Chapter 44 Access Control List Configuration DGS-3610 Series Configuration Guide
44.1.2 Why to Configure Access Lists
There are many reasons why we need configure access lists, shown as follows:
Restrict route updating: Control the places of sending and receiving the route updating
information.
Restrict network access: To ensure network security, make users unable to access
some services by defining rules. (When a user only needs to access the WWW and
E-mail services, other services like TELNET are disabled). Or, allow users to access
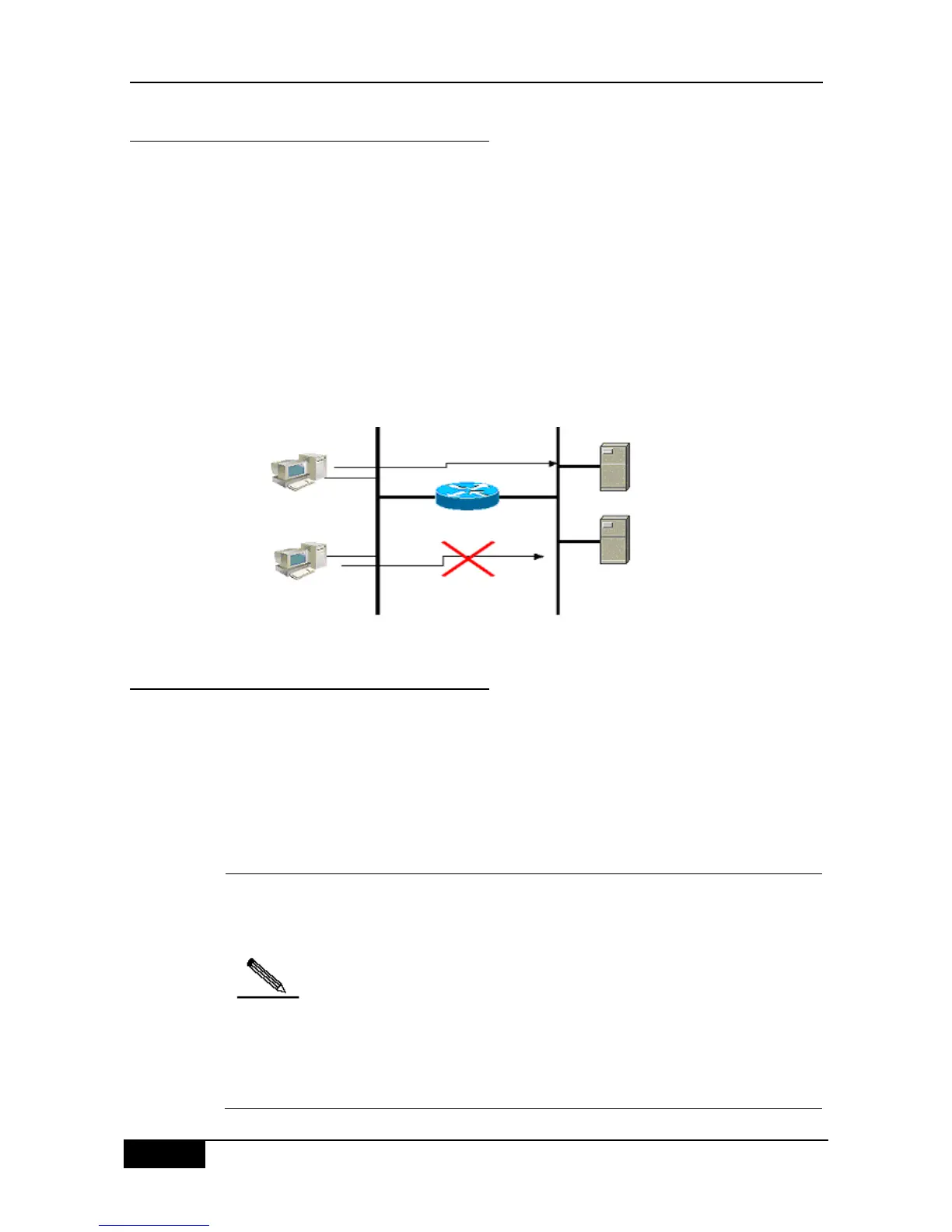
services only in a given period or only allow some hosts to access networks. Figure
45-1 is a case. In the case, only host A can access the Finance Network, while Host B
cannot.
Figure 44-1 Using Access List to Control Network Access
PC B
Finance
Server
Accounting
Server
Finance Network
Human Resource
Network
PC A
44.1.3 When to Configure Access Lists
Depending on your requirements, you can select the basic access list or dynamic access list.
In general, the basic access list can meet the security requirements. However, experienced
hackers can provide spoof source addresses through some software so as to deceive the
devices and successfully access the network. Before the user can access the network, the
dynamic access list requires the pass of authentication so that the hackers are difficult to
invade the network. So, in some sensitive areas the dynamic access list can be used to
ensure the network security.
The behavior of providing spoof source addresses to deceive devices is
called spoofing and it is an inherent problem of all access lists. Even you
use the dynamic list, a spoofing problem may occur. During the valid
access period of an authenticated user, a hacker may use a counterfeit
user address and accesses the network. There are two methods to solve
the problem. One method is to set free time for a user to access the
network as little as possible, making a hacker difficult to attack the
network. The other method is to use the IPSEC encryption protocol to
encrypt network data, ensuring that all the data entering devices are
encrypted.

 Loading...
Loading...











