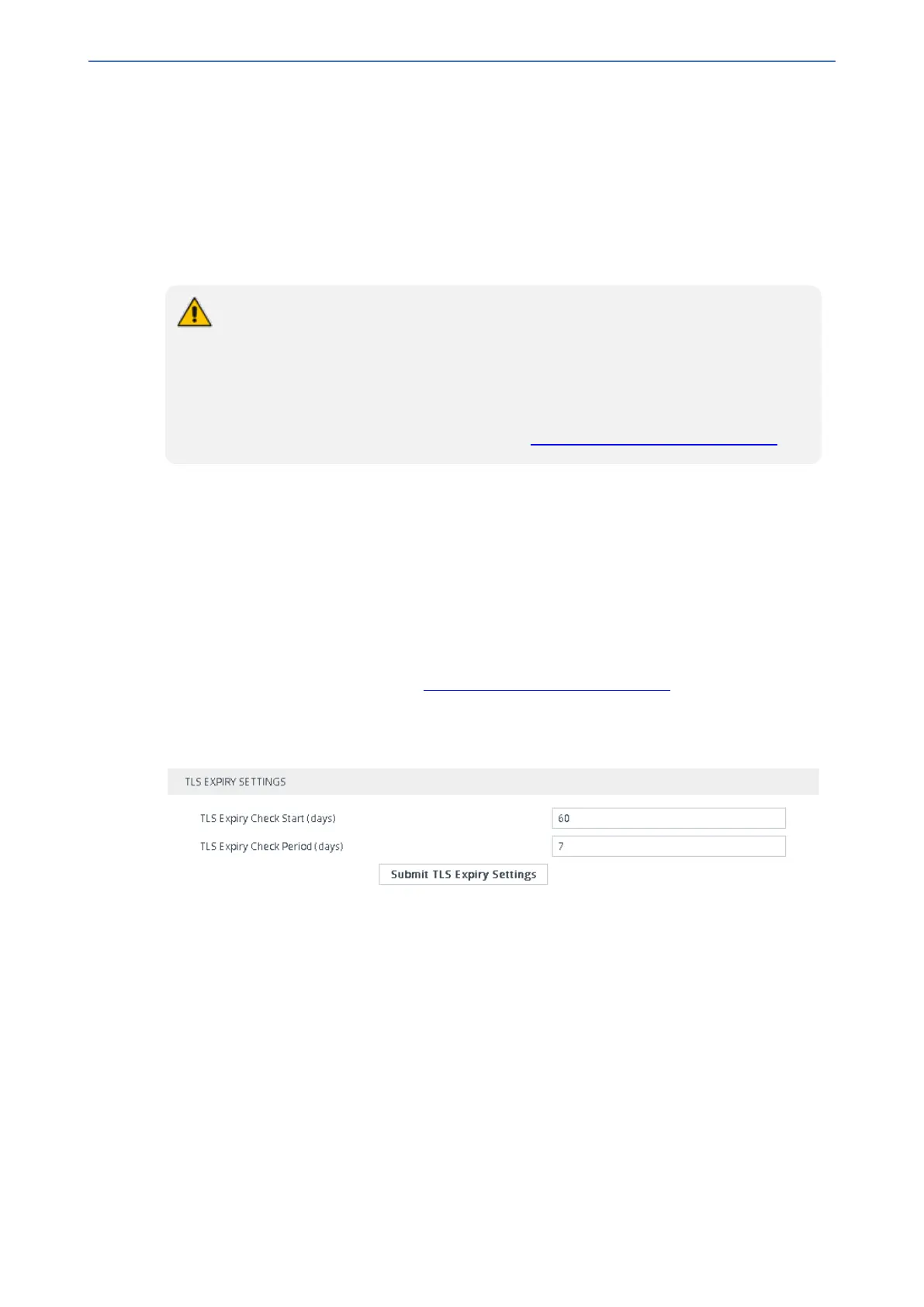
3. Scroll down the page to the TLS Expiry Settings group:
4. In the 'TLS Expiry Check Start' field, enter the number of days before the installed TLS server
certificate is to expire when the device sends an SNMP trap event to notify of this.
5. In the 'TLS Expiry Check Period' field, enter the periodical interval (in days) for checking the
TLS server certificate expiry date. By default, the device checks the certificate every 7 days.
6. Click the Submit TLS Expiry Settings button.
Configuring Firewall Rules
The Firewall table lets you configure up to 50 firewall rules, which define network traffic filtering
rules (access list ) for incoming (ingress) traffic. The access list offers the following firewall
possibilities:
■ Block traffic from known malicious sources
■ Allow traffic only from known "friendly" sources, and block all other traffic
■ Mix allowed and blocked network sources
- 136 -

 Loading...
Loading...











