62-4
Catalyst 4500 Series Switch, Cisco IOS Software Configuration Guide - Cisco IOS XE 3.9.xE and IOS 15.2(5)Ex
Chapter 62 Configuring Network Security with ACLs
About ACLs
ACLs permit or deny packet forwarding based on how the packet matches the entries in the ACL. For
example, you can use access lists to allow one host to access a part of a network, but prevent another
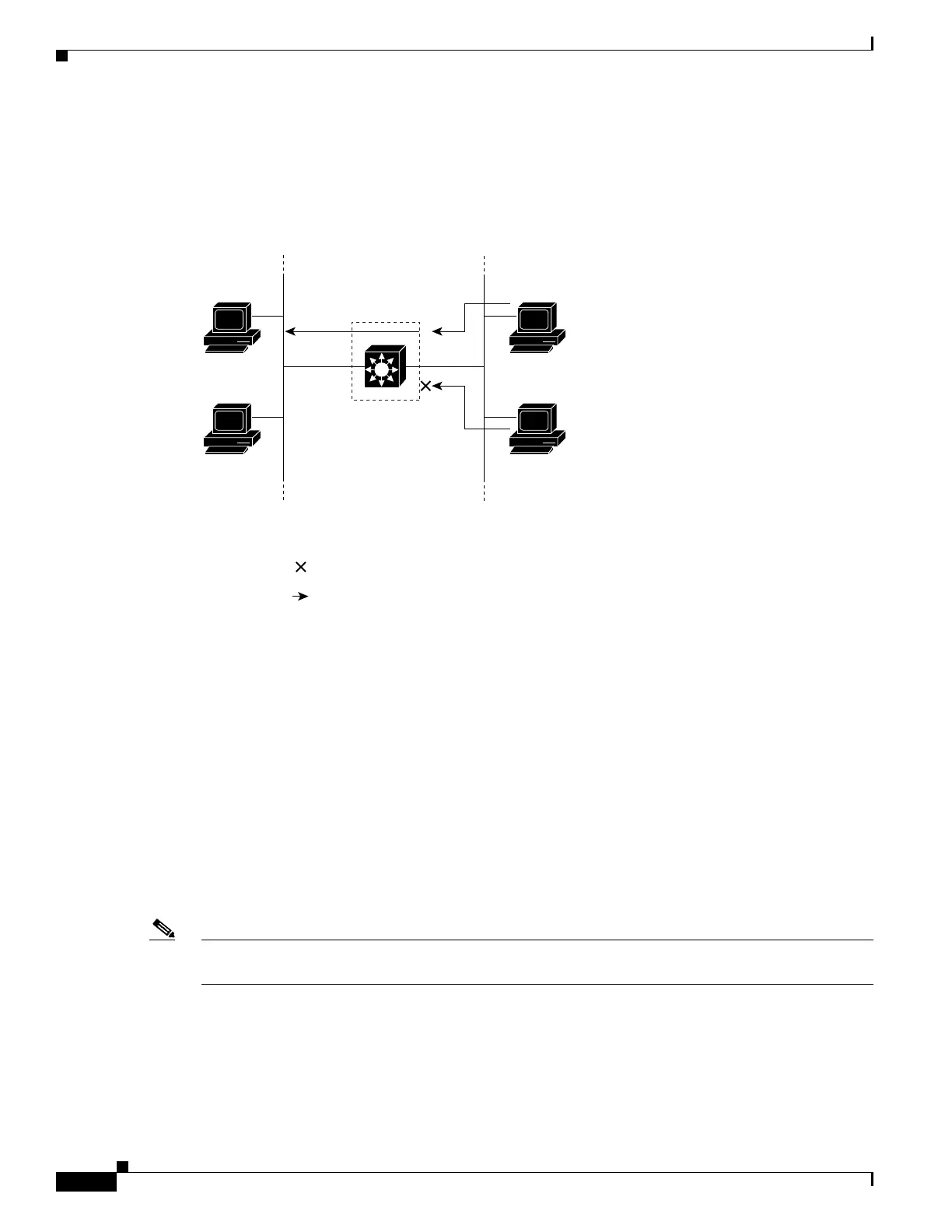
host from accessing the same part. In Figure 62-1, ACLs applied at the router input allow Host A to
access the Human Resources network, but prevent Host B from accessing the same network.
Figure 62-1 Using ACLs to Control Traffic to a Network
Port ACLs
You can also apply ACLs to Layer 2 interfaces on a switch. Port ACLs are supported on physical
interfaces and EtherChannel interfaces. The following access lists are supported on Layer 2 interfaces:
• Standard IP access lists using source addresses
• Extended IP access lists using source and destination addresses and optional protocol type
information
• IPv6 access lists using source and destination addresses and optional protocol type information
• MAC extended access lists using source and destination MAC addresses and optional protocol type
information
Note Negative TCP flags such as -syn, -psh or -fin in ACEs are not considered when you apply port ACLs,
We recommend that you use positive TCP flags in ACEs.
As with router ACLs, the switch examines ACLs associated with features configured on a given interface
and permits or denies packet forwarding based on how the packet matches the entries in the ACL. In the
example in Figure 62-1, if all workstations were in the same VLAN, ACLs applied at the Layer 2 input
would allow Host A to access the Human Resources network, but prevent Host B from accessing the
same network.
Si
Host A
Host B
94152
Research &
Development
network
= ACL denying traffic from Host B
and permitting traffic from Host A
= Packet
Catalyst 4500 series switch
Human
Resources
network

 Loading...
Loading...




















