CHAPTER16 Services
Mediant 1000 Gateway & E-SBC | User's Manual
● Management Service-type LDAP server: This LDAP server account is used only for user
authorization (i.e., the user's management access level and privileges). The device has an
always-on connection with the LDAP server and uses a configured (fixed) LDAP
username (Bind Name) and password. Only if user authentication succeeds, does the
device query this Management Service-type LDAP server account for user authorization.
Thus, management groups and DNs are configured only for this LDAP server account
(instead of for the regular LDAP-based management account).
Therefore, user authorization is done only by a specific LDAP "administrator", which has a fixed
username and password. In contrast, user authentication is done by the user itself (i.e., binding
to the LDAP account with each user's username and password). Having a dedicated LDAP
account for user authorization may provide additional security to the network by preventing
users from accessing the authorization settings in the LDAP server.
For all the previously discussed LDAP services, the following additional LDAP functionality is
supported:
■ Search method for searching DN object records between LDAP servers and within each LDAP
server (see Configuring LDAP Search Methods).
■ Default access level that is assigned to the user if the queried response does not contain an
access level.
■ Local Users table for authenticating users instead of the LDAP server (for example, when a
communication problem occurs with the server). For more information, see Configuring Local
Database for Management User Authentication.
Enabling the LDAP Service
Before you can configure LDAP support, you need to enable the LDAP service.
➢ To enable LDAP:
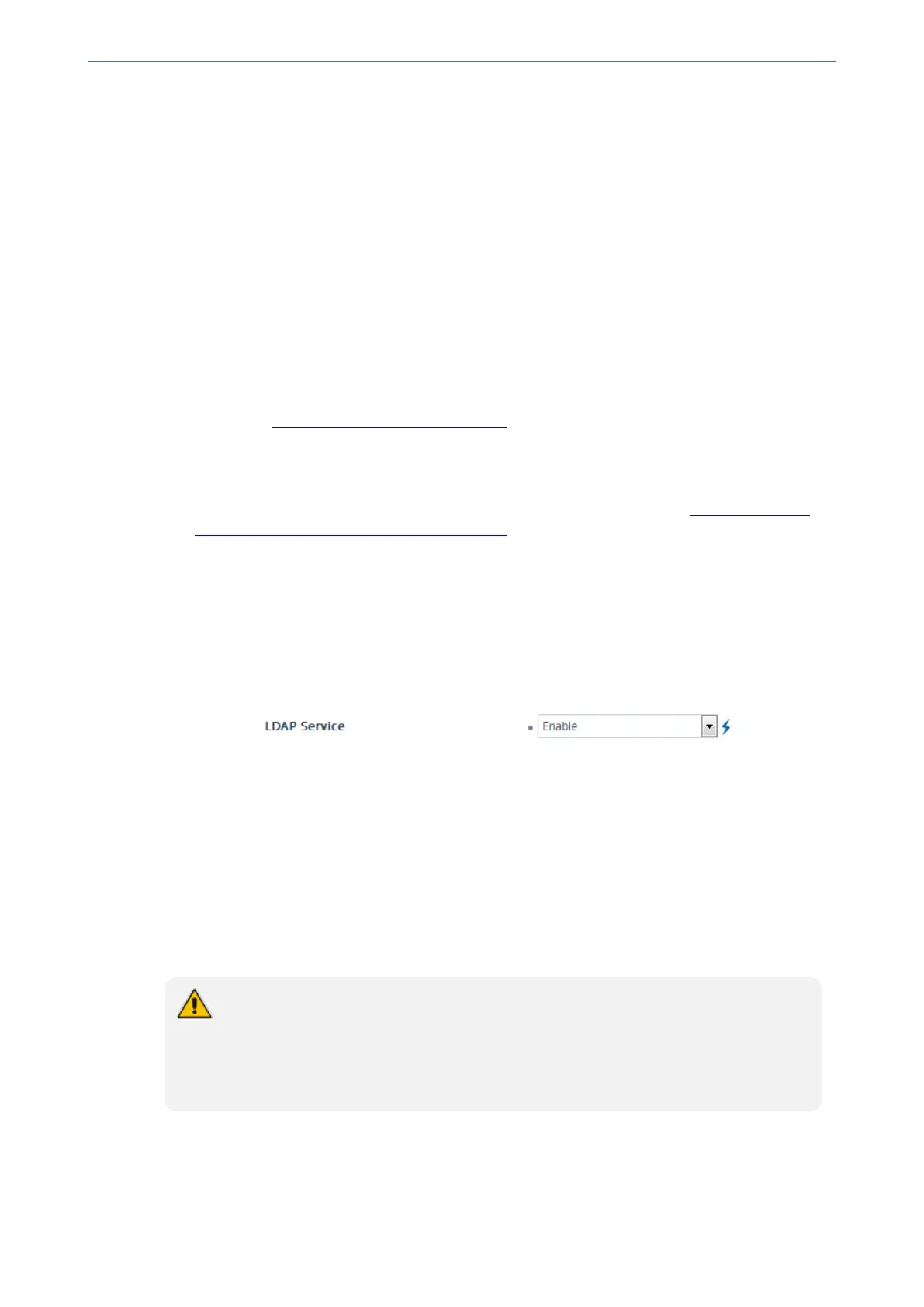
1. Open the LDAP Settings page (Setup menu > IP Network tab > RADIUS & LDAP folder >
LDAP Settings).
2. From the 'LDAP Service' drop-down list, select Enable.
3. Click Apply, and then reset the device with a save-to-flash for your settings to take effect.
Enabling LDAP-based Web/CLI User Login Authentication and
Authorization
The LDAP service can be used for authenticating and authorizing device management users (Web
and CLI) based on the user's login username and password (credentials). At the same, it can also
be used to determine users' management access levels (privileges). Before you can configure
LDAP-based login authentication, you must enable this type of LDAP service.
If you enable LDAP- based user login authentication, when users with Security
Administrator privilege level log in to the device’s CLI, they are automatically given
access to the CLI privileged mode (“#”). For all other user privilege levels, the user
needs to run the enable command and then enter the password to access the CLI
privileged mode.
➢ To enable LDAP-based login authentication:
1. Open the Authentication Server page (Setup menu > Administration tab > Web & CLI folder
> Authentication Server).
- 211 -

 Loading...
Loading...











