AES hardware accelerator (AES) RM0367
438/1043 RM0367 Rev 7
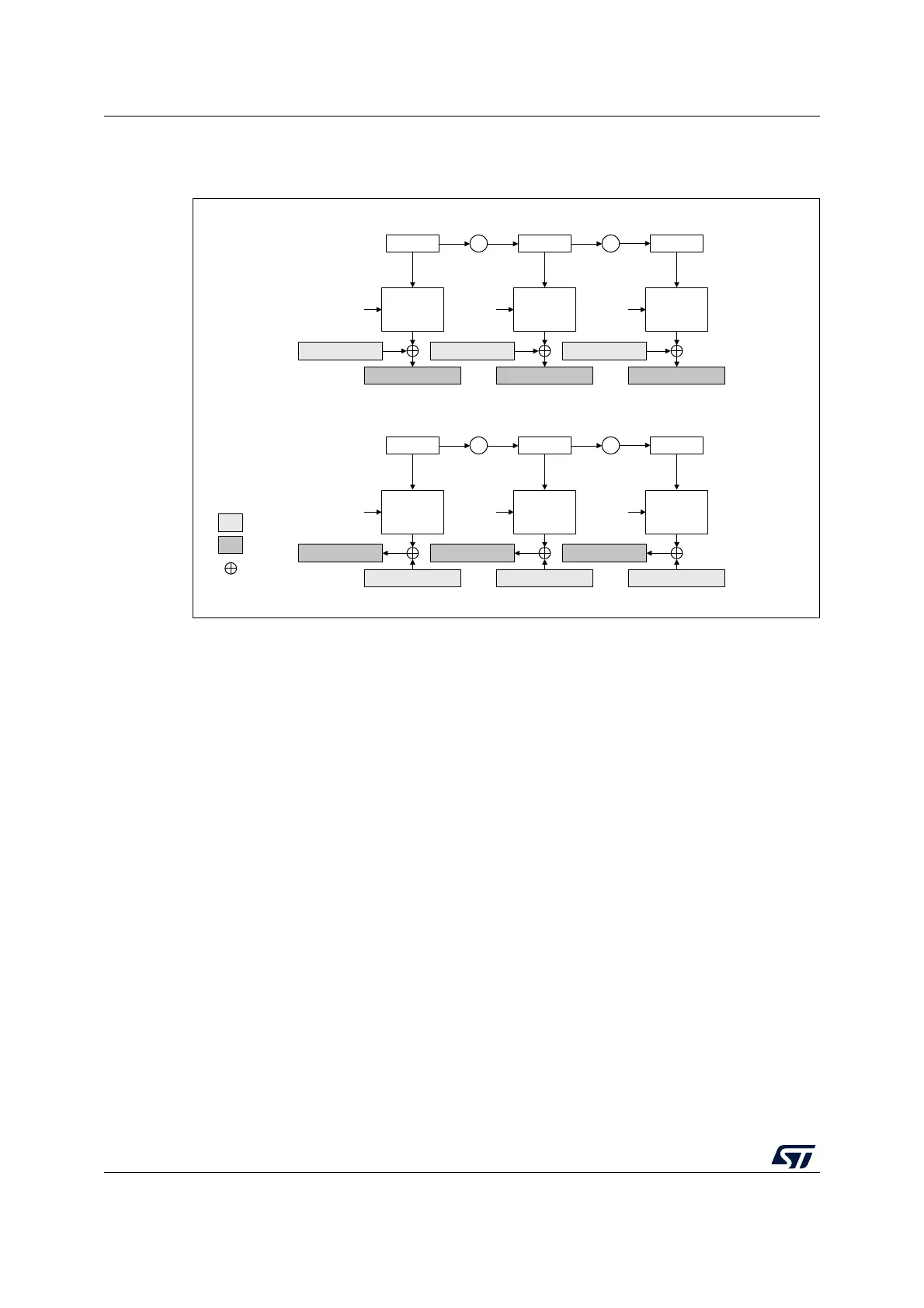
Counter (CTR) mode
Figure 87. CTR encryption and decryption principle
The CTR mode uses the AES core to generate a key stream. The keys are then XORed
with the plaintext to obtain the ciphertext as specified in NIST Special Publication 800-38A,
Recommendation for Block Cipher Modes of Operation.
Note: Unlike with ECB and CBC modes, no key scheduling is required for the CTR decryption,
since in this chaining scheme the AES core is always used in encryption mode for producing
the key stream, or counter blocks.
19.4.4 AES procedure to perform a cipher operation
Introduction
A typical cipher operation is explained below. Detailed information is provided in sections
starting from Section 19.4.8: AES basic chaining modes (ECB, CBC).
The flowcharts shown in Figure 88 describe the way STM32 cryptographic library
implements the AES algorithm. AES accelerates the execution of the AES-128
cryptographic algorithm in ECB, CBC, and CTR operating modes.
Note:
For more details on the cryptographic library, refer to the UM1924 user manual
“STM32 crypto library
” available from www.st.com.
MSv42142V1
Encryption
Plaintext block 1
Ciphertext block 1 Ciphertext block 2 Ciphertext block 3
Encrypt Encrypt Encrypt
Decryption
Ciphertext block 1 Ciphertext block 2 Ciphertext block 3
Decrypt Decrypt Decrypt
input
output
Legend
key key key
key key key
Plaintext block 2 Plaintext block 3
Counter Counter Counter
+1 +1
Plaintext block 1 Plaintext block 2 Plaintext block 3
Counter Counter Counter
+1 +1
XOR
value value + 1 value + 2
value value + 1 value + 2

 Loading...
Loading...