Operation Manual – SSH Terminal Service
H3C S3600 Series Ethernet Switches-Release 1510 Chapter 1
SSH Terminal Service
1-2
Local switch
Local Ethernet
WANServer
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WANServer
PC
SSH
PC
Laptop
Laptop
WANServer
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Rem
Remote sw itch
SSH
ote Ethernet
Server
WANServer
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WANServer
PC
SSH
PC
Laptop
Laptop
WANServer
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Rem
SSH
ote Ethernet
Server
Local switch
Local Ethernet
WANServer
PC
SSH
PC
Laptop
Laptop
Local switch
Local Ethernet
WANServer
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WAN
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WANServer
PC
SSH
PC
Laptop
Laptop
WANServer
PC
SSH
PC
Laptop
Laptop
WANServer
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Rem
Remote sw itch
SSH
ote Ethernet
Server
WANServer
PC
SSH
Workstation
Workstation
Rem
Remote sw itch
SSH
ote Ethernet
Server
WANServer
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WANServer
PC
SSH
PC
Laptop
Workstation
Remote Ethernet
Server
WANServer
PC
SSH
PC
Laptop
Laptop
WANServer
PC
SSH
PC
Laptop
Laptop
WANServer
PC
SSH Client
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Rem
SSH Server
ote Ethernet
Server
Local switch
Local Ethernet
WANServer
PC
SSH
PC
Laptop
Laptop
Local switch
Local Ethernet
WANServer
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WAN
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WANServer
PC
SSH
PC
Laptop
Laptop
WANServer
PC
SSH
PC
Laptop
Laptop
WANServer
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Rem
Remote sw itch
SSH
ote Ethernet
Server
WANServer
PC
SSH
Workstation
Workstation
Rem
Remote sw itch
SSH
ote Ethernet
Server
WANServer
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WANServer
PC
SSH
PC
Laptop
Workstation
Remote Ethernet
Server
WANServer
PC
SSH
PC
Laptop
Laptop
WANServer
PC
SSH
PC
Laptop
Laptop
WANServer
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Rem
SSH
ote Ethernet
Server
Local switch
Local Ethernet
WANServer
PC
SSH
PC
Laptop
Laptop
Local switch
Local Ethernet
WANServer
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WAN
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WANServer
PC
SSH
PC
Laptop
Laptop
WANServer
PC
SSH
PC
Laptop
Laptop
WANServer
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Server
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Rem
Remote sw itch
SSH
ote Ethernet
Server
WANServer
PC
SSH
Workstation
Workstation
Rem
Remote sw itch
SSH
ote Ethernet
Server
WANServer
PC
SSH
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Remote Ethernet
Server
WANServer
PC
SSH
PC
Laptop
Workstation
Remote Ethernet
Server
WANServer
PC
SSH
PC
Laptop
Laptop
WANServer
PC
SSH
PC
Laptop
Laptop
WANServer
PC
SSH Client
PC
Laptop
Laptop
PC
Laptop
Laptop
Workstation
Workstation
Rem
SSH Server
ote Ethernet
Server
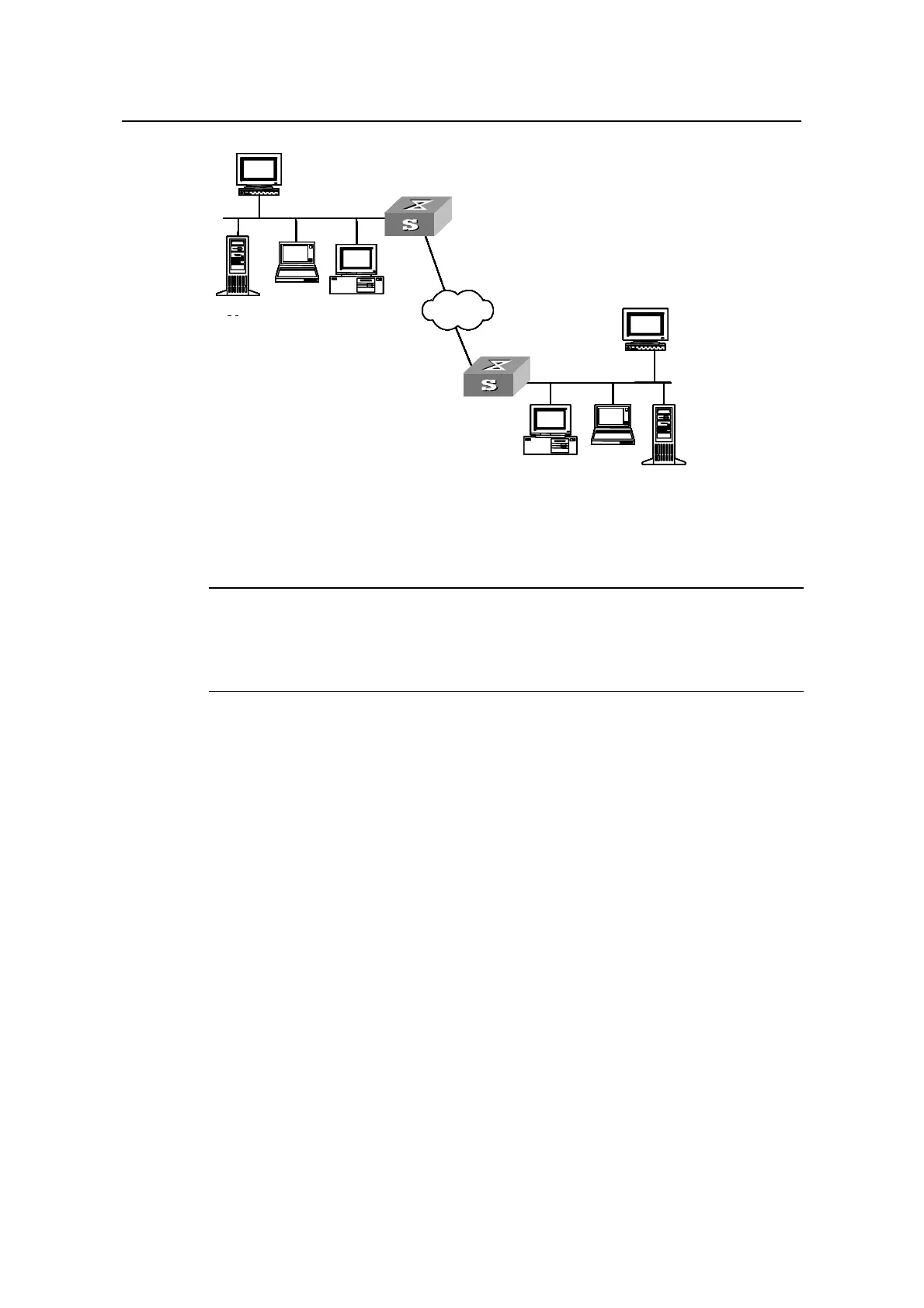
Figure 1-2 Establish SSH connection through a WAN
Note:
At present, the device supports two SSH versions: SSH2 and SSH1. Unless otherwise
noted, SSH refers to SSH2 throughout this document.
The communication process between a SSH client and server goes through the
following five stages.
1) Version negotiation stage:
z The client sends a TCP connection request to the server.
z When a TCP connection is established, the two ends begin to negotiate an SSH
version.
z If they get a successful negotiation, they go to the key negotiation stage.
Otherwise the server terminates the TCP connection.
2) Key and algorithm negotiation stage:
z The server and the client send key algorithm negotiation packets to each other,
which include the supported server-side public key algorithm list, encryption
algorithm list, MAC algorithm list, and compression algorithm list.
z Based on the received algorithm negotiation packets, the server and the client
figure out the algorithms to be used.
z The server and the client use the DH key exchange algorithm and parameters
such as the host key pair to generate the session key and session ID.

 Loading...
Loading...