RM0444 Rev 5 491/1390
RM0444 AES hardware accelerator (AES)
522
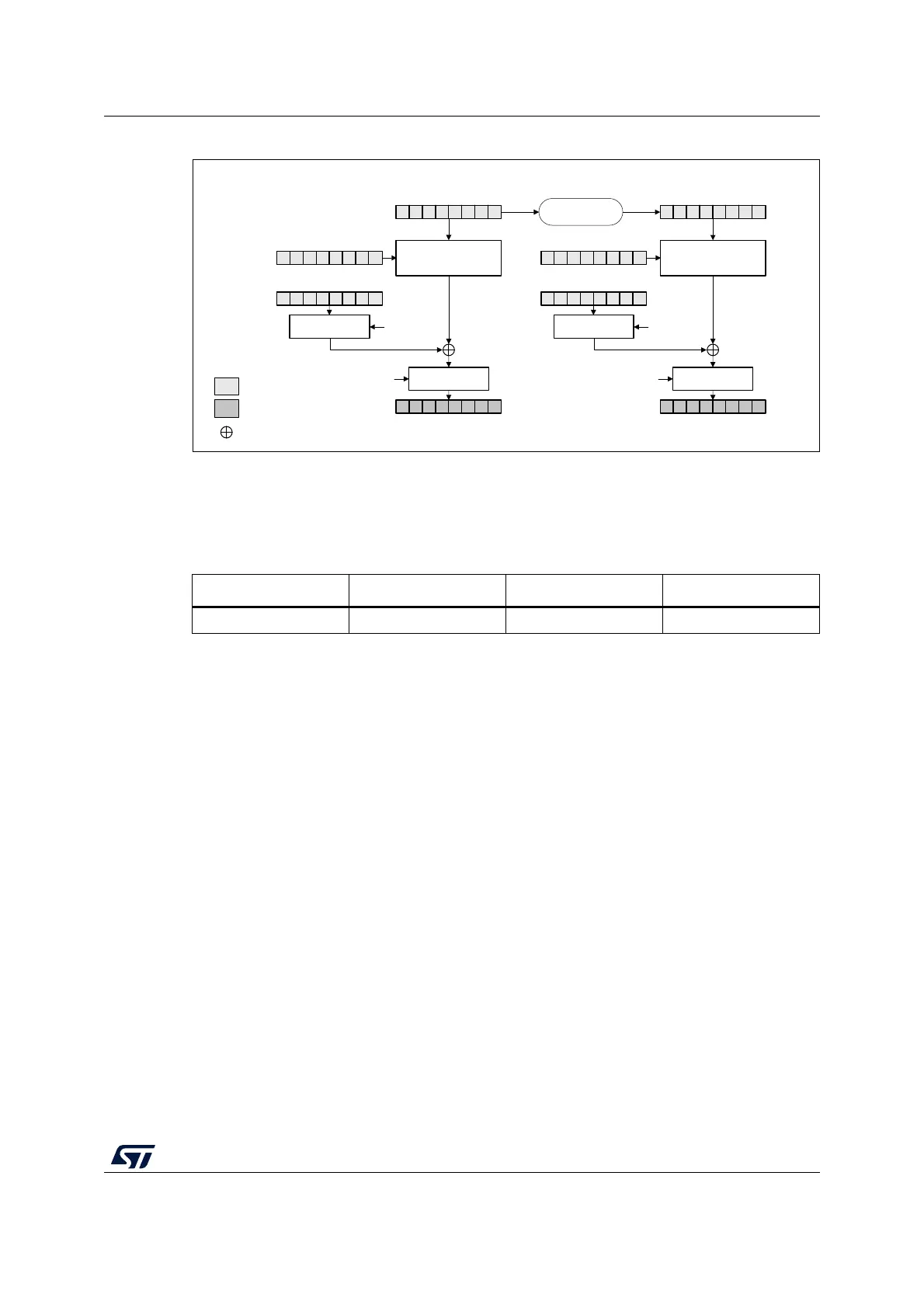
Figure 91. CTR decryption
In CTR mode, the cryptographic core output (also called keystream) Ox is XOR-ed with
relevant input block (Px' for encryption, Cx' for decryption), to produce the correct output
block (Cx' for encryption, Px' for decryption). Initialization vectors in AES must be initialized
as shown in Table 103.
Unlike in CBC mode that uses the AES_IVRx registers only once when processing the first
data block, in CTR mode AES_IVRx registers are used for processing each data block, and
the AES peripheral increments the counter bits of the initialization vector (leaving the nonce
bits unchanged).
CTR decryption does not differ from CTR encryption, since the core always encrypts the
current counter block to produce the key stream that is then XOR-ed with the plaintext (CTR
encryption) or ciphertext (CTR decryption) input. In CTR mode, the MODE[1:0] bitfield
setting 01 (key derivation) is forbidden and all the other settings default to encryption mode.
The sequence of events to perform an encryption or a decryption in CTR chaining mode:
1. Ensure that AES is disabled (the EN bit of the AES_CR must be 0).
2. Select CTR chaining mode by setting to 010 the CHMOD[2:0] bitfield of the AES_CR
register. Set MODE[1:0] bitfield to any value other than 01.
3. Initialize the AES_KEYRx registers, and load the AES_IVRx registers as described in
Table 103.
4. Set the EN bit of the AES_CR register, to start encrypting the current counter (EN is
automatically reset when the calculation finishes).
5. If it is the last block, pad the data with zeros to have a complete block, if needed.
6. Append data in AES, and read the result. The three possible scenarios are described in
Section 20.4.4: AES procedure to perform a cipher operation.
7. Repeat the previous step till the second-last block is processed. For the last block,
apply the two previous steps and discard the bits that are not part of the payload (if the
size of the significant data in the last input block is less than 16 bytes).
Table 103. CTR mode initialization vector definition
AES_IVR3[31:0] AES_IVR2[31:0] AES_IVR1[31:0] AES_IVR0[31:0]
Nonce[31:0] Nonce[63:32] Nonce[95:64] 32-bit counter = 0x0001
MSv18942V2
Encrypt
AES_KEYRx (KEY)
AES_DINR (ciphertext C1)
AES_DOUTR (plaintext P1)
DATATYPE[1:0]
Swap
management
AES_IVRx
Nonce + 32-bit counter
input
output
Legend
XOR
Swap
management
DATATYPE[1:0]
Encrypt
AES_KEYRx (KEY)
AES_DOUTR (plaintext P2)
DATATYPE[1:0]
Swap
management
AES_IVRx
Nonce + 32-bit counter (+1)
Swap
management
DATATYPE[1:0]
Counter
increment (+1)
AES_DINR (ciphertext C2)
I1
I2
O1 O2
Block 1 Block 2
C1'
C2'
P1'
P2'

 Loading...
Loading...