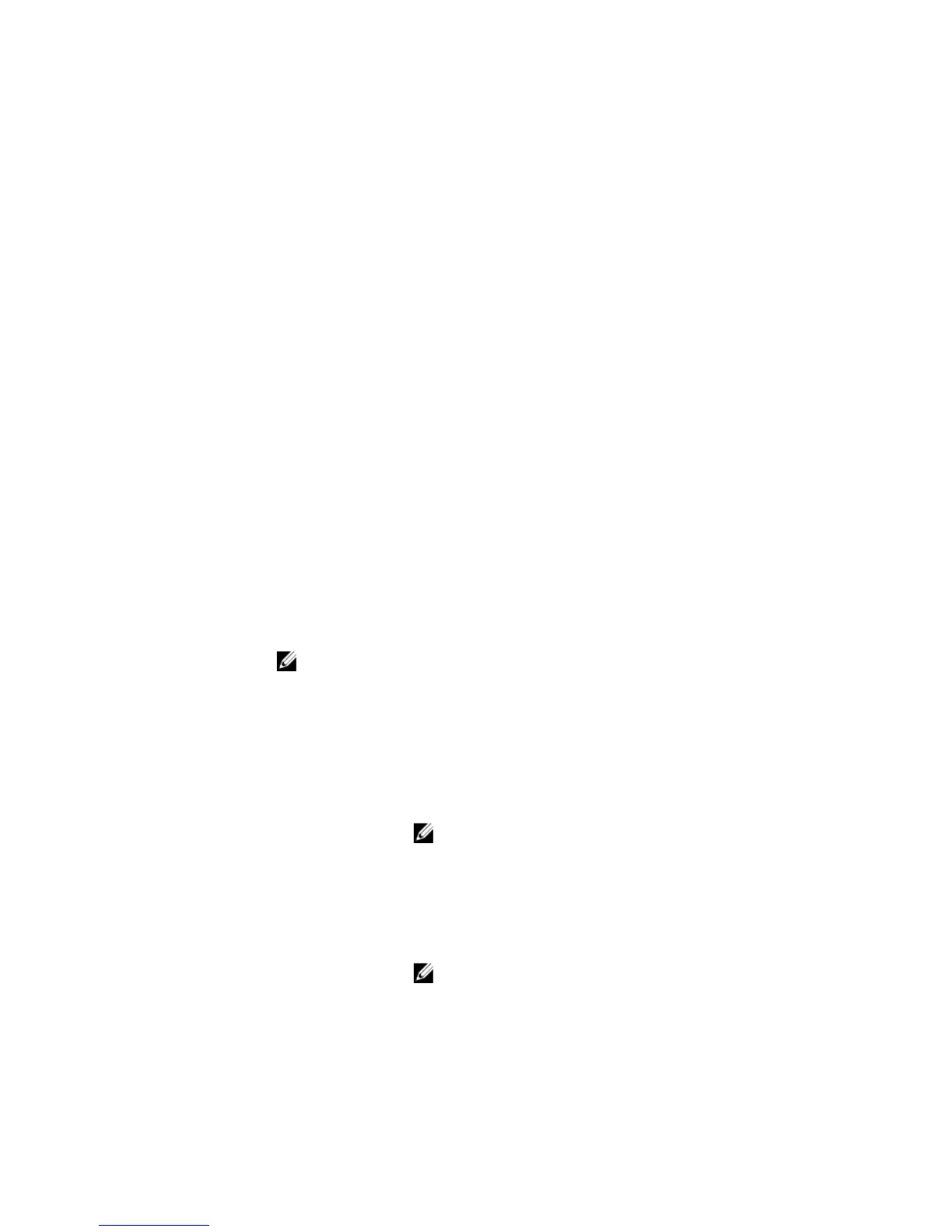
Auth-Fail VLAN id: 11
Auth-Fail Max-Attempts: 3
Tx Period: 30 seconds
Quiet Period: 60 seconds
ReAuth Max: 2
Supplicant Timeout: 30 seconds
Server Timeout: 30 seconds
Re-Auth Interval: 3600 seconds
Max-EAP-Req: 2
Auth Type: SINGLE_HOST
Auth PAE State: Initialize
Backend State: Initialize
Dell#
SSH Server and SCP Commands
Dell Networking OS supports secure shell (SSH) protocol versions 1.5 and 2.0. SSH is a protocol for
secure remote login over an insecure network. SSH sessions are encrypted and use authentication.
The SSH server and client are enhanced to support the VRF awareness functionality. Using this capability,
an SSH client or server can use a VRF instance name to look up the correct routing table and establish a
connection.
crypto key generate
Generate keys for the SSH server.
S4810
Syntax
NOTE: Some of the parameters in this command require licensing to access.
For more information, contact your Dell Networking representative.
crypto key generate {rsa | rsa1}
Parameters
rsa Enter the keyword rsa then the key size to generate a SSHv2
RSA host keys. The range is from 1024 to 2048 if you did not
enable FIPS mode; if you enabled FIPS mode, you can only
generate a 2048-bit key. The default is 1024.
NOTE: You must have a license to access the FIPS mode.
For more information, contact your Dell Networking
representative.
rsa1 Enter the keyword rsa1 then the key size to generate a
SSHv1 RSA host keys. The range is from 1024 to 2048. The
default is 1024.
NOTE: This option is not available in FIPS mode.
Defaults Key size 1024; if you enable FIPS mode, the key size is 2048.
1506
Security

 Loading...
Loading...











