RM0453 Rev 1 657/1461
RM0453 AES hardware accelerator (AES)
698
GMAC is similar to GCM, except that it is applied on a message composed only by plaintext
authenticated data (that is, only header, no payload).
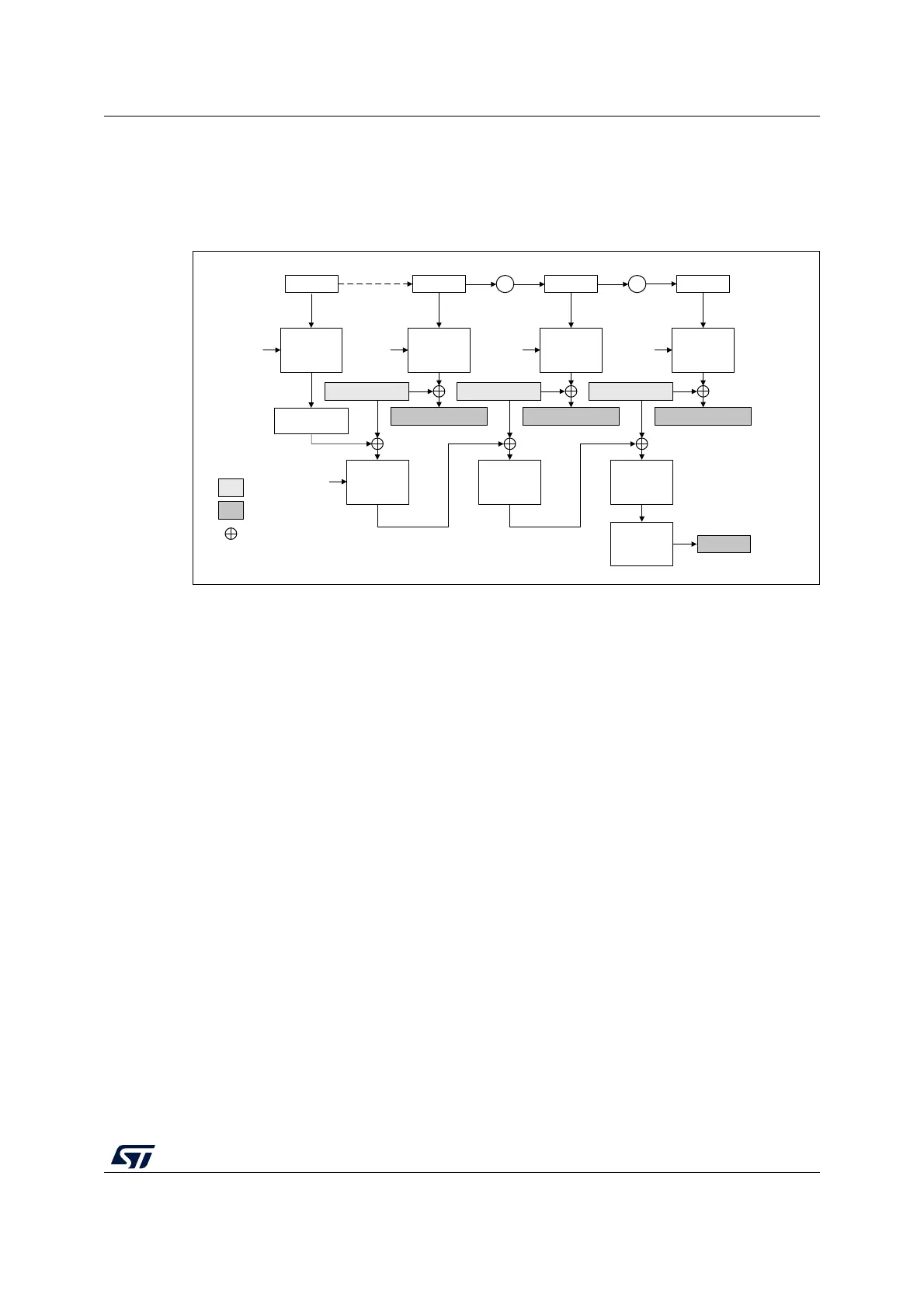
Counter with CBC-MAC (CCM) principle
Figure 107. CCM encryption and authentication principle
In Counter with cipher block chaining-message authentication code (CCM) mode, the
plaintext message is encrypted while a message authentication code (MAC) is computed in
parallel, thus generating the corresponding ciphertext and the corresponding MAC (also
known as tag). It is described by NIST in Special Publication 800-38C, Recommendation for
Block Cipher Modes of Operation - The CCM Mode for Authentication and Confidentiality.
CCM mode is based on AES in counter mode for confidentiality and it uses CBC for
computing the message authentication code. It requires an initial value.
Like GCM, the CCM chaining mode can be applied on a message composed only by
plaintext authenticated data (that is, only header, no payload). Note that this way of using
CCM is not called CMAC (it is not similar to GCM/GMAC), and its usage is not
recommended by NIST.
23.4.4 AES procedure to perform a cipher operation
Introduction
A typical cipher operation is explained below. Detailed information is provided in sections
starting from Section 23.4.8: AES basic chaining modes (ECB, CBC).
MSv42145V1
Plaintext block 1
Ciphertext block 1 Ciphertext block 2 Ciphertext block 3
Encrypt Encrypt Encrypt
key key key
Plaintext block 2 Plaintext block 3
Count 1 Count 2 Count 3
+1 +1
Encrypt Encrypt Encrypt
Final
TAG
Init
(Encrypt)
key
Initialization
vector
input
output
Legend
XOR
B0
key

 Loading...
Loading...