49-25
Catalyst 4500 Series Switch, Cisco IOS Software Configuration Guide - Cisco IOS XE 3.9.xE and IOS 15.2(5)Ex
Chapter 49 Configuring 802.1X Port-Based Authentication
About 802.1X Port-Based Authentication
Because of this topology, the authenticator switch cannot always be trusted. For example, compact switches (8-port Catalyst
3560 and Catalyst 2960) are generally deployed outside the wiring closet. This enables hacker devices to swamp them to gain
access to the network, compromising security. An edge switch must be able to authenticate itself against another switch,
referred to as Network Edge Authentication Topology (NEAT).
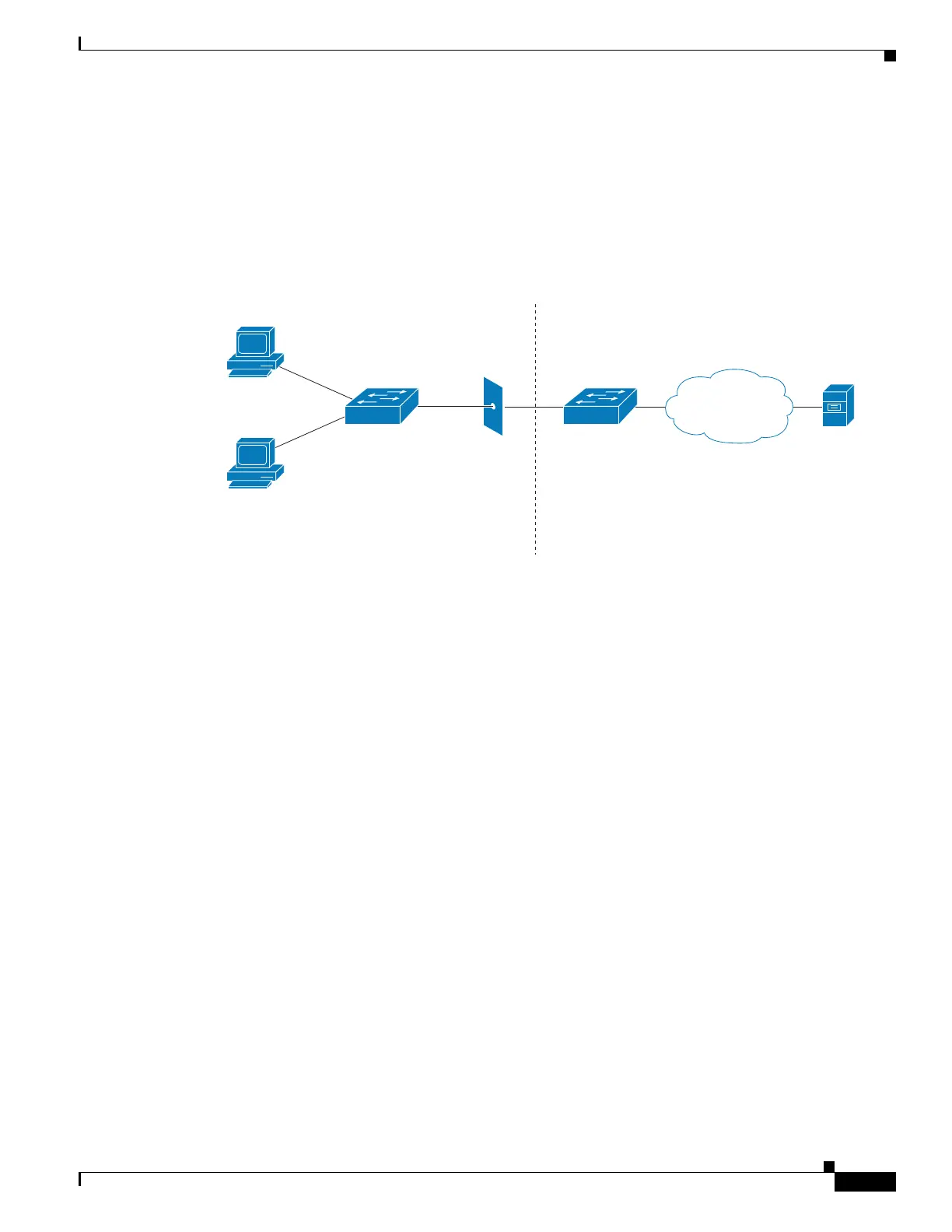
Figure 49-8 illustrates a typical NEAT topology.
Figure 49-8 Typical NEAT Topology
NEAT facilitates the following functionality in such scenarios:
Host Authorization— Ensures that only traffic from authorized hosts (connecting to the switch with a supplicant) is
allowed on the network. The switches use Client Information Signalling Protocol (CISP) to send the MAC addresses
connecting the supplicant switch to the authenticator switch.
Auto enablement—Automatically enables trunk configuration on the authenticator switch, allowing user traffic from
multiple VLANs arising from supplicant switches. At the ACS, you must configure the Cisco AV pair as
device-traffic-class=switch. For details on how to do this, see the “Configuring an Authenticator and a Supplicant Switch
with NEAT” section on page 49-88.
How 802.1X Fails on a Port
802.1X may fail on a port in three ways: timeout, explicit failure, and protocol timeout.
Timeout—A switch attempts 802.1X at link up but the attached endpoint is not 802.1X-capable. After the configured
number of retries and timeouts, the switch attempts the next authentication method if one is configured (like MAB). If
MAB fails, the switch deploys the Guest VLAN (also called the no-response VLAN), if configured. The Guest VLAN is
configured with the authentication event no-response interface command.
Explicit Failure—A switch and the endpoint perform the entire 802.1X authentication sequence and the result is an explicit
failure (usually indicated by an Access-Reject from the RADIUS server to the switch and an EAP-Failure sent from the
switch to the endpoint). In this case, the switch attempts MAB (if “authentication event failure action next-method” is
configured) or deploy the AuthFail VLAN (if “authentication event failure action authorize vlan” is configured).
Protocol Timeout—A switch and the endpoint start the 802.1X authentication process but do not complete it. For example,
the endpoint may send an 802.1X EAPoL-Start message and then stop responding to the switch (perhaps, because the
endpoint lacks a credential or because it is waiting for end user to enter some information). In this case, the switch knows
that the connected device is EAPoL-capable, so it will not deploy the Guest VLAN after timing out. Instead, it restarts
authentication after a timeout. The switch continues to label the port as EAPoL-capable until a physical link down event
SSw
Supplicant to ASw-switch
Authenticator for clients
ASw
Authenticator
AAA
RADIUS
Server
ACS
Campus
LAN
Wiring closet
Switch
Wall jack
in
conference
room
Cisco Switch w
Supplicant (EAP-MD5)
Also acts as 802.1X
Authenticator to hosts
207274

 Loading...
Loading...




















