49-38
Catalyst 4500 Series Switch, Cisco IOS Software Configuration Guide - Cisco IOS XE 3.9.xE and IOS 15.2(5)Ex
Chapter 49 Configuring 802.1X Port-Based Authentication
Configuring 802.1X Port-Based Authentication
Configuring Limiting Login for Users
Configuring 802.1X Authentication with ACL Assignments and Redirect URLs
This section includes these topics:
• Downloadable ACL, page 49-38
• URL-Redirect, page 49-42
• Configuring a Downloadable Policy, page 49-44
Downloadable ACL
The downloadable ACL (DACL) feature allows you to download device specific authorization policies from the authentication
server. These policies activate after authentication succeeds for the respective client and the client’s IP address was populated
in the IP device tracking table. (Downloadable ACL is applied on the port, once the port is authenticated and the IP device
tracking table has the host IP address entry).
The following sections describe the configuration that is necessary to complement the related authentication (802.1X or MAB)
configuration. (No unique configuration is required on the switch. All of the configuration is on the ACS.) After authentication
succeeds, enter the show ip access-list command to display the downloadable ACLs.
Configuring the Switch for Downloadable ACL
To configure the switch for downloadable ACL, follow these steps:
Step 1 Configure the IP device tracking table.
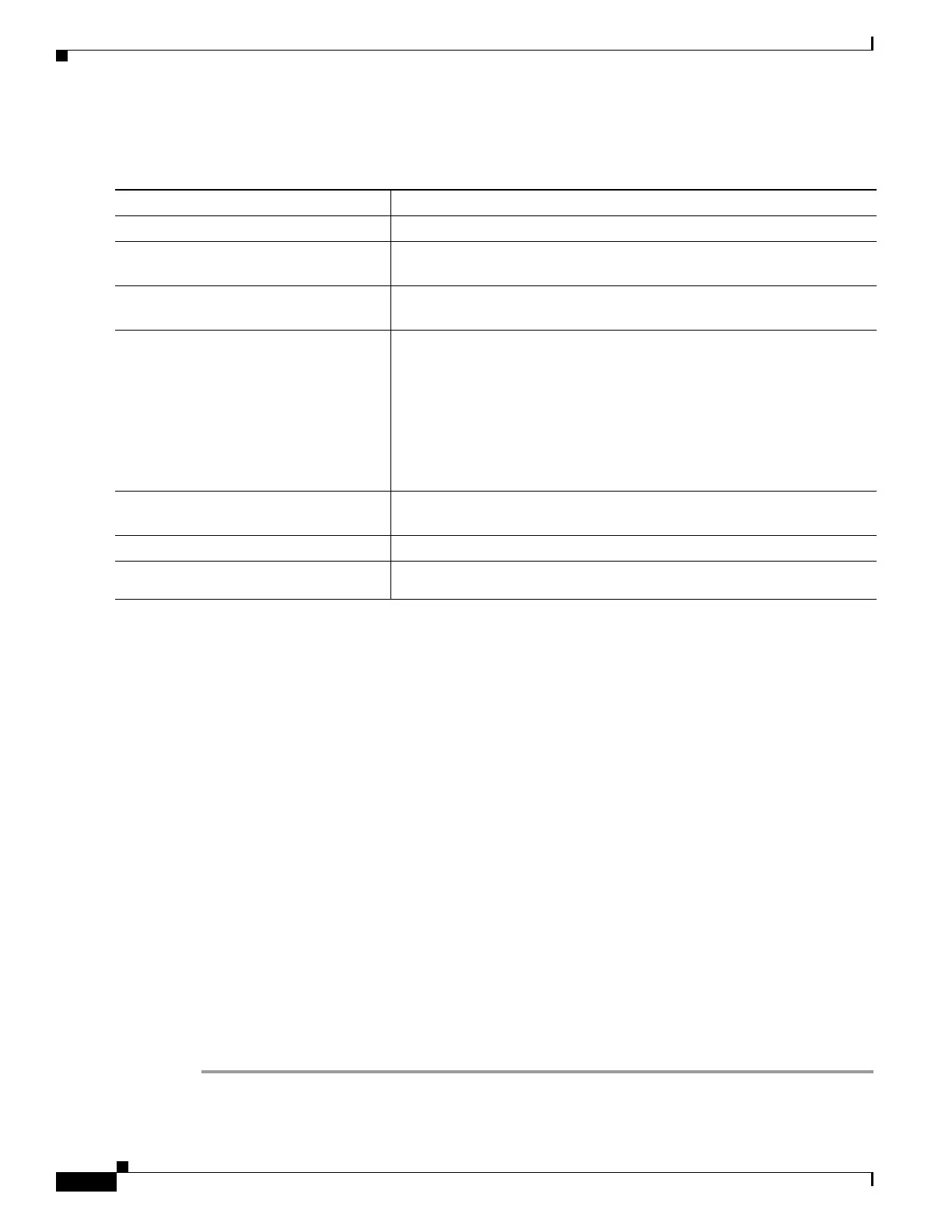
Command Purpose
Step 1
Switch# configure terminal
Enters global configuration mode.
Step 2
Switch(config)# aaa new-model
Enables the authentication, authorization, and accounting (AAA) access
control model.
Step 3
Switch(config)# aaa authentication
login default local
Sets the authentication, authorization, and accounting (AAA)
authentication by using the default authentication methods.
Step 4
Switch(config)# aaa authentication
rejected n in m ban x
Configures the time period for which an user is blocked, if the user fails
to successfully login within the specified time and login attempts.
• n—Specifies the number of times a user can try to login.
• m—Specifies the number of seconds within which an user can try to
login.
• x—Specifies the time period an user is banned if the user fails to
successfully login.
Step 5
Switch(config)# end
Exits from global configuration mode and returns to privileged EXEC
mode.
Step 6
Switch# show aaa local user blocked
Displays the list of local users who were blocked.
Step 7
Switch# clear aaa local user
blocked username username
Clears the information about the blocked local user.

 Loading...
Loading...




















