Zone Configuration
Except on the first page, right running head:
Heading1 or Heading1NewPage text (automatic)
771
Alcatel-Lucent
Beta Beta
OmniAccess 5740 Unified Services Gateway CLI Configuration Guide
ZONE CONFIGURATION
Refer to following sections for detailed spectrum on configuring zones:
• “Trusted Zone Configuration”
• “Untrusted Zone Configuration”
• “Semi-trusted Zone or Demilitarized Zone”
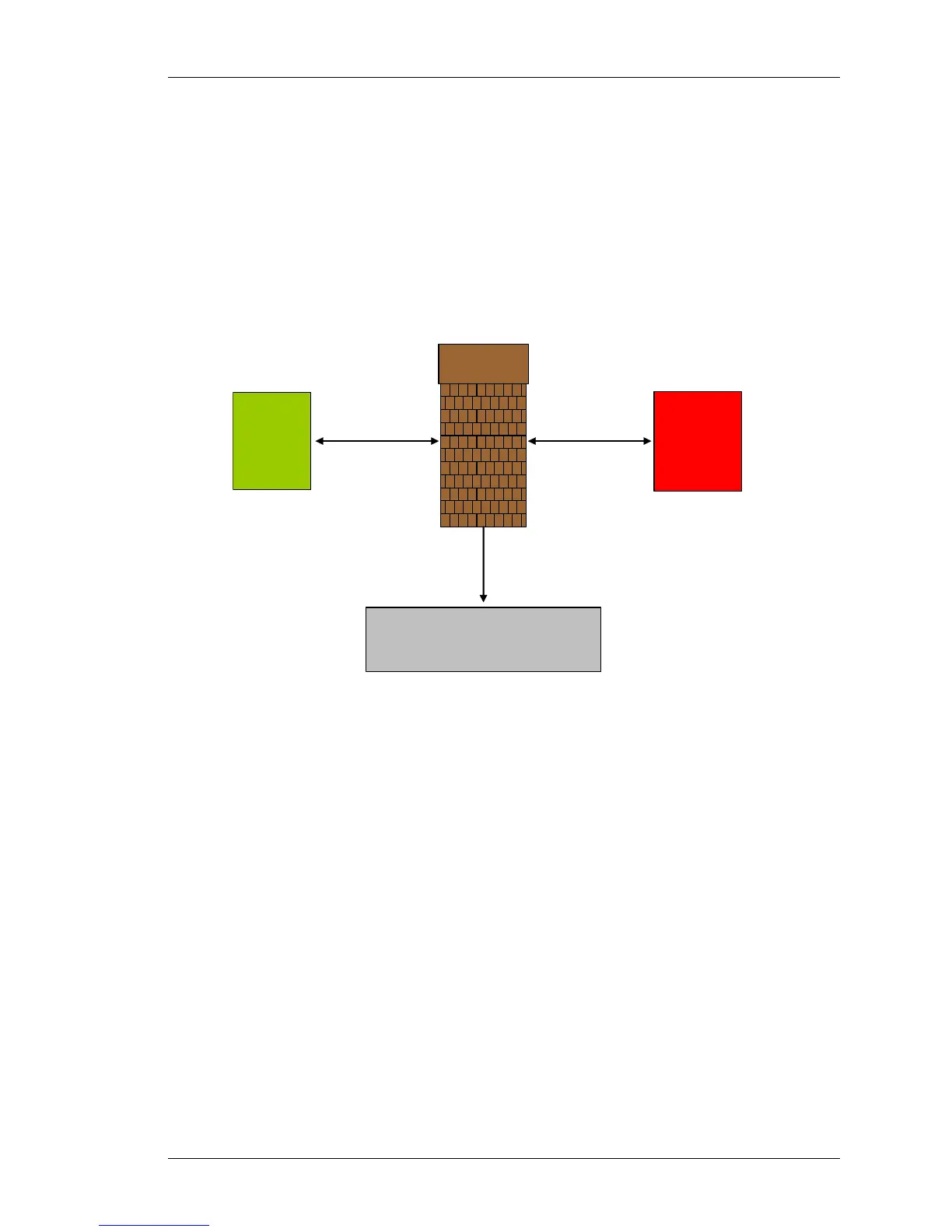
Figure 22: Figure Depicting Three Zones
TRUSTED ZONE CONFIGURATION
The "Trusted Zone" is a network domain in which the users and systems are
known entities and hence, communication between the known entities is
conducted in an environment of integrity. Hence, data presented from resulting
communication is not checked for malicious content or intent. In a corporate
network, all systems within the domain of the company is considered to be within
a "trusted zone".
UNTRUSTED ZONE CONFIGURATION
The domain falling outside the "trusted zone" is the "untrusted zone". Hence,
external networks which comprise traffic or systems that are not within the
administrative purview of a private network, such as the Internet, is an example of
"untrusted zone".
Trusted
Zone
Untrusted
Zone
Semi-Trusted Zone (DMZ)
Firewall

 Loading...
Loading...