RM0453 Rev 1 675/1461
RM0453 AES hardware accelerator (AES)
698
23.4.12 AES counter with CBC-MAC (CCM)
Overview
The AES counter with cipher block chaining-message authentication code (CCM)
algorithm allows encryption and authentication of plaintext, generating the corresponding
ciphertext and tag (also known as message authentication code). To ensure confidentiality,
the CCM algorithm is based on AES in counter mode. It uses cipher block chaining
technique to generate the message authentication code. This is commonly called CBC-
MAC.
Note: NIST does not approve this CBC-MAC as an authentication mode outside the context of the
CCM specification.
CCM chaining is specified in NIST Special Publication 800-38C, Recommendation for Block
Cipher Modes of Operation - The CCM Mode for Authentication and Confidentiality. A typical
message construction for CCM is given in Figure 122.
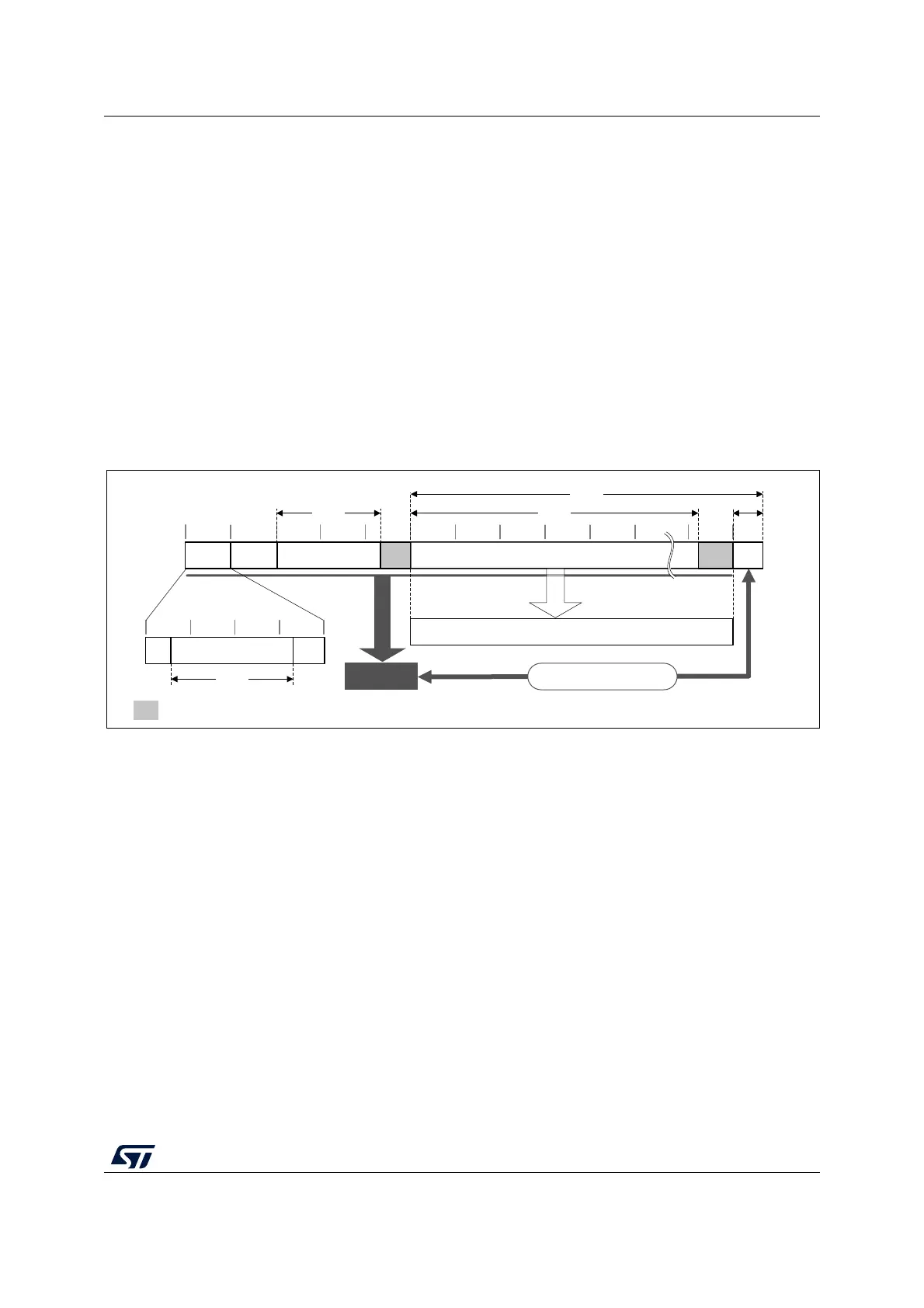
Figure 122. Message construction in CCM mode
The structure of the message is:
• 16-byte first authentication block (B0), composed of three distinct fields:
– Q: a bit string representation of the octet length of P (Len(P))
– Nonce (N): a single-use value (that is, a new nonce must be assigned to each
new communication) of Len(N) size. The sum Len(N) + Len(P) must be equal to
15 bytes.
– Flags: most significant octet containing four flags for control information, as
specified by the standard. It contains two 3-bit strings to encode the values t (MAC
length expressed in bytes) and Q (plaintext length such that Len(P) < 2
8q
bytes).
The counter blocks range associated to Q is equal to 2
8Q-4
, that is, if the maximum
value of Q is 8, the counter blocks used in cipher must be on 60 bits.
• 16-byte blocks (B) associated to the Associated Data (A).
This part of the message is only authenticated, not encrypted. This section has a
known length Len(A) that can be a non-multiple of 16 bytes (see Figure 122). The
MSv42159V2
Plaintext (P)
16-byte
boundaries
Associated data (A)
Authenticated & encrypted ciphertext (C)
0
Len(A) Len(P)
0
Enc
(T)
MAC (T)
B0
4-byte boundaries
QNonce (N)
authenticate
encrypt
Zero padding
Len(C)
[a]
32
[a]
16
Len(T)
flags
Len(N)
Decrypt and compare

 Loading...
Loading...