49-26
Catalyst 4500 Series Switch, Cisco IOS Software Configuration Guide - Cisco IOS XE 3.9.xE and IOS 15.2(5)Ex
Chapter 49 Configuring 802.1X Port-Based Authentication
Configuring 802.1X Port-Based Authentication
is detected. To force the switch to deploy the Guest VLAN in the case of a protocol timeout, configure dot1x guest-vlan
supplicant globally. If the port is configured for hostmode multi-domain authentication, the switch behaves as if dot1x
guest-vlan supplicant is configured.
Supported Topologies
The 802.1X port-based authentication supports two topologies:
• Point-to-point
• Wireless LAN
In a point-to-point configuration (see Figure 49-1 on page 49-3), only one client can be connected to the 802.1X-enabled switch
port when the multiple- host mode is not enabled (the default). The switch detects the client when the port link state changes
to the up state. If a client leaves or is replaced with another client, the switch changes the port link state to down, and the port
returns to the unauthorized state.
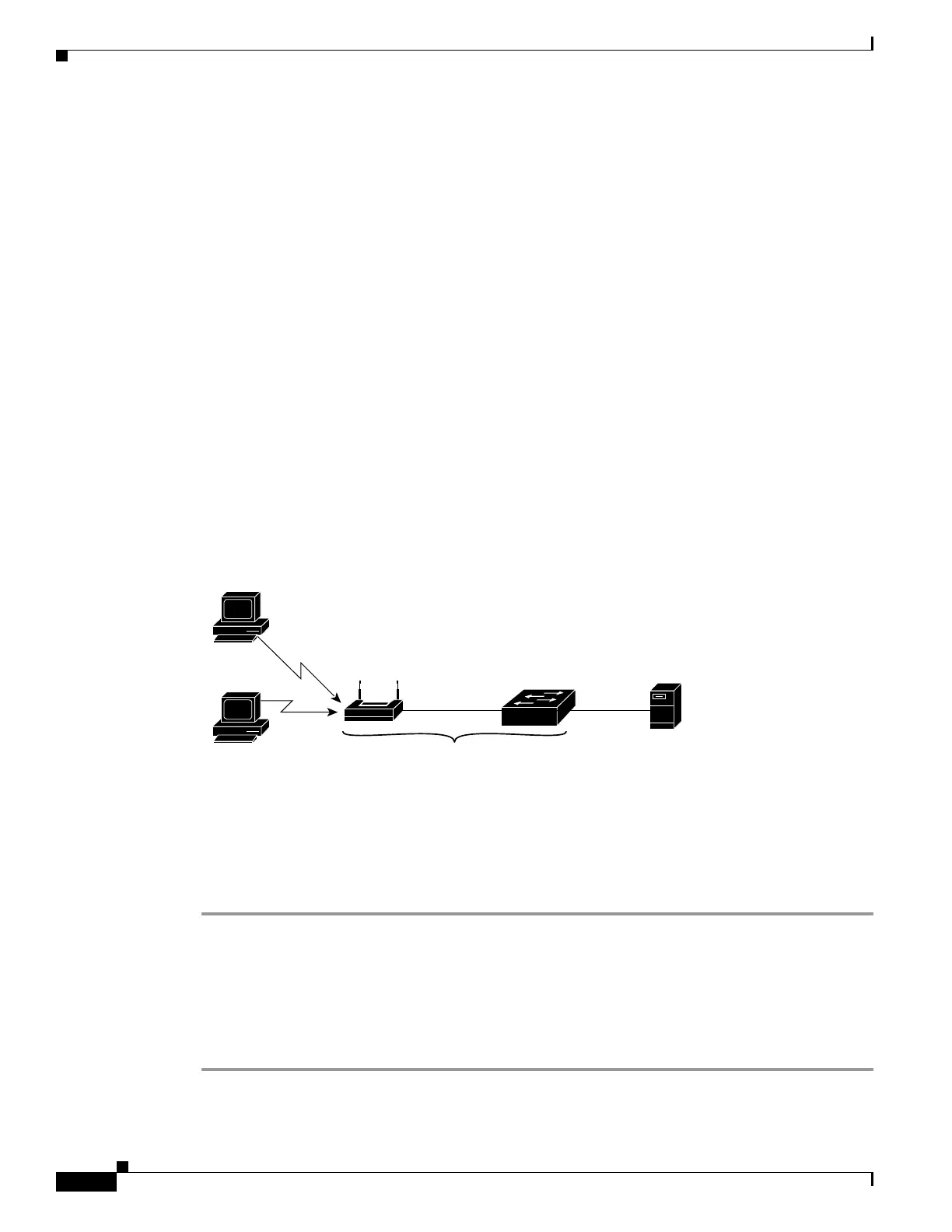
For 802.1X port-based authentication in a wireless LAN (Figure 49-9), you must configure the 802.1X port as a multiple-host
port that is authorized as a wireless access point once the client is authenticated. (See the “Resetting the 802.1X Configuration
to the Default Values” section on page 49-95.) When the port is authorized, all other hosts that are indirectly attached to the
port are granted access to the network. If the port becomes unauthorized (reauthentication fails or an EAPOL-logoff message
is received), the switch denies access to the network for all wireless access point-attached clients. In this topology, the wireless
access point is responsible for authenticating clients attached to it, and the wireless access point acts as a client to the switch.
Figure 49-9 Wireless LAN Example
Configuring 802.1X Port-Based Authentication
To configure 802.1X, follow this procedure:
Step 1 Enable 802.1X authentication. See the “Enabling 802.1X Authentication” section on page 49-29.
Step 2 Configure switch to RADIUS server communication. See the “Configuring Switch-to-RADIUS-Server
Communication” section on page 49-32.
Step 3 Adjust the 802.1X timer values. See the “Changing the Quiet Period” section on page 49-84.
Step 4 Configure optional features. See the “Configuring RADIUS-Provided Session Timeouts” section on
page 49-53.
Wireless
clients
Wireless
access point
Catalyst 4500 Network
Access Switch
RADIUS
94160
Authenticator Authentication server
Supplicants

 Loading...
Loading...




















