RM0453 Rev 1 79/1461
RM0453 Global security controller (GTZC)
96
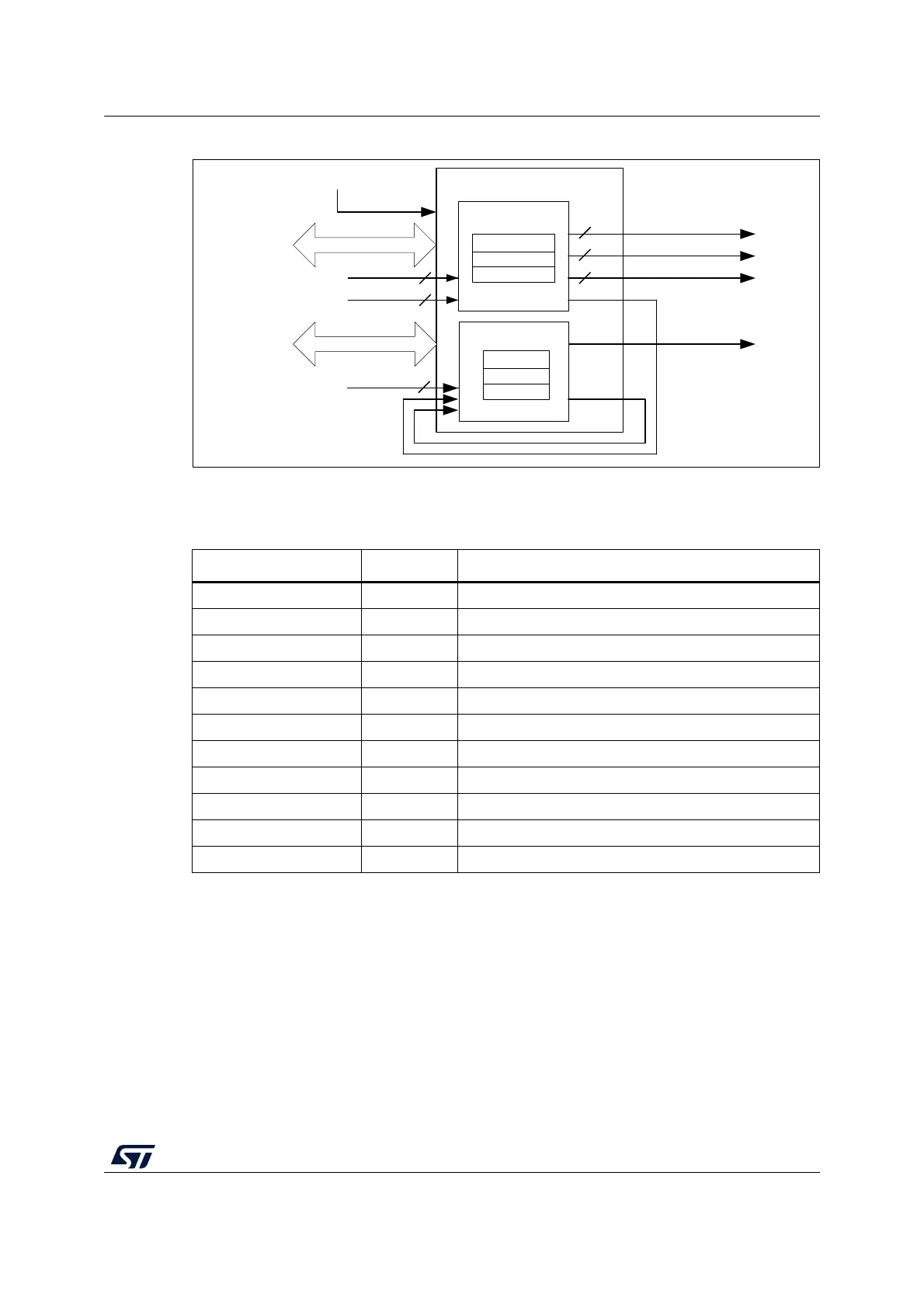
Figure 5. GTZC block diagram
3.4.2 GTZC internal signals
3.4.3 Illegal access definition
The existing types of illegal access are listed below:
• Illegal non-secure read write access
Any non-secure read write transaction trying to access a secure resource is considered
as illegal. The addressed resource generates an illegal access event for illegal read
/write access.
MSv60799V1
GTZC
TZSC
TZIC
AHB
tzsc_periph[n]_sec
tzsc_periph[n]_priv
n x ila_event
(from peripherals)
SECCFGR
PRIVCFGR
MPCWMR
IER
MISR
ICR
tzic_ila_event
(from option bytes)
ESE
AHB
tzsc_periph[n]_ sec
tzsc_mpcwm[n]_ sec
tzsc_mpcwm[n]_priv
tzsc_ila_event
tzic_ila_it
(from option byte)
Table 5. GTZC internal signals
Internal signal name Signal type Description
AHB Input/output AHB slaves TZSC and TZIC register access ports
ESE Input Security enable from user option ESE
tzsc_periph[n]_sec Input TZSC peripheral [n] security control from User option
tzsc_mpcmw[n]_sec Input TZSC MPCWM [n] security control from User option
tzsc_periph[n]_sec Output TZSC peripheral [n] security control
tzsc_periph[n]_priv Output TZSC peripheral [n] privileged control
tzsc_mpcmw[n]_priv Output TZSC internal memories MPCWM [n] privileged control
tzsc_ila_event Output TZSC illegal access event
tzic_ila_event Output TZIC illegal access event
ila_events Input Peripheral illegal access events
tzic_ila_it Output TZIC illegal access interrupt

 Loading...
Loading...