16 PIM Snooping Configuration
This chapter will describe how to configure the protocol independent multicast snooping on
the DGS-3610 series. It will cover the content below:
Understand the PIM snooping principle.
Configure the PIM snooping by default.
Guide and restriction the PIM snooping configuration.
Configure the PIM snooping.
16.1 Understanding PIM Snooping
Principle
Within the network that the L2 switches connect to several routers, the switches will flood the
multicast data flow into all router ports even though the multicast function is not enabled in
the downstream direction. When the PIM snooping is enabled, the switches will limit the
multicast data to connect the ports of the multicast routers.
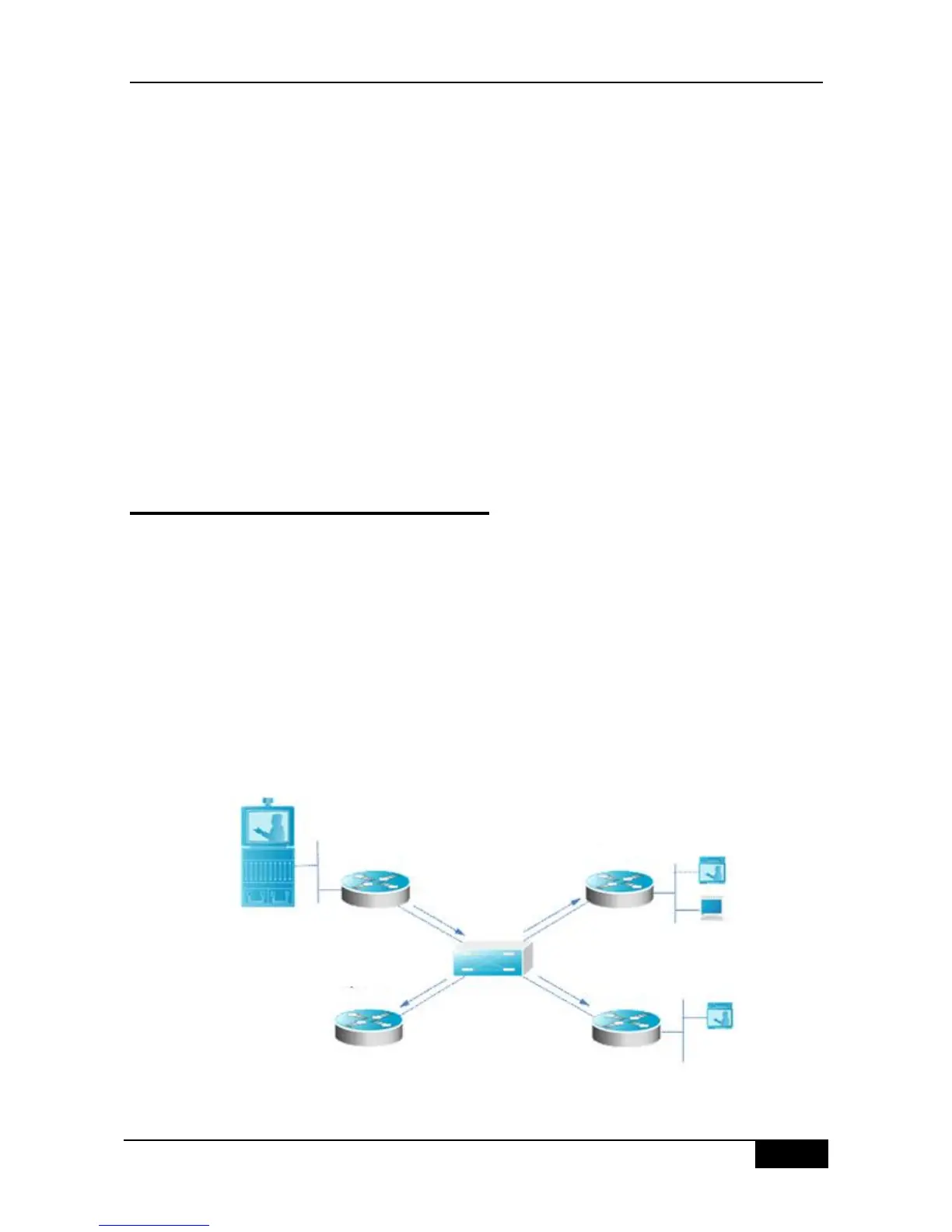
The figure below shows the multicast data flow flooding before the PIM snooping is enabled
and the multicast data stream limit after the PIM snooping is enabled.
In the Figure 16-1, the multicast data will flow into all the ports of the switches if the PIM
snooping is not enabled.
Figure 16-1 Multicast flow the PIM snooping is diabled

 Loading...
Loading...











