Programmer’s Model
ARM DDI 0301H Copyright © 2004-2009 ARM Limited. All rights reserved. 2-3
ID012310 Non-Confidential, Unrestricted Access
2.2 Secure world and Non-secure world operation with TrustZone
This section describes;
• TrustZone model
• How the Secure model works on page 2-4.
For more details on TrustZone and the ARM architecture, see the ARM Architecture Reference
Manual.
2.2.1 TrustZone model
The basis of the TrustZone model is that the computing environment splits into two isolated
worlds, the Secure world and the Non-secure world, with no leakage of Secure data to the
Non-secure world. Software Secure Monitor code, running in the Secure Monitor Mode, links
the two worlds and acts as a gatekeeper to manage program flow. The system can have both
Secure and Non-secure peripherals that suitable Secure and Non-secure device drivers control.
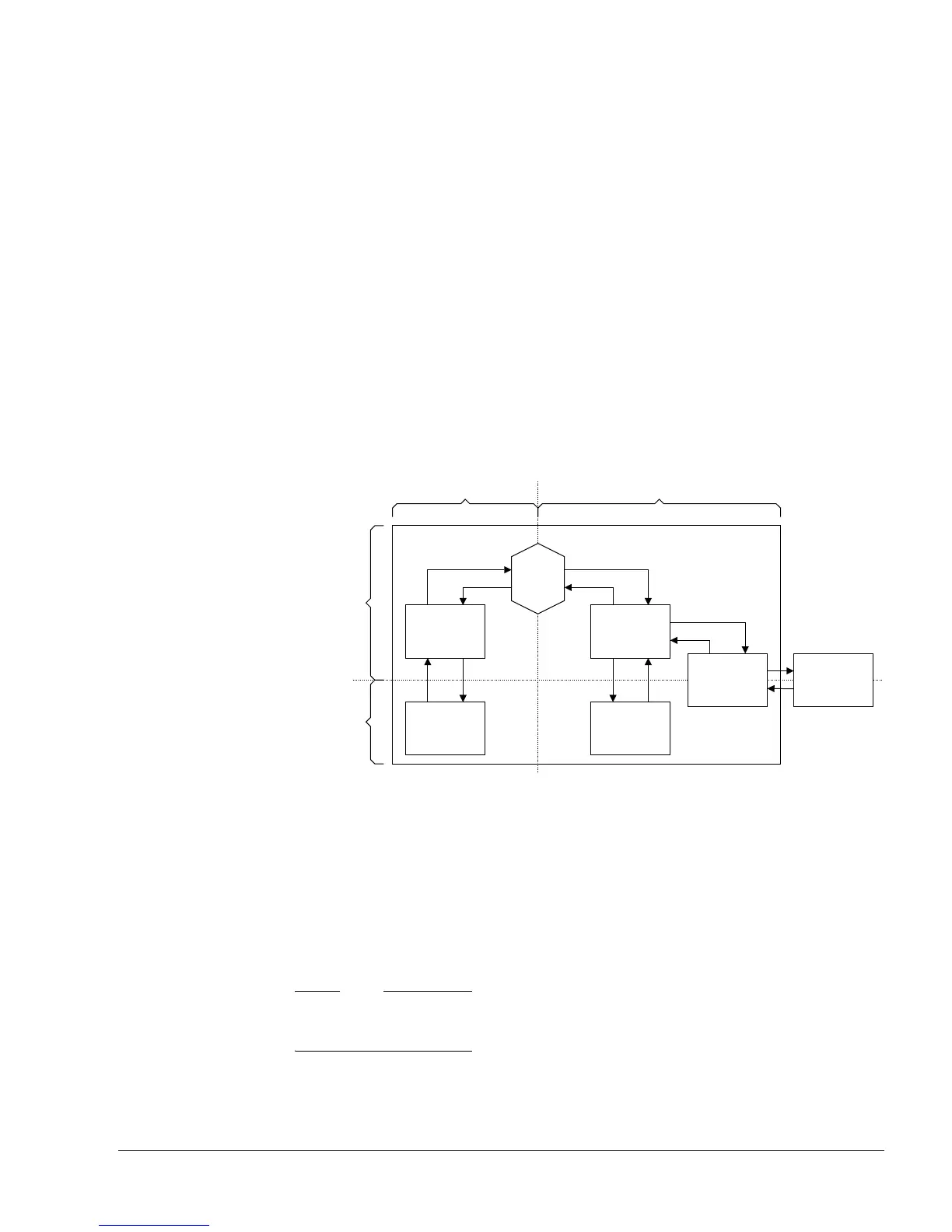
Figure 2-1 shows the relationship between the Secure and Non-secure worlds. The Operating
System (OS) splits into the Secure OS, that includes the Secure kernel, and the Non-secure OS,
that includes the Non-secure kernel. For details on modes of operation, see Operating modes on
page 2-17.
Figure 2-1 Secure and Non-secure worlds
In normal Non-secure operation the OS runs tasks in the usual way. When a User process
requires Secure execution it makes a request to the Non-secure kernel, that operates in privileged
mode, and this calls the Secure Monitor to transfer execution to the Secure world.
This approach to secure systems means that the platform OS, that works in the Non-secure
world, has only a few fixed entry points into the Secure world through the Secure Monitor. The
trusted code base for the Secure world, that includes the Secure kernel and Secure device
drivers, is small and therefore much easier to maintain and verify.
Note
Software that runs in User mode cannot directly switch the world that it operates in. Changes
from one world to the other can only occur through the Secure Monitor mode.
Non-secure
kernel
Secure
kernel
Non-secure
application
Secure
tasks
Secure
device driver
Secure
device
Non-secure Secure
Privileged modesUser mode
Fixed entry
points
Fixed entry
points
Monitor
 Loading...
Loading...