62-17
Catalyst 4500 Series Switch, Cisco IOS Software Configuration Guide - Cisco IOS XE 3.9.xE and IOS 15.2(5)Ex
Chapter 62 Configuring Network Security with ACLs
Configuring EtherType Matching
To create a named MAC extended ACL, perform this task:
This example shows how to create and display an access list named mac1, denying only EtherType
DECnet Phase IV traffic, but permitting all other types of traffic:
Switch(config)# mac access-list extended mac1
Switch(config-ext-macl)# deny any any decnet-iv (old) protocol-family decnet (new)
Switch(config-ext-macl)# permit any any
Switch(config-ext-macl)# end
Switch # show access-lists
Extended MAC access list mac1
deny any any decnet-iv (old) protocol-family decnet (new)
permit any any
The following example shows how to enable or disable hardware statistics while configuring ACEs in
the access list:
Switch# config t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)# mac access-list extended mac1
Switch(config-ext-nacl)# hardware statistics
Switch(config-ext-nacl)# end
Switch# show access-lists
Extended MAC access list macl
deny any any decnet-iv (old) protocol-family decnet (new)
permit any any
hardware statistics
Configuring EtherType Matching
You can classify non-IP traffic based on the EtherType value using the existing MAC access list
commands. When you classify non-IP traffic by EtherType, you can apply security ACLs and QoS
policies to traffic that carry the same EtherType.
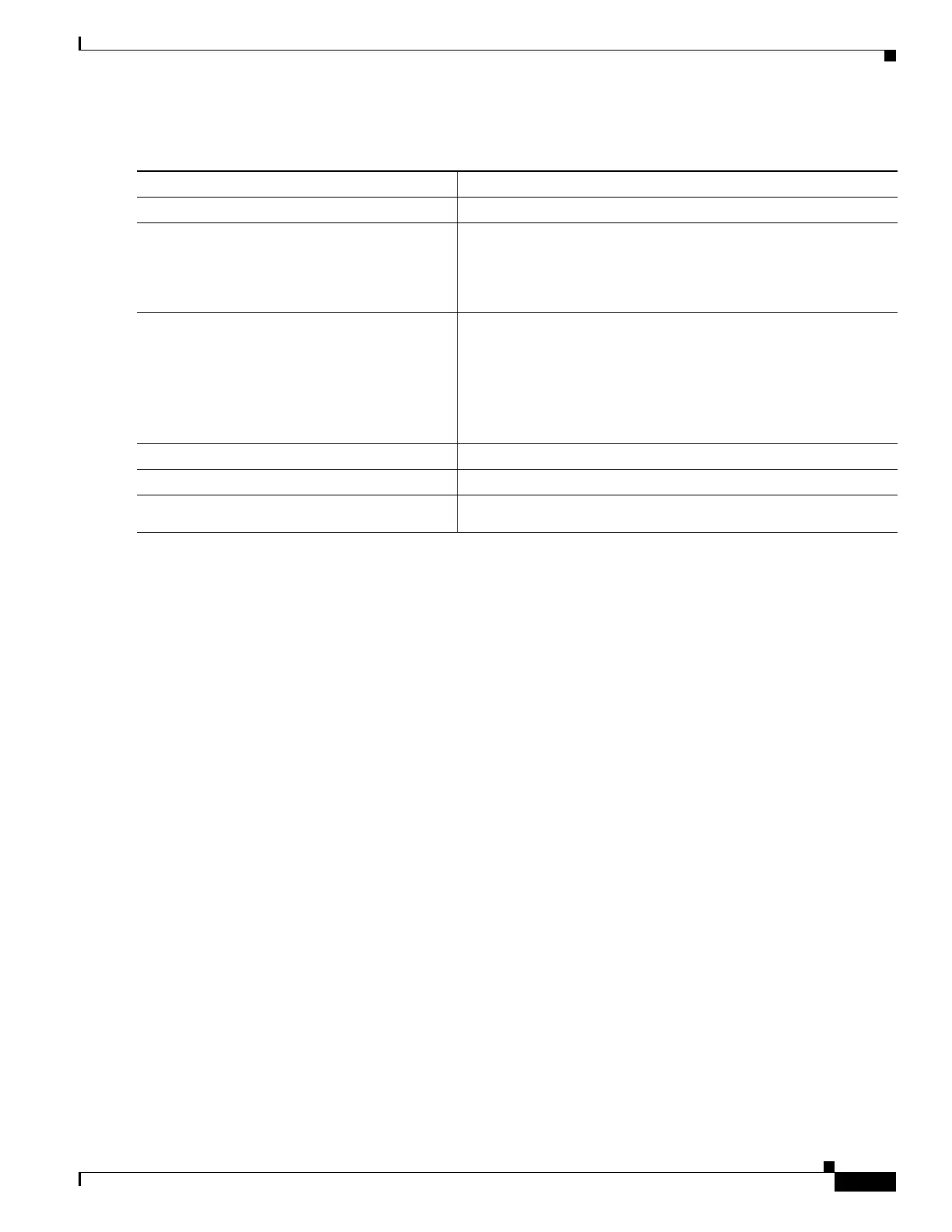
Command Purpose
Step 1
Switch# configure terminal
Enters global configuration mode.
Step 2
Switch(config)# [no] mac access-list
extended name
Defines an extended MAC access list using a name.
To delete the entire ACL, use the no mac access-list extended
name global configuration command. You can also delete
individual ACEs from named MAC extended ACLs.
Step 3
Switch(config-ext-macl)# {deny | permit}
{any | host source MAC address | source
MAC address mask} {any | host destination
MAC address | destination MAC address
mask} [protocol-family {appletalk |
arp-non-ipv4 | decnet | ipx | ipv6 (not
supported on Sup 6-E and 6L-E)| rarp-ipv4
| rarp-non-ipv4 | vines | xns]
In extended MAC access-list configuration mode, specify to
permit or deny any source MAC address, a source MAC address
with a mask, or a specific host source MAC address and any
destination MAC address, destination MAC address with a mask,
or a specific destination MAC address.
Note IPv6 packets do not generate Layer 2 ACL lookup keys.
Step 4
Switch(config-ext-macl)# end
Returns to privileged EXEC mode.
Step 5
Switch# show access-lists [number | name]
Shows the access list configuration.
Step 6
Switch(config)# copy running-config
startup-config
(Optional) Saves your entries in the configuration file.

 Loading...
Loading...




















