RM0367 Rev 7 445/1043
RM0367 AES hardware accelerator (AES)
466
second-block plaintext data P2’ to produce the I2 input data for the AES core to produce the
second block of ciphertext data. The chaining of data blocks continues in this way until the
last plaintext block in the message is encrypted.
If the message size is not a multiple of 128 bits, the final partial data block is encrypted in
the way explained in Section 19.4.6: AES ciphertext stealing and data padding.
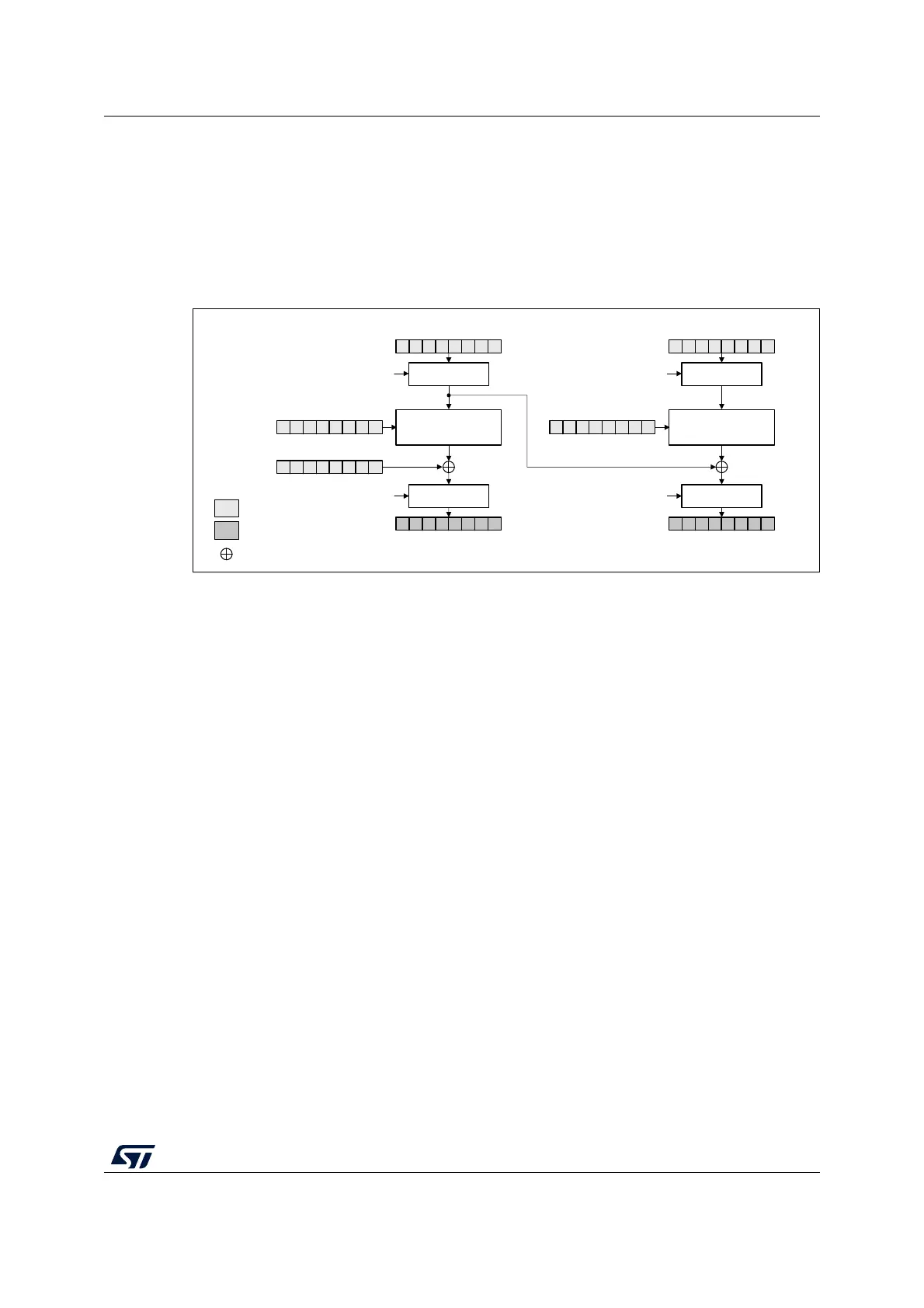
Figure 94 illustrates the cipher block chaining (CBC) decryption mode.
Figure 94. CBC decryption
In CBC decrypt mode, like in ECB decrypt mode, the secret key must be prepared to
perform an AES decryption.
After the key preparation process, the decryption goes as follows: the first 128-bit ciphertext
block (after the swap operation) is used directly as the AES core input block I1 for decrypt
operation, using the 128-bit key. Its output O1 is XOR-ed with the 128-bit IVI field (that must
be identical to that used during encryption) to produce the first plaintext block P1.
The second ciphertext block is processed in the same way as the first block, except that the
I1 data from the first block is used in place of the initialization vector.
The decryption continues in this way until the last complete ciphertext block is decrypted.
If the message size is not a multiple of 128 bits, the final partial data block is decrypted in
the way explained in Section 19.4.6: AES ciphertext stealing and data padding.
For more information on data swapping, refer to Section 19.4.10: AES data registers and
data swapping.
MSv19104V2
Decrypt
AES_KEYRx (KEY)
AES_DINR (ciphertext C1)
AES_DOUTR (plaintext P1)
Swap
management
DATATYPE[1:0]
DATATYPE[1:0]
Swap
management
Decrypt
AES_KEYRx (KEY)
AES_DINR (ciphertext C2)
AES_DOUTR (plaintext P2)
Swap
management
DATATYPE[1:0]
DATATYPE[1:0]
Swap
management
AES_IVRx (IV)
input
output
Legend
XOR
I1
I2
O1
O2
Block 1 Block 2
IVI
P1'
P2'
 Loading...
Loading...