BootROMStack
BoottoM0entrypoint
0x0000
0x0002
0x004E
Bootloader Features
www.ti.com
174
SPRUI07–March 2020
Submit Documentation Feedback
Copyright © 2020, Texas Instruments Incorporated
Boot ROM
2.2.4 Watchdog Module
When branching directly to Flash, OTP, or M0 single-access RAM (SARAM) or external interface (XINTF)
the watchdog is not touched. In the other boot modes, the watchdog is disabled before booting and then
re-enabled and cleared before branching to the final destination address.
2.2.5 Taking an ITRAP Interrupt
If an illegal opcode is fetched, the device will take an ITRAP (illegal trap) interrupt. During the boot
process, the interrupt vector used by the ITRAP is within the CPU vector table of the boot ROM. The
ITRAP vector points to an interrupt service routine (ISR) within the boot ROM named ITRAPIsr(). This
interrupt service routine attempts to enable the watchdog and then loops forever until the processor is
reset. This ISR will be used for any ITRAP until the user's application initializes and enables the peripheral
interrupt expansion (PIE) block. Once the PIE is enabled, the ITRAP vector located within the PIE vector
table will be used.
2.2.6 Internal Pullup Circuit
Each GPIO pin has an internal pullup circuit that can be enabled or disabled in software. The pins that are
read by the boot mode selection code to determine the boot mode selection have pull-ups enabled after
reset by default. In noisy conditions it is still recommended to configure each of the boot mode selection
pins externally.
The peripheral bootloaders all enable the pullup circuit for the pins that are used for control and data
transfer. The bootloader leaves the circuit enabled for these pins when it exits. For example, the SCI-A
bootloader enables the pullup circuit on the SCITXA and SCIRXA pins. It is the user's responsibility to
disable them, if desired, after the bootloader exits.
2.2.7 PIE Configuration
The boot modes do not enable the PIE. It is left in its default state, which is disabled.
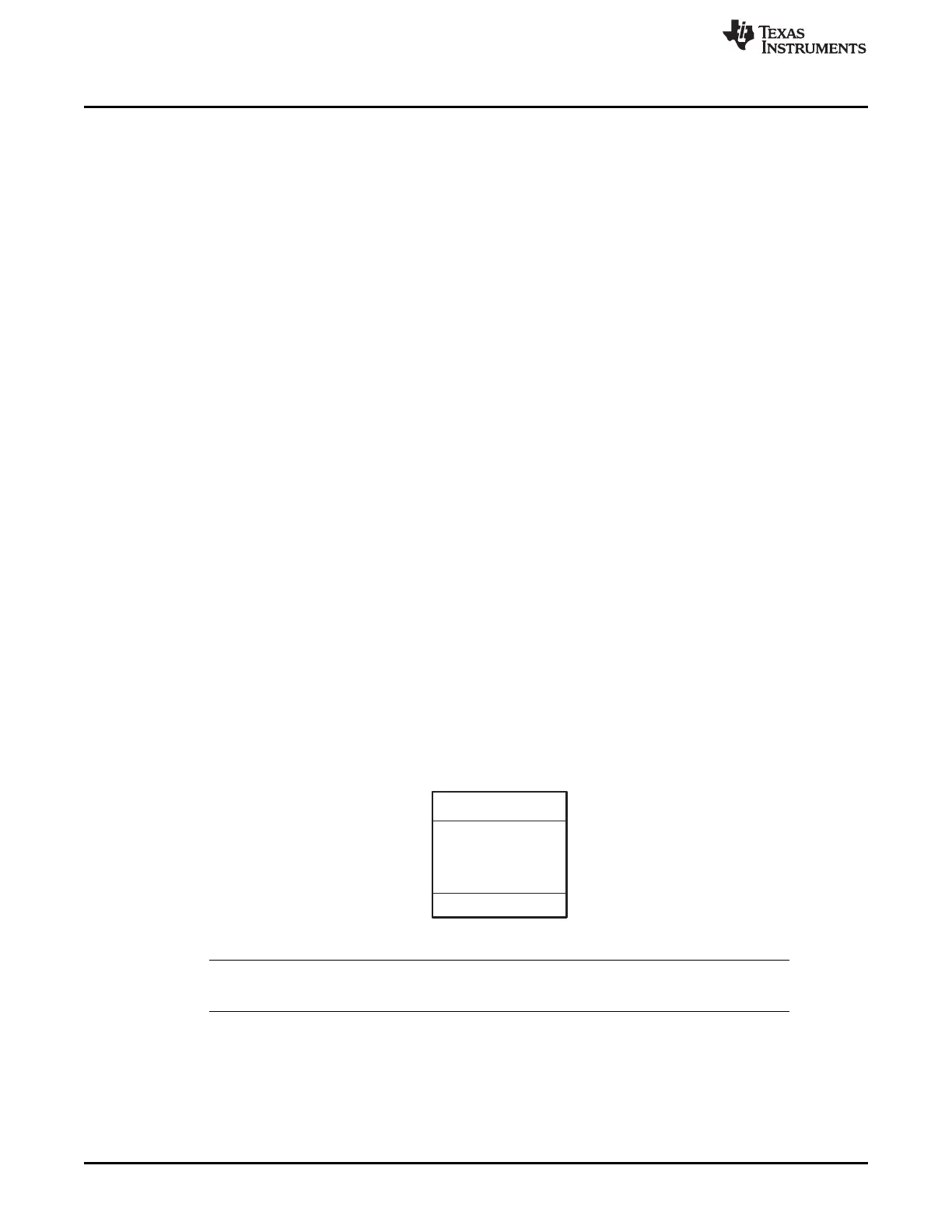
2.2.8 Reserved Memory
The M0 memory block address range 0x0002 - 0x004E is reserved for the stack and .ebss code sections
during the boot-load process. If code is bootloaded into this region there is no error checking to prevent it
from corrupting the boot ROM stack. Address 0x0000-0x0001 is the boot to M0 entry point. This should be
loaded with a branch instruction to the start of the main application when using "boot to SARAM" mode.
Figure 2-4. Boot ROM Stack
Boot ROM loaders on older C28x devices had the stack in M1 memory. This is a change for this boot loader.
NOTE: If code or data is bootloaded into the address range address range 0x0002 - 0x004E, there
is no error checking to prevent it from corrupting the boot ROM stack.

 Loading...
Loading...