Send documentation comments to mdsfeedback-doc@cisco.com
44-29
Cisco MDS 9000 Family Fabric Manager Configuration Guide
OL-17256-03, Cisco MDS NX-OS Release 4.x
Chapter 44 Configuring IPsec Network Security
Crypto IPv4-ACLs
Crypto Map Configuration Guidelines
When configuring crypto map entries, follow these guidelines:
• The sequence number for each crypto map decides the order in which the policies are applied. A
lower sequence number is assigned a higher priority.
• Only one IPv4-ACL is allowed for each crypto map entry (the IPv4-ACL itself can have multiple
permit or deny entries).
• When the tunnel endpoint is the same as the destination address, you can use the auto-peer option
to dynamically configure the peer.
• For IPsec to interoperate effectively with Microsoft iSCSI initiators, specify the TCP protocol and
the local iSCSI TCP port number (default 3260) in the IPv4-ACL. This configuration ensures the
speedy recovery of encrypted iSCSI sessions following disruptions such as Gigabit Ethernet
interfaces shutdowns, VRRP switchovers, and port failures.
Creating Crypto Map Entries
To create mandatory crypto map entries using Fabric Manager, follow these steps:
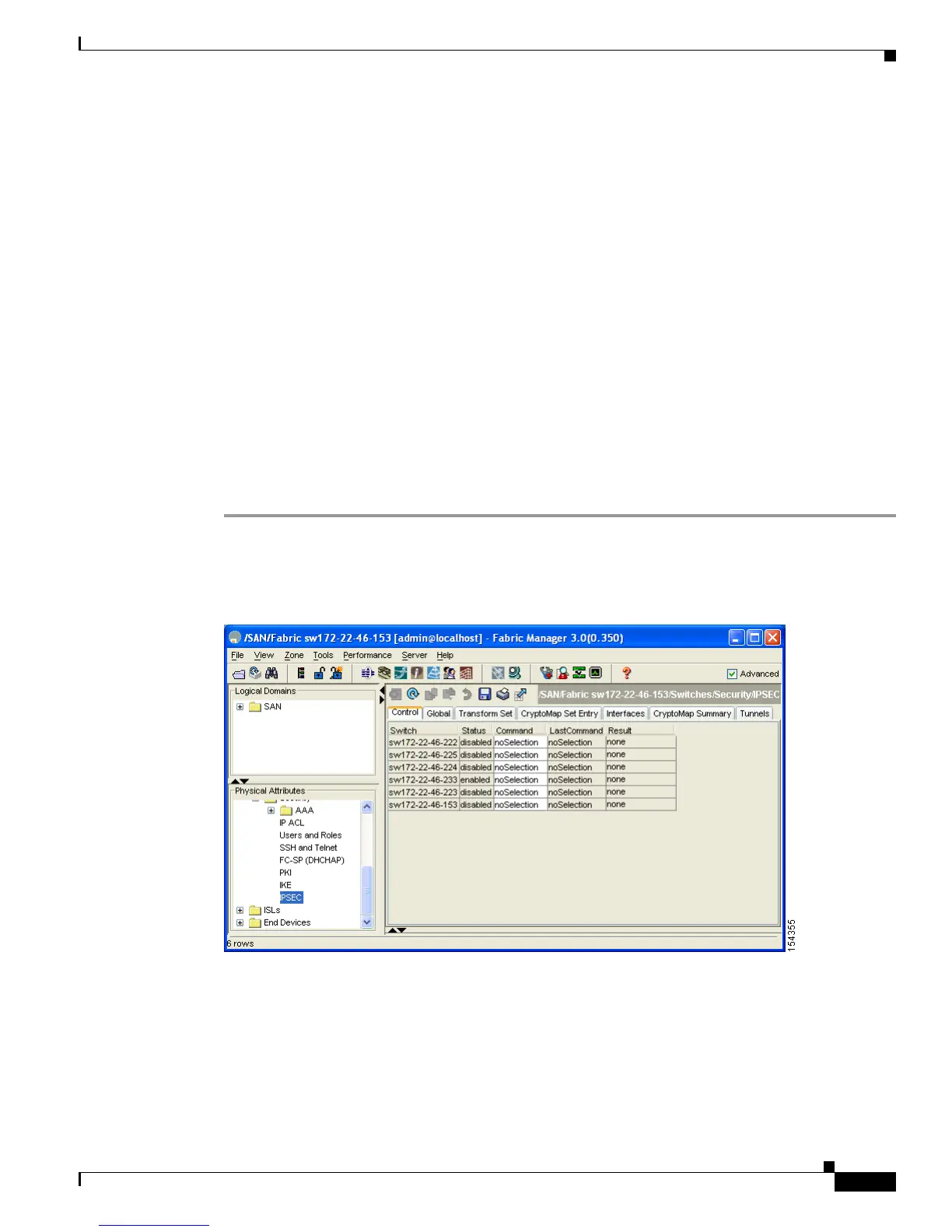
Step 1 Expand Switches > Security and then select IPSEC in the Physical Attributes pane.
You see the IPSec configuration in the Information pane (see Figure 44-21).
Figure 44-21 IPsec Configuration
Step 2 Choose the CryptoMap Set Entry tab.
You see the existing crypto maps configured (see Figure 44-22).

 Loading...
Loading...