Embedded Flash memory (FLASH) RM0444
98/1390 RM0444 Rev 5
3.5.5 Disabling core debug access
For executing sensitive code or manipulating sensitive data in securable memory area, the
debug access to the core can temporarily be disabled.
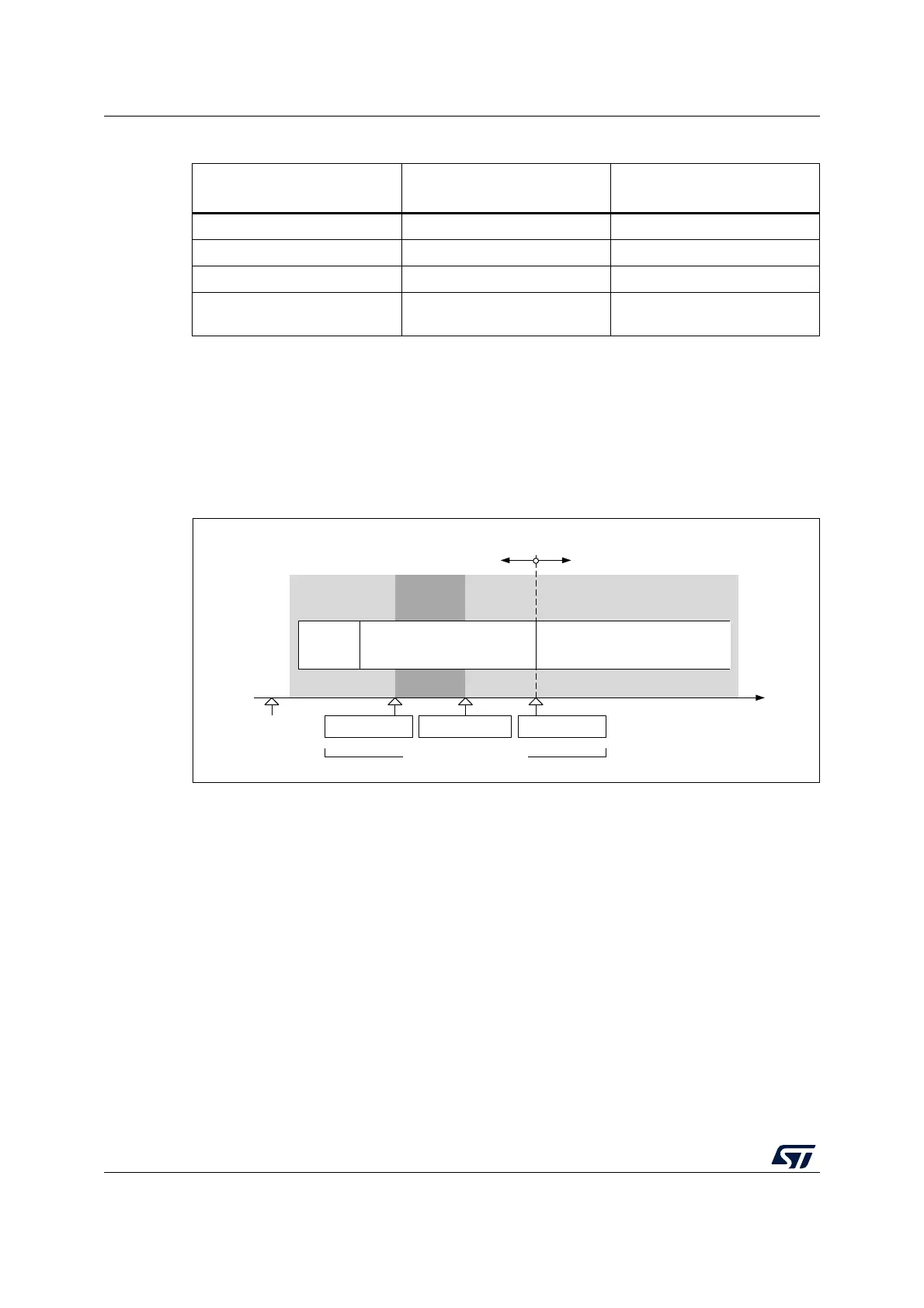
Figure 4 gives an example of managing DBG_SWEN and SEC_PROT (or SEC_PROT2, for
Bank 2 in dual-bank devices) bits.
Figure 4. Example of disabling core debug access
3.5.6 Forcing boot from Flash memory
To increase the security and establish a chain of trust, the BOOT_LOCK option bit of the
FLASH_SECR register allows forcing the system to boot from the Main Flash memory
regardless the other boot options. It is always possible to set the BOOT_LOCK bit.
However, it is possible to reset it only when:
• RDP is set to Level 0, or
• RDP is set to Level 1, while Level 0 is requested and a full mass-erase is performed.
3.6 FLASH interrupts
Table 22. Securable memory erase at RDP Level 1 to Level 0 change
Securable memory size
(SEC_SIZEx[7:0])
PCROP_RDP Erased pages
0 1 All (mass erase)
0 0 All but PCROP
> 0 1 All (mass erase)
> 0 0
All but PCROP outside the
securable memory area
MSv42192V1
timeline
Debug
enabled
Debug
enabled
Debug
disabled
DBG_SWEN = 0 DBG_SWEN = 1 SEC_PROT = 1
Option
byte
loading
Execution of code
within securable memory
Execution of code
outside securable memory
Power up
SEC_PROT = 1
Securable memory secured
SEC_PROT = 0
Securable memory not secured
Software management

 Loading...
Loading...