Send documentation comments to mdsfeedback-doc@cisco.com
43-15
Cisco MDS 9000 Family Fabric Manager Configuration Guide
OL-17256-03, Cisco MDS NX-OS Release 4.x
Chapter 43 Configuring Certificate Authorities and Digital Certificates
Configuring CAs and Digital Certificates
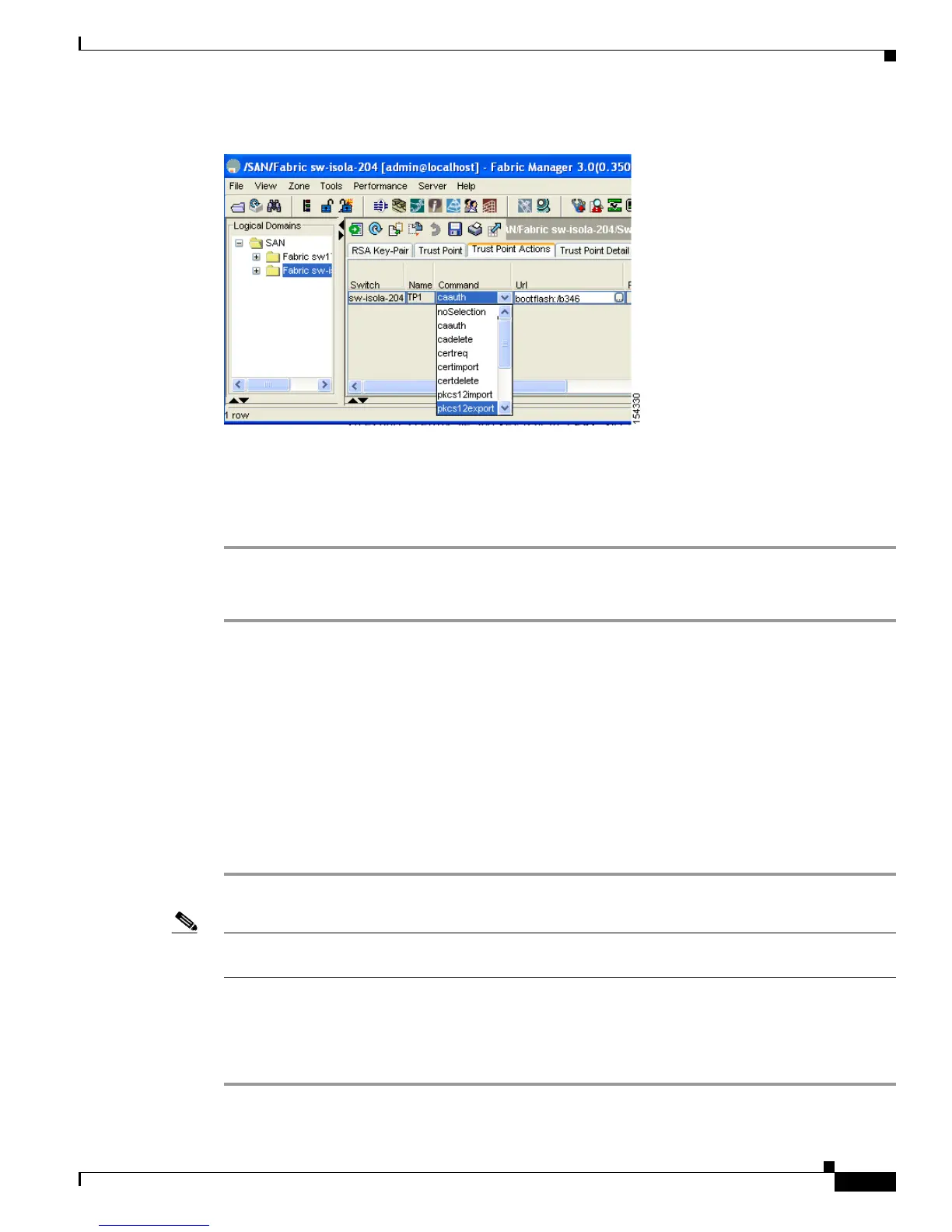
Figure 43-9 Pkcs12export Option Exports a Key-Pair
Step 4 Enter the output file name as bootflash:filename to store the exported PKCS#12 identity.
Step 5 Enter the required password. The password is set for encoding the PKCS#12 data. On successful
completion, the exported data is available in bootflash in the specified file.
Step 6 Click Apply Changes to save the changes.
To import a certificate and key pair formatted as a PKCS#12 formatted file, follow these steps:
Step 1 Expand Switches > Security and then select PKI in the Physical Attributes pane.
Step 2 Click the Trust Point Actions tab in the Information pane (see Figure 43-9).
Step 3 Select the pkcs12import option from the Command drop-down menu to import the key-pair, identity
certificate, and the CA certificate or certificate chain in the PKCS#12 format to the selected trust point.
Step 4 Enter the input in the bootflash:filename format, containing the PKCS#12 identity.
Step 5 Enter the required password. The password is set for decoding the PKCS#12 data. On completion, the
imported data is available in bootflash in the specified file.
Step 6 Click Apply Changes to save the changes.
On completion the trust point is created in the RSA key-pair table corresponding to the imported
key-pair. The certificate information is updated in the trust point.
Note The trust point must be empty (with no RSA key-pair associated with it and no CA is associated with it
using CA authentication) for the PKCS#12 file import to succeed.
Configuring a CRL
To configure the CRL from a file to a trust point using Fabric Manager, follow these steps:
Step 1 Click Switches > Security > PKI in the Physical Attributes pane.

 Loading...
Loading...