AES hardware accelerator (AES) RM0367
442/1043 RM0367 Rev 7
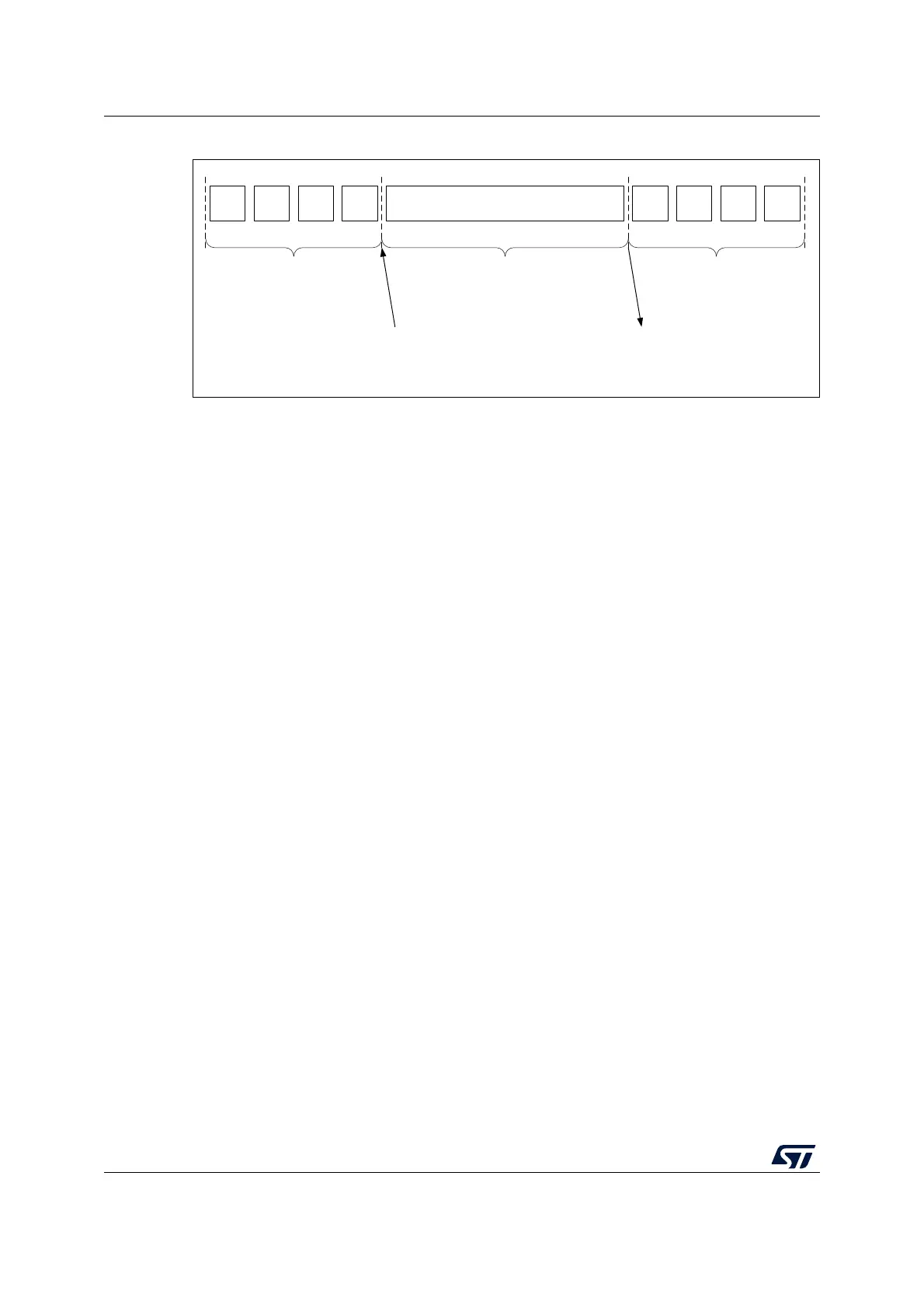
Figure 89. Encryption key derivation for ECB/CBC decryption (Mode 2)
If the software stores the initial key prepared for decryption, it is enough to do the key
schedule operation only once for all the data to be decrypted with a given cipher key.
Note: Alternative key preparation is to select Mode 4 by setting to 11 the MODE[1:0] bitfield of the
AES_CR register. In this case Mode 3 cannot be used.
19.4.6 AES ciphertext stealing and data padding
When using AES in ECB or CBC modes to manage messages the size of which is not a
multiple of the block size (128 bits), ciphertext stealing techniques are used, such as those
described in NIST Special Publication 800-38A, Recommendation for Block Cipher Modes
of Operation: Three Variants of Ciphertext Stealing for CBC Mode. Since the AES peripheral
on the device does not support such techniques, the last two blocks of input data must be
handled in a special way by the application.
Note: Ciphertext stealing techniques are not documented in this reference manual.
Similarly, when AES is used in other modes than ECB or CBC, an incomplete input data
block (that is, block with input data shorter than 128 bits) must be padded with zeros prior to
encryption (that is, extra bits must be appended to the trailing end of the data string). After
decryption, the extra bits must be discarded. As AES does not implement automatic data
padding operation to the last block, the application must follow the recommendation given
in Section 19.4.4: AES procedure to perform a cipher operation on page 438 to manage
messages the size of which is not a multiple of 128 bits.
Note: Padding data are swapped in a similar way as normal data, according to the
DATATYPE[1:0] field of the AES_CR register (see Section 19.4.10: AES data registers and
data swapping on page 451 for details).
19.4.7 AES task suspend and resume
A message can be suspended if another message with a higher priority must be processed.
When this highest priority message is sent, the suspended message can resume in both
encryption or decryption mode.
Suspend/resume operations do not break the chaining operation and the message
processing can resume as soon as AES is enabled again to receive the next data block.
Figure 90 gives an example of suspend/resume operation: Message 1 is suspended in
order to send a shorter and higher-priority Message 2.
MS18937V2
WR
EK3
WR
EK2
WR
EK1
WR
EK0
Wait until flag CCF = 1
RD
DK3
RD
DK2
RD
DK1
RD
DK0
Input phase
4 write operations into
AES_KEYRx[31:0]
Computation phase
Output phase (optional)
4 read operations of
AES_KEYRx[31:0]
EK = encryption key = 4 words (EK3, … , EK0)
DK = decryption key = 4 words (DK3, … , DK0)
MSB LSB MSB LSB
EN = 1 into AES_CR
128-bit derivation key
stored into AES_KEYRx

 Loading...
Loading...