Page F-10
Appendix F – Network Topology
INTER-TEL
®
AXXESS
®
MANUAL VERSION 11.0 – May 2008
Public (Untrusted) Networks
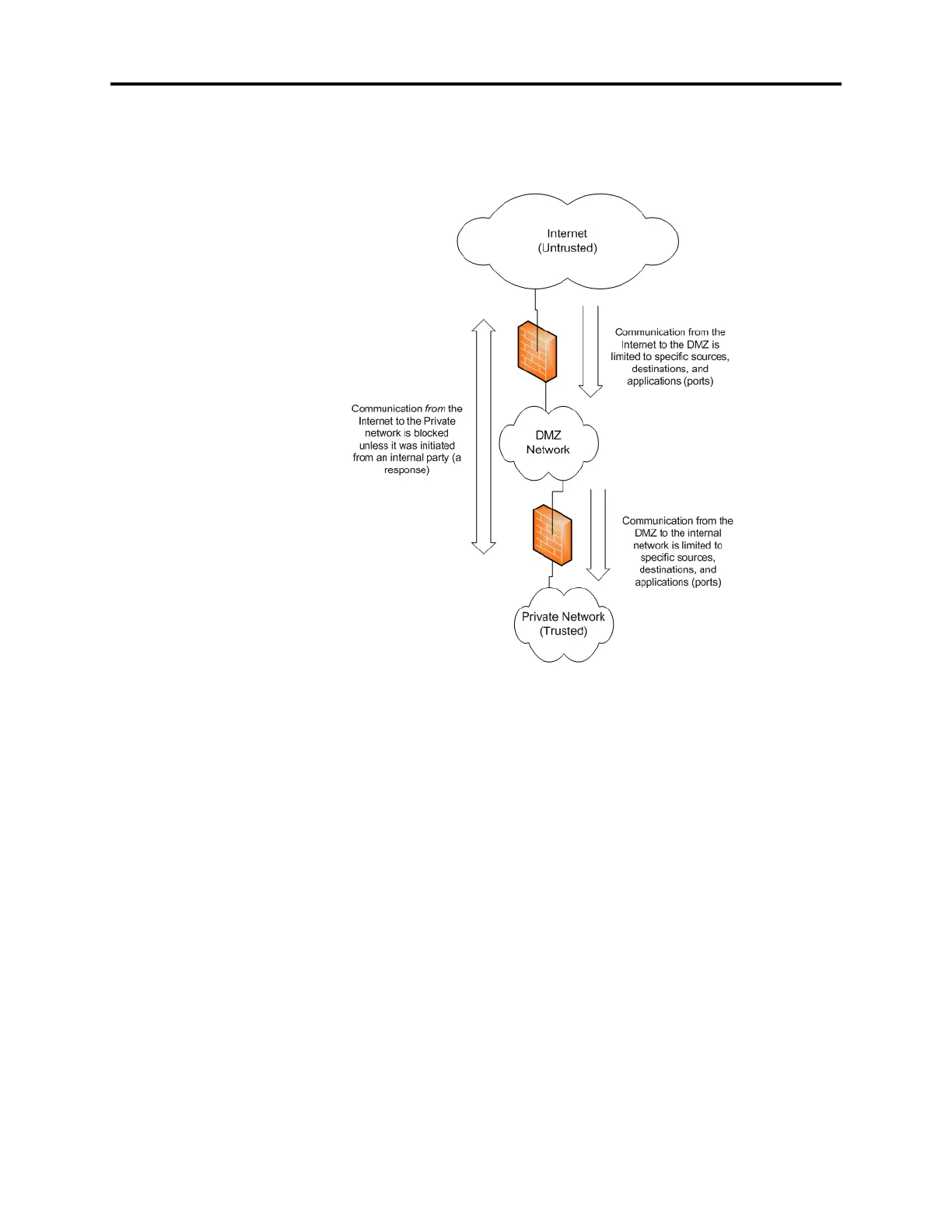
8.3 In some environments, DMZs are implemented in what is referred to as a two-tier archi-
tecture using two firewalls as shown in the following example. In this environment, the DMZ
is between the inside trusted network and the outside untrusted network. The security issues
are still the same, but the configuration is split between the two firewalls.
8.4 In addition to providing protection, firewalls also perform a Network Address Transla-
tion (NAT) function (described in “Terminology” on page F-2) in which private IP addresses
are converted to public IP addresses as packets go out through the firewall. As a general rule,
IP telephony devices do not perform well without special considerations when the communica-
tions must pass through a device performing NAT.
 Loading...
Loading...