RUGGEDCOM ROX II
CLI User Guide
Chapter 12
Tunneling and VPNs
Example: Configuring an Encrypted VPN Tunnel 423
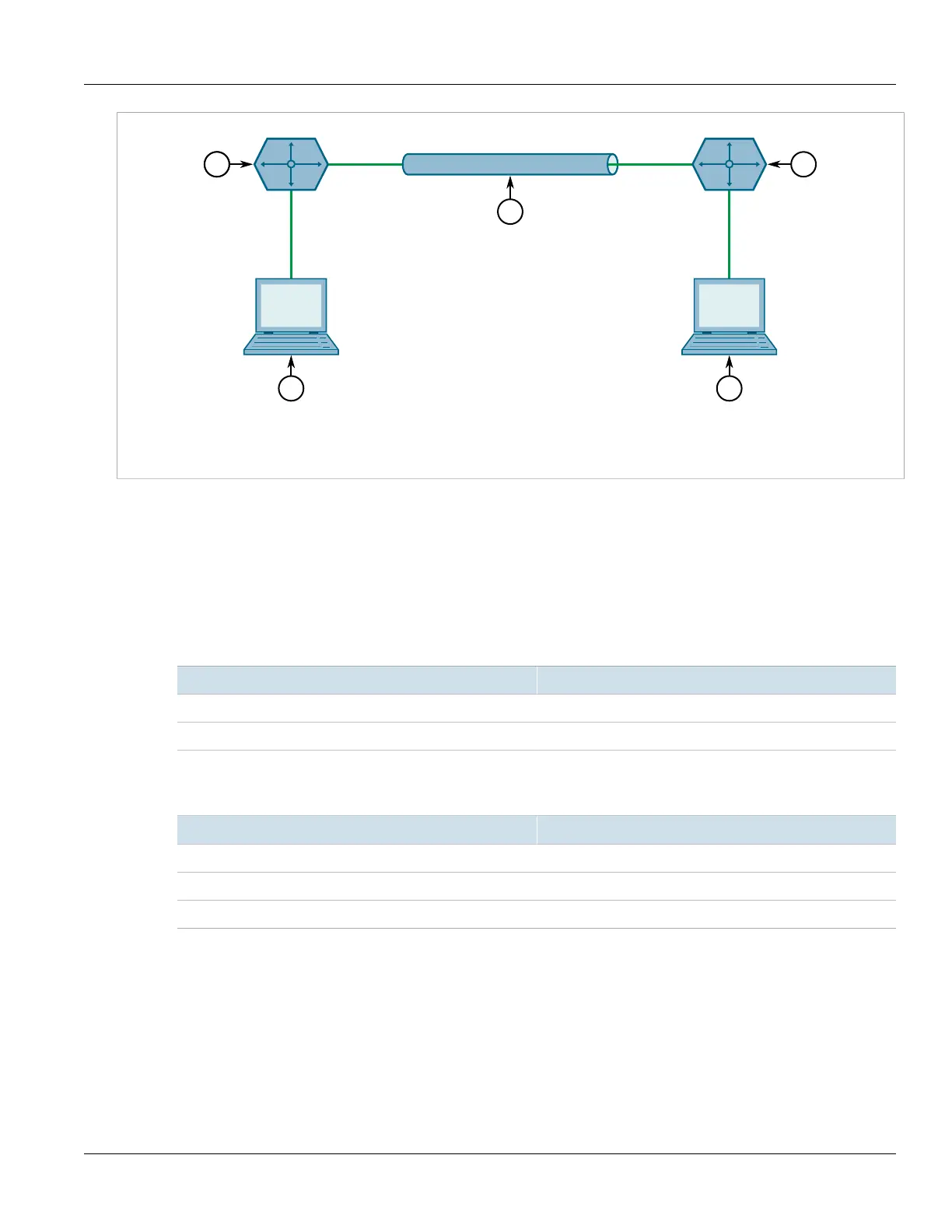
192.168.50.1/24
192.168.50.100/24
2.2.2.1/30 2.2.2.2/30
192.168.60.1/24
192.168.60.100/24
Figure19:Topology – Site-to-Site Encrypted VPN Tunnel with a Pre-Shared Key
1.Device A 2.IPsec Encrypted VPN Tunnel 3.Device B 4.Client 1 5.Client 2
To configure a VPN tunnel, do the following:
1. Configure a connection name for the VPN. For more information, refer to Section12.8.6.2, “Adding a
Connection”.
2. Configure Device A:
a. Configure a host name for the device. For more information, refer to Section5.2, “Configuring the Host
Name”.
b. Add a unique pre-shared key and configure the following parameters:
Parameter Value
Local Address 2.2.2.1/30
Remote Address 2.2.2.2/30
For more information, refer to Section12.8.5.2, “Adding a Pre-Shared Key”.
c. Add an IPsec connection and configure the following parameters:
Parameter Value
Startup Operation start
Authenticate By secret
Connection Type tunnel
For more information about IPsec connections, refer to Section12.8.6.2, “Adding a Connection”.
d. Configure an Internet Key Exchange (IKE) algorithm with default values. For more information, refer to
Section12.8.7.2, “Adding an IKE Algorithm”.
e. Configure an Encapsulated Security Payload (ESP) algorithm with default values. For more information,
refer to Section12.8.8.3, “Adding an ESP Algorithm”.
f. Configure the left connection end for the IPsec tunnel with the following public IP address parameters:

 Loading...
Loading...











