49-100
Catalyst 4500 Series Switch, Cisco IOS Software Configuration Guide - Cisco IOS XE 3.9.xE and IOS 15.2(5)Ex
Chapter 49 Configuring 802.1X Port-Based Authentication
Controlling Switch Access with RADIUS
CoA ACK Response Code
If the authorization state is changed successfully, a positive acknowledgement (ACK) is sent. The attributes returned within
CoA ACK will vary based on the CoA Request and are discussed in individual CoA Commands.
CoA NAK Response Code
A negative acknowledgement (NAK) indicates a failure to change the authorization state and can include attributes that indicate
the reason for the failure. Use show commands to verify a successful CoA.
CoA Request Commands
This section includes:
• Session Reauthentication
• Session Termination
• CoA Disconnect-Request
• CoA Request: Disable Host Port
• CoA Request: Bounce-Port
The switch supports the commands shown in Table 49-4.
Session Reauthentication
The AAA server typically generates a session reauthentication request when a host with an unknown identity or posture joins
the network and is associated with a restricted access authorization profile (such as a guest VLAN). A reauthentication request
allows the host to be placed in the appropriate authorization group when its credentials are known.
To initiate session authentication, the AAA server sends a standard CoA-Request message which contains a Cisco
vendor-specific attribute (VSA) in this form: Cisco:Avpair=“subscriber:command=reauthenticate” and one or more session
identification attributes.
The current session state determines the switch response to the message. If the session is currently authenticated by IEEE
802.1x, the switch responds by sending an EAPoL
1
-RequestId message (see footnote 1 below) to the server.
If the session is currently authenticated by MAC authentication bypass (MAB), the switch sends an access-request to the server,
passing the same identity attributes used for the initial successful authentication.
If session authentication is in progress when the switch receives the command, the switch terminates the process, and restarts
the authentication sequence, starting with the method configured to be attempted first.
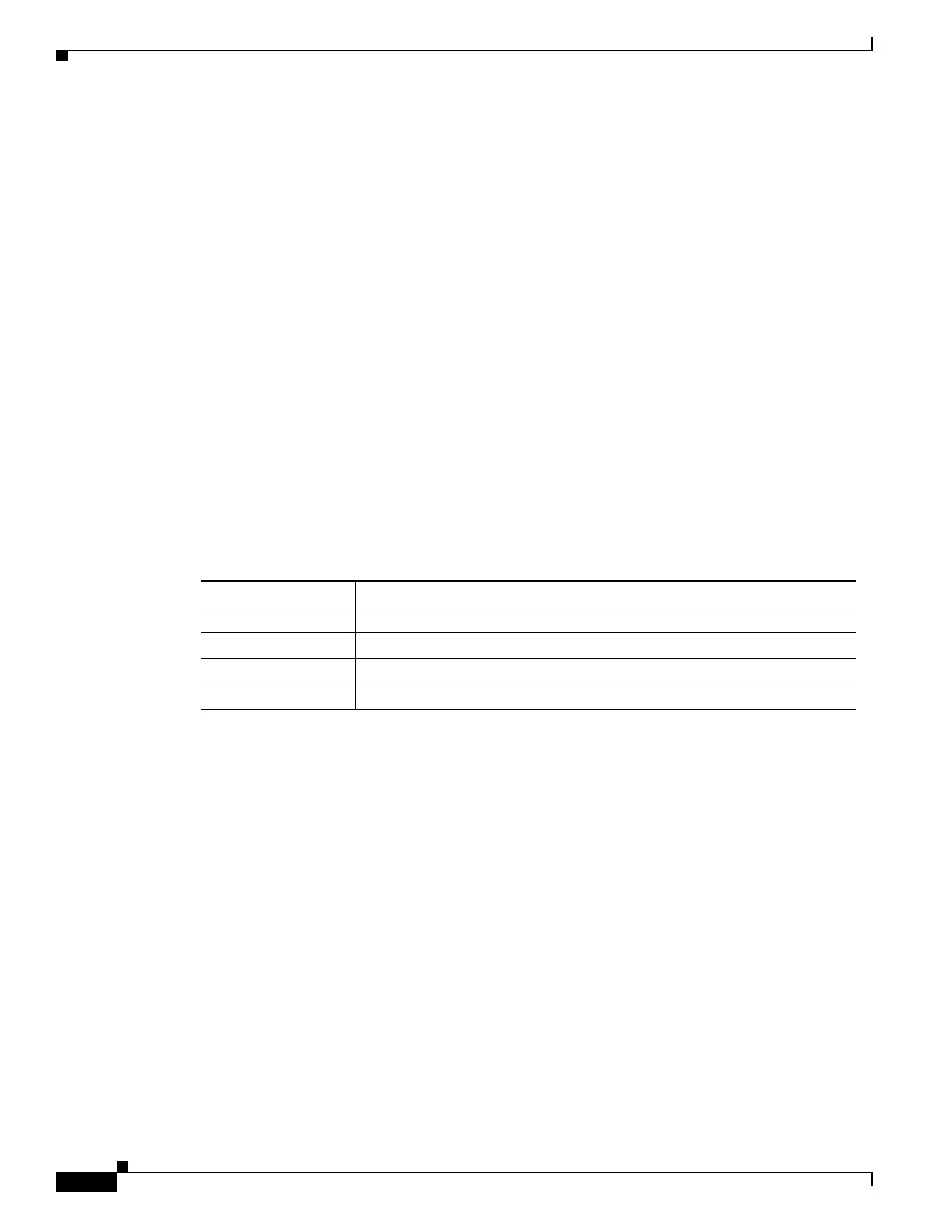
Table 49-4 CoA Commands Supported on the Switch
Command
1
1. All CoA commands must include the session identifier between the switch and the CoA client.
Cisco VSA
Reauthenticate host Cisco:Avpair=“subscriber:command=reauthenticate”
Terminate session it is a standard disconnect request that does not require a VSA.
Bounce host port Cisco:Avpair=“subscriber:command=bounce-host-port”
Disable host port Cisco:Avpair=“subscriber:command=disable-host-port”
1. Extensible Authentication Protocol over Lan

 Loading...
Loading...




















