On an 802.1X-enabled device, all ports are uncontrolled ports by default. We can set a port
as a controlled port, to impose authentication over all the users under that port.
When a user has passed authentication (the switch has received success packets from the
RADIUS Server), the user is authorized and therefore can freely use network resources.If
the user fails in the authentication and remains in the unauthenticated status, it is possible to
initiate authentication once again. If the communication between the switch and the RADIUS
server is faulty, the user is still unauthorized and therefore still cannot use the network.
When the user sends the EAPOL-LOGOFF packets, its status is changed from authorized to
unauthorized.
When a port of the switch is changed to the LINK-DOWN status, all the users on the port
change to the unauthorized status.
When the device restarts, all users on the device turn into the unauthorized status.
To force a user to pass the authentication, you can add a static MAC address.
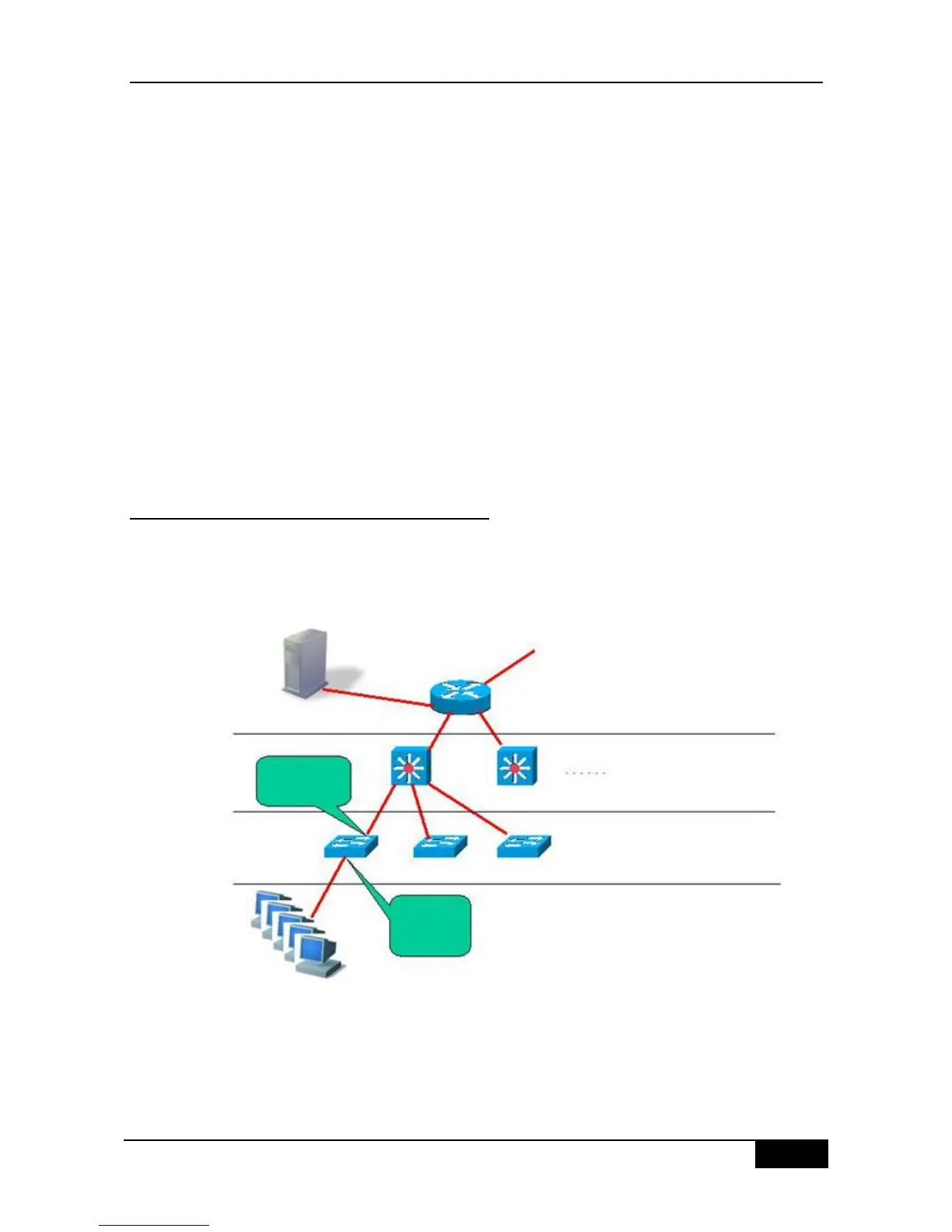
37.1.4 Topologies of Typical Applications
A. The 802.1X-enabled device is used as the access layer device
Figure 37-3
 Loading...
Loading...











