RM0090 Cryptographic processor (CRYP)
Doc ID 018909 Rev 4 560/1422
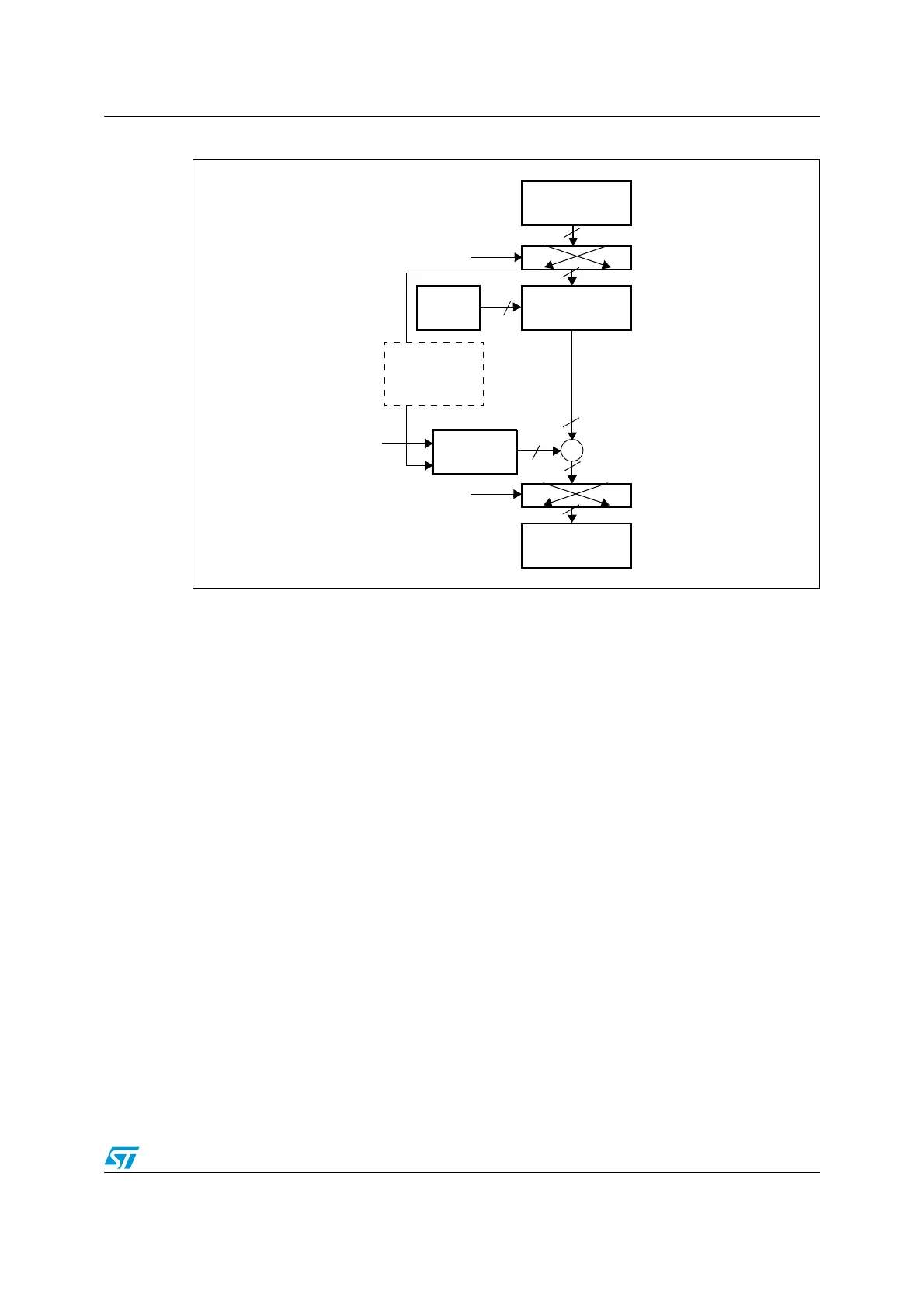
Figure 210. AES-CBC mode decryption
1. K: key; C: cipher text; I: input block; O: output block; Ps: plain text before swapping (when decoding) or
after swapping (when encoding); P: plain text; IV: Initialization vectors.
2. IVx=[IVxR IVxL], R=right, L=left.
3. If Key size = 128 => Key = [K3 K2].
If Key size = 192 => Key = [K3 K2 K1]
If Key size = 256 => Key = [K3 K2 K1 K0].
AES counter mode (AES-CTR) mode
The AES counter mode uses the AES block as a key stream generator. The generated keys
are then XORed with the plaintext to obtain the cipher. For this reason, it makes no sense to
speak of different CTR encryption/decryption, since the two operations are exactly the
same.
In fact, given:
● Plaintext: P[0], P[1], ..., P[n] (128 bits each)
● A key K to be used (the size does not matter)
● An initial counter block (call it ICB but it has the same functionality as the IV of CBC)
The cipher is computed as follows:
C[i] = enck(iv[i]) xor P[i], where:
iv[0] = ICB and iv[i+1] = func(iv[i]), where func is an update function
applied to the previous iv block; func is basically an increment of one of the fields
composing the iv block.
Given that the ICB for decryption is the same as the one for encryption, the key stream
generated during decryption is the same as the one generated during encryption. Then, the
ciphertext is XORed with the key stream in order to retrieve the original plaintext. The
decryption operation therefore acts exactly in the same way as the encryption operation.
IN FIFO
I, 128 bits
OUT FIFO
ciphertext C
plaintext P
P, 128 bits
swapping
AEA, decrypt
K 0...
3
(3)
128, 192
+
128
AHB2 data write
(before CRYP
is enabled)
O, 128 bits
I is written
back into IV
at the same time
as P is pushed
into the OUT FIFO
C, 128 bits
swapping
DATATYPE
DATATYPE
or 256
Ps, 128 bits
MS19024V1
IV=[IV1 IV0]
(2)

 Loading...
Loading...